5 Common Phishing Vectors and Examples – 2024
5 Well-liked Phishing Vectors and Examples – 2024
Phishing assaults shall be performed thru diverse intention, equivalent to SMS and phone calls, however the most prevalent system involves sending victims emails containing malicious attachments.
These would maybe well also advance in diverse forms, but they most regularly belong to 1 of the following classes: executable recordsdata, office documents, archives, PDFs, or links.
Let’s rob a nearer witness at these forms and survey examples of fresh phishing assaults that spend such malware provide suggestions.
1. Executable Files
The relate of an executable electronic mail attachment is the most classic, yet the most apparent system of conducting a phishing assault. A bare malicious .exe file no longer handiest raises an scare in the particular person that comes all over it, but additionally is seemingly to trigger a security machine.
To originate executables reasonably much less suspicious, menace actors would maybe well also conceal them as legitimate documents, photos, or tool updates, the usage of innocuous-sounding names like âA financial document” or âinvoiceâ.
Most regularly, these recordsdata advance with corresponding emails that seem like from a respected source, like a financial institution or a tool seller.
Attackers would maybe well also employ quite quite lots of executable forms to trick a seemingly victim with out ample computer records into opening them. These encompass .msi, .dll, and .scr recordsdata, which, despite the usage of a range of extensions, purpose similarly to .exe ones.
Instance:
Letâs analyze a sample of a phishing executable in a sandbox. In this case, we are in a position to ogle how the AgentTesla malware is delivered on the machine thru an .exe file disguised as a PDF one.
It has a unsuitable identify âBANK SWIFT.pdf____â, which will be ample to confuse a seemingly victim and safe them to speed it.
2. Utter of industrial Documents
The next identical previous form of phishing assault involves distributing Word, Excel, PowerPoint documents with embedded malicious macros, scripts, or exploits.
As soon as opened, the malicious instruct within the file is performed, regularly main to the set up of malware or the theft of honest records.
Instance:
In this case, sandbox prognosis finds the usage of the CVE-2017-11882, a vulnerability that enables attackers to invent malicious code by exploiting a flaw in Microsoft Equation Editor.
By opening the contaminated Excel file, the victim triggers the execution chain, which indirectly outcomes in the infection with AgentTesla.
3. Archives
Archiving in phishing assaults is mostly frail as a identical previous intention of evading detection.
