Bl00dy Ransomware Gang Exploiting Printer Vulnerability to Attack Schools

A joint Cybersecurity Advisory (CSA) from the FBI and CISA absorb been published on actively exploiting the vulnerability in some versions of PaperCut NG and PaperCut MF, identified as CVE-2023-27350.
This makes it doable for an unauthenticated actor to attain malicious code remotely. In March 2023, PaperCut made a fix on hand.
The Bl00dy Ransomware Gang tried to make use of weak PaperCut servers to attack the Education sector.
“In early Could perhaps 2023, per FBI recordsdata, the Bl00dy Ransomware Gang received entry to sufferer networks all around the Education Services Subsector the put apart PaperCut servers weak to CVE-2023-27350 had been uncovered to the net,” reads the safety advisory.
“By some means, a couple of these operations ended in recordsdata exfiltration and encryption of sufferer methods.”
The vulnerability has been actively exploited since now not decrease than April 18, 2023, roughly a month after being made public in March.
Though the suppose has been mounted in PaperCut NG and MF versions 20.1.7, 21.2.11, and 22.0.9, organizations absorb hesitated to practice the upgrade, leaving themselves birth to attacks.
Reports point out that this severe-severity a ways off code execution (RCE) vulnerability affects PaperCut MF and PaperCut NG, the printer management plot weak by practically 70,000 organizations in over 100 countries.
“PaperCut servers weak to CVE-2023-27350 put in power terrifying entry controls in the SetupCompleted Java class, permitting malicious actors to avoid client authentication and entry the server as an administrator. After accessing the server, actors can leverage existing PaperCut plot aspects for a ways off code execution (RCE)”, CISA reports.
Attack by the Bl00dy Ransomware Gang on the Education Sector
About 68% of the PaperCut servers accessible via the net, per CISA, are in the Education Services subsector. However it’s peaceful unclear how many weak endpoints are unpatched.
Utilizing CVE-2023-27350 to avoid client authentication and find administrator entry to the machine, the Bl00dy ransomware attacks which absorb been lately seen had been a hit against a couple of targets in the industry.
This entry used to be then weak to generate additional ‘cmd.exe’ and ‘powershell.exe’ processes with the identical high privileges to fetch a ways off entry to the plot and use it as a launchpad to spice up laterally via the community.
The ransomware perpetrators take recordsdata and encrypt the plan methods one day of this time, then shuffle away notes soliciting for price in replace for a working decryptor and a pledge to now not section or promote the stolen deliver.
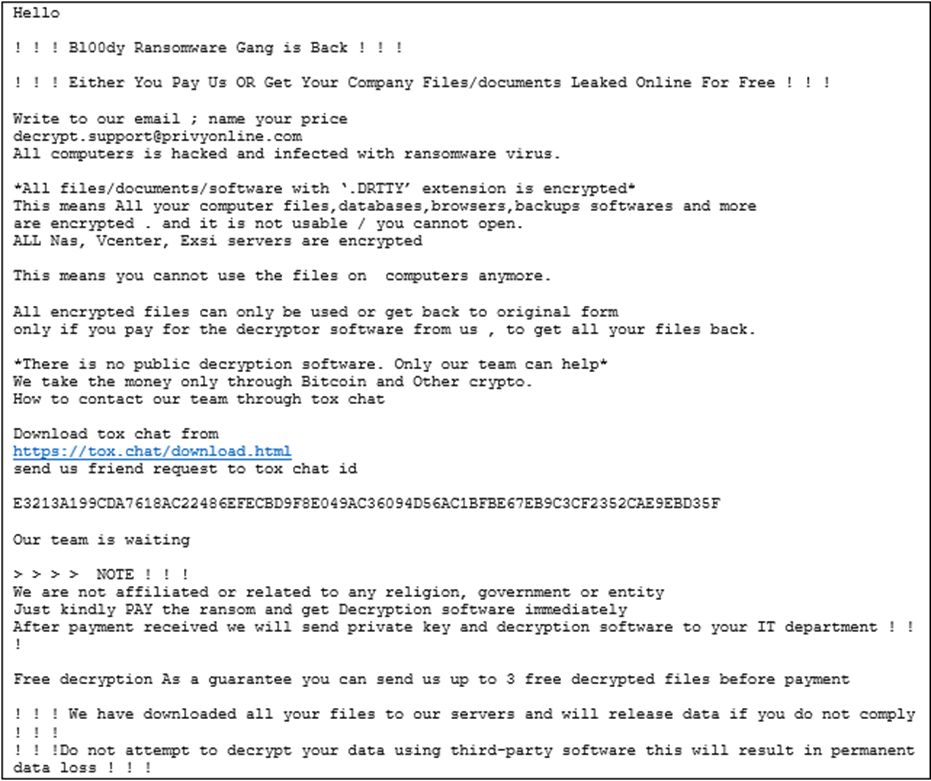
“The Bl00dy Ransomware Gang left ransom notes on sufferer methods annoying price in replace for the decryption of encrypted recordsdata”, says the document.
Notably, legit a ways off management and repairs (RMM) plot, per FBI study, used to be downloaded and flee on sufferer methods the usage of commands sent thru PaperCut’s print scripting interface.
Bl00dy Gang ransomware actors would possibly well perhaps veil their malicious community web deliver traffic by speaking with assorted networks thru Tor and/or assorted proxies internal sufferer networks.
The FBI also chanced on evidence of the download and use of repeat and revel in watch over (C2) malware, along side DiceLoader, TrueBot, and Cobalt Strike Beacons. Alternatively, It is unknown when these instruments had been weak in the attack.
Therefore, customers and administrators are knowledgeable by the FBI and CISA to straight away deploy fixes and make use of workarounds if that’s now not doable.
Struggling to Apply The Security Patch in Your Design? –
Try All-in-One Patch Supervisor Plus
Source credit : cybersecuritynews.com


