CISA & FBI Released Guide to Respond for DDoS Attacks

The Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the Federal Bureau of Investigation (FBI) and the Multi-Suppose Info Sharing and Analysis Heart (MS-ISAC), has launched a comprehensive e book.
It geared toward assisting federal, disclose, native, tribal, and territorial govt entities in responding to Distributed Denial-of-Service (DDoS) assaults.

Determining the Menace Landscape
DDoS assaults form from extra than one sources and could presumably still be in particular worthy to impress and block.
The e book provides an in-depth overview of the DoS and DDoS landscapes, detailing assault kinds, motivations, and attainable impacts on govt operations.
It emphasizes the importance of planning for emerging DDoS trends and technologies to larger defend against malicious exercise.
CISA and FBI haven’t any longer too prolonged ago launched a comprehensive e book that offers technical info and most productive practices to reply successfully to Distributed Denial of Service (DDoS) assaults.
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security groups have to triage 100s of vulnerabilities. :
- The downside of vulnerability fatigue this day
- Distinction between CVSS-specific vulnerability vs possibility-essentially based mostly vulnerability
- Evaluating vulnerabilities in response to the enterprise affect/possibility
- Automation to within the reduction of alert fatigue and provides a rob to security posture vastly
AcuRisQ, which lets you quantify possibility accurately:
DoS vs. DDoS: What’s the Distinction?
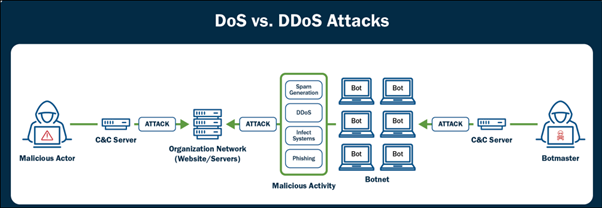
The e book clarifies the distinction between DoS and DDoS assaults.
A DoS assault on the total entails a single source overwhelming a system with traffic, while a DDoS assault makes spend of extra than one sources, in most cases coordinated by botnets, to lengthen the disruption.
The disbursed nature of DDoS assaults makes them extra worthy to defend against.
CISA Cyber no longer too prolonged ago tweeted about the release of a e book by CISA and FBI that offers detailed knowledge on how to reply to DDoS assaults
Categorizing DDoS Attacks
DDoS assaults are labeled into three predominant kinds:
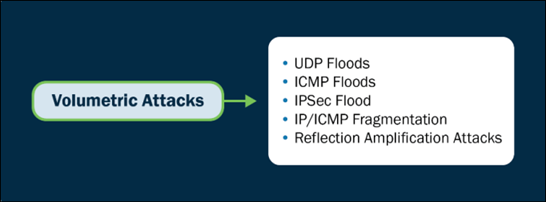
- Volume-Primarily based entirely Attacks: These aim to spend bandwidth or system sources by overwhelming the purpose with huge traffic.
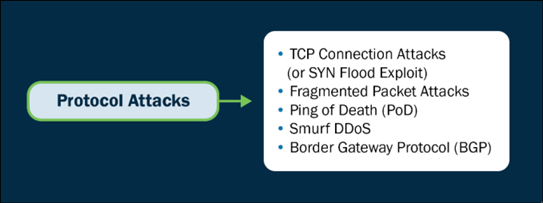
- Protocol-Primarily based entirely Attacks: These exploit community protocol vulnerabilities to degrade performance or trigger malfunctions, in most cases concentrated on Layers 3 and 4 of the OSI model.
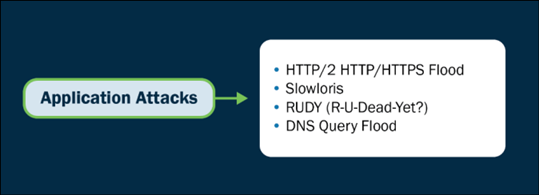
- Utility Layer-Primarily based entirely Attacks: These assault specific capabilities or services, exploiting weaknesses to spend processing vitality or trigger malfunctions. They level of curiosity on Layer 7 of the OSI model.
Proactive Steps In opposition to DDoS Attacks
The e book outlines several proactive measures organizations can rob to within the reduction of the attainable injury of a DDoS assault:
- Conducting possibility assessments
- Implementing worthy community monitoring
- Examining traffic to attach a baseline
- Integrating Captcha challenges
- Rising a comprehensive incident response belief
- Utilizing DDoS mitigation services
- Planning for bandwidth skill
- Implementing load-balancing alternatives
- Configuring firewalls and updating programs
- Ensuring redundancy and failover mechanisms
- Coaching employees on cybersecurity consciousness
Figuring out a DDoS Assault
Recognizing a DDoS assault shall be worthy.
The e book lists signs equivalent to web plot unavailability, community congestion, odd traffic patterns, server crashes, excessive handy resource utilization, and communication disruptions as attainable indicators of an ongoing assault.

Responding to a DDoS Incident
When an assault is known, organizations are told to:
- Set off their incident response belief
- Inform provider providers
- Buy proof
- Put in force traffic filtering
- Enable DDoS mitigation services
- Scale up bandwidth and sources
- Insist CDN services
- Withhold obvious communication with stakeholders
- Learn from the assault to present a rob to future responses
Restoration and Reporting
Post-assault, organizations could presumably still assess the affect, restore services, designate a post-incident diagnosis, put into effect remediation measures, overview security controls, update incident response plans, educate employees, give a rob to community monitoring, have interaction with legislation enforcement, and preserve clear communication with stakeholders.
The joint e book launched by CISA, FBI, and MS-ISAC is a well-known handy resource for presidency agencies and organizations.
It provides them with the well-known instruments and data to successfully reply to and recover from DDoS assaults, making sure the resilience and security of their operations within the face of evolving cyber threats.
Defend updated on Cybersecurity news, Whitepapers, and Infographics. Prepare us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