Putting malware within a .ZIP, .RAR, or any other archive structure file permits menace actors to avoid security solutions which will no longer scan compressed recordsdata as thoroughly as uncompressed ones.
Criminals would maybe well also relate diverse compression formats, encryption, or password safety to originate it extra complicated for security researchers and automatic instruments to examine the contents of the archive.
By hiding the malicious payload within an archive, the malware has a greater likelihood of efficiently infiltrating the target machine.
Instance:
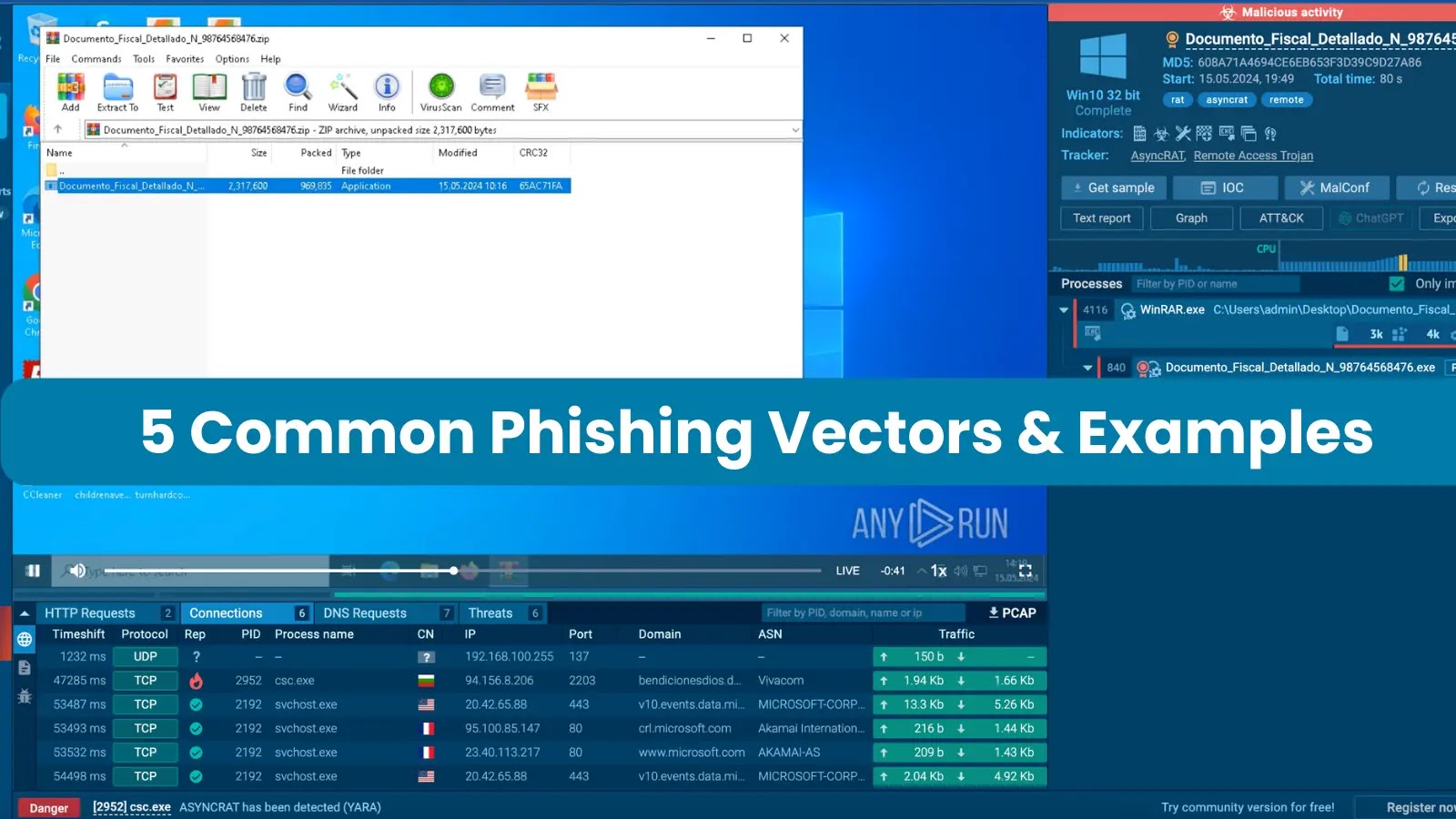
In this Attack, the sandbox lets us safely analyze and detonate an archive containing a malicious executable.
Spy how the archive and the file it comprises are named âDocumento_Fiscal_Detalladoâ, which as soon as extra shows how attackers relate legitimate sounding names to fool victims.
We can contemplate about how, the machine gets contaminated with AsyncRAT after launching the archived executable.
4. PDFs
The main system of the usage of PDFs in phishing is by embedding them with a malicious hyperlink. These links are in total crafted to undergo a resemblance to legitimate documents.
By clicking on the hyperlink within the PDF, customers trigger the following assault stage, that would maybe well also be pleased stealing their login credentials, personal records, or indirectly concluding with malware being dropped on their machine.
Instance:
Right here is an instance of a PDF file containing a phishing hyperlink. On this case, by clicking on this hyperlink, the user downloads an archive, which comprises a malicious executable. The final stage of the assault is the deployment of the DBatLoader that proceeds to fall its payloads.
5. URLs
At final, an especially frequent phishing system depends on malicious links sent as portion of emails. To originate these URLs seem extra proper, cybercriminals regularly relate URL shortening, typosquatting, or homograph assaults to procure malicious links.
After clicking on it, the victim gets redirected to a unsuitable web page which will hold their login credentials, personal records, or safe them to download malware and invent it.
Instance:
This sandbox session shows a popular phishing assault that makes an attempt to trick customers into entering their password on a unsuitable MS Outlook page. Attackers are also abusing the legitimate IPFS.io carrier to host their page to originate it seem extra real.
Analyze Phishing in ANY.RUN
ANY.RUN’s cloud-primarily based sandbox is ultimate for analyzing phishing assaults, with fully-interactive Windows and Linux VM environments.
Have interaction with uploaded recordsdata and URLs to impress the assault, make all wanted investigation activities, and form an intensive look of community traffic, registry adjustments, active processes, TTPs, and further.
Source credit : cybersecuritynews.com