Cisco IMC Command Injection Vulnerability Under Active Attack

An attacker with learn-only or better privileges on a Cisco Integrated Administration Controller (IMC) can exploit a repeat injection vulnerability (CVE-2024-20295) to kind elephantine regulate (root gain entry to) of the underlying operating system.
The vulnerability exists due to insufficient validation of client-equipped enter on the IMC CLI and there are now not any workarounds readily accessible, but tool updates to address this serious say gain been released.

A Cisco Integrated Administration Controller (IMC) vulnerability permits authenticated native attackers with learn-only privileges or better to escalate privileges to root, which encompass functions admire wireless controllers, APIC servers, Industrial Edition dwelling equipment, Catalyst Heart dwelling equipment, and more.
The vulnerabilities that affected Cisco products encompass 5000 Sequence ENCS, Catalyst 8300 Sequence Edge uCPE, UCS C-Sequence and E-Sequence Servers, and heaps of Cisco dwelling equipment basically basically based on preconfigured UCS C-SeriesḤ̣Ḥ Servers.
UCS B-Sequence Blade Servers, UCS C-Sequence Rack Servers below Cisco UCS Manager management, UCS S-Sequence Storage Servers, and UCS X-Sequence Modular Systems originate now now not make stronger Cisco IMC, which reduces the functionality attack surface on these platforms. Cisco has now now not known any vulnerabilities in these products.
Cisco has released tool updates to repair a now now not too long previously learned vulnerability, which are readily accessible with out spending a dime to customers with provider contracts that encompass tool updates.
Customers may per chance gain to peaceable update their tool as soon as doubtless if they’ve a Cisco product that’s at possibility of this vulnerability and consider that they’ll only set up and keep a query to make stronger for tool variations that they’ve a license for.

To upgrade Cisco tool, customers will must gain a sound license acquired straight a long way from Cisco or a accomplice, as upgrades are in most cases maintenance updates to reward tool and free security updates won’t grant contemporary licenses or essential upgrades.
Sooner than upgrading, customers may per chance gain to peaceable compare Cisco Safety Advisories for identified considerations and choices and they wish to peaceable guarantee their devices gain sufficient reminiscence and compatibility with the contemporary tool.
The advisory addresses a vulnerability in Cisco tool and customers who’re now now not lined by a Cisco provider contract or are unable to kind a repair via their vendor may per chance gain to peaceable contact Cisco TAC for a free upgrade.
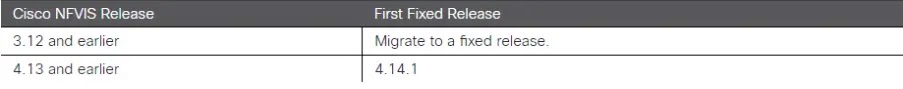
It moreover entails a desk that lists affected tool variations and the corresponding fixed releases.
For Cisco 5000 Sequence ENCS and Catalyst 8300 Sequence Edge uCPE, upgrading Cisco IMC requires upgrading the Cisco NFVIS tool first and the IMC shall be upgraded automatically throughout the NFVIS firmware upgrade course of.
Particulars referring to the Cisco IMC tool vulnerability and its fixes for Cisco UCS C-Sequence and E-Sequence servers are categorized by M-Sequence variations (M4, M5, M6, M7) and E-Sequence variations (M2, M3, M6).
It is miles instructed that Cisco IMC be upgraded to particular fixed releases basically basically based on the server mannequin, and there are exceptions where particular firmware update packages or hotfixes are required for definite Cisco dwelling equipment.
Source credit : cybersecuritynews.com


