Copybara Uses On-Device Fraud to Steal Funds Directly from the Victim's Device

Cybersecurity consultants at Cleafy Labs accept as true with exposed a flowery fraud campaign orchestrated by a neighborhood identified as Copybara.
This campaign, leveraging on-instrument fraud ways, has been meticulously designed to siphon funds straight from victims’ units, marking a serious escalation within the severity and class of cyber threats going by folks and institutions alike.

Cleafy Labs detailed the Copybara campaign, which employs a multifaceted advance to infiltrate and exploit victims’ units.
Unlike in vogue fraud solutions that rely on intercepting or redirecting communications between a user and their monetary establishment, on-instrument fraud occurs straight throughout the compromised instrument.
This vogue enables attackers to avoid many of the protection measures that banks and other monetary companies accept as true with place in self-discipline, making it a namely insidious fabricate of cybercrime.
Are you from SOC and DFIR groups? – Be part of With 400,000 self sustaining Researchers
Malware diagnosis could per chance even be fleet and straight forward. Right allow us to remark you the capacity to:
- Contain interplay with malware safely
- Dwelling up virtual machine in Linux and all Windows OS variations
- Work in a crew
- Salvage detailed studies with most info
While you discontinuance up attempting to test all these parts now with fully free accumulate admission to to the sandbox: ..
Copybara Makes use of On-Instrument Fraud to Grab Funds
At the center of the Capybara campaign is malicious instrument, or malware, that is cleverly disguised within apparently innocuous capabilities.
Once place in on a victim’s instrument, this malware grants the attackers extraordinary accumulate admission to to the instrument’s capabilities and info, reads Cleafy Labs file.
This contains intercepting and manipulating SMS messages and push notifications, most ceaselessly worn as fragment of two-say authentication processes.
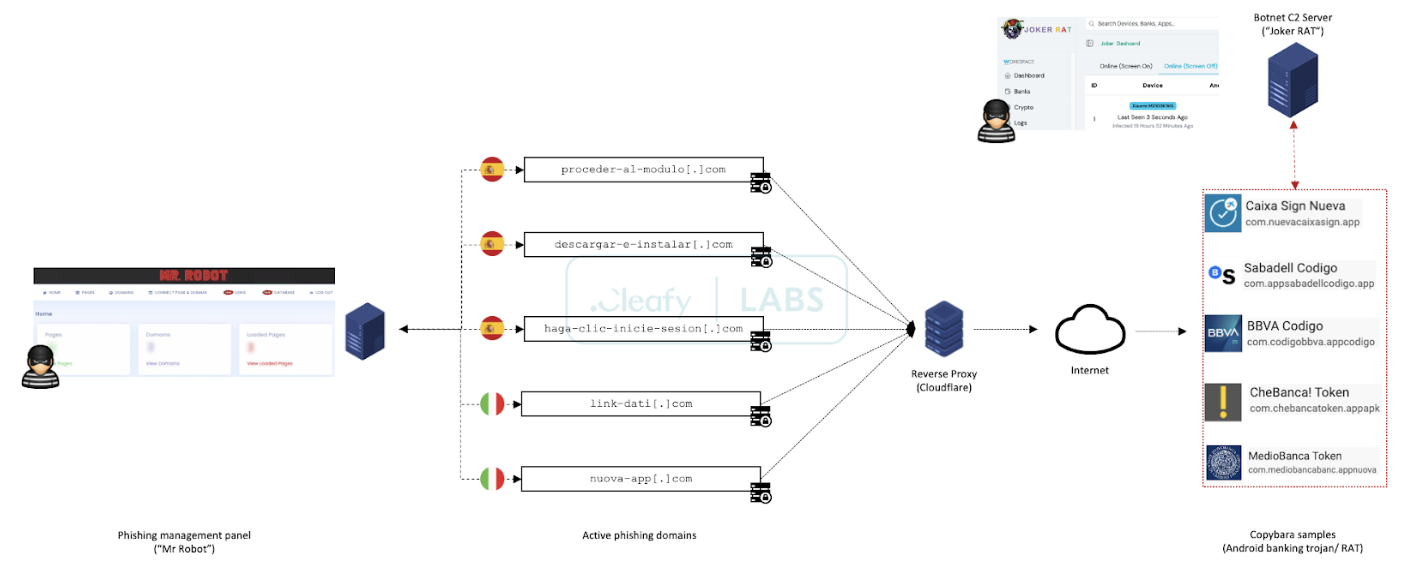
The sophistication of the Copybara malware lies in its skill to stay undetected while actively monitoring the instrument for particular actions, equivalent to gaining access to banking capabilities or web sites.
The malware springs into action upon detecting such actions, surreptitiously redirecting the user’s inputs to the attackers’ servers.
This allows the perpetrators to capture sensitive info, equivalent to login credentials and monetary info, without the victim’s info.
In all chance most alarmingly, the Copybara campaign demonstrates high customization and adaptability.
The attackers accept as true with proven the flexibility to tailor their malware to focus on particular monetary institutions and apps, increasing the likelihood of a hit fraud.
This stage of specificity, mixed with the malware’s stealthy operation, poses a serious self-discipline to present cybersecurity measures.
According to the rising risk posed by on-instrument fraud, cybersecurity consultants, including these at Cleafy Labs, are calling for elevated vigilance and the adoption of more evolved safety measures.
This contains the use of behavior-essentially based fully detection systems that can title and neutralize malicious actions on a instrument earlier than any injure could per chance even be done
As the Copybara campaign continues to adapt, it serves as a stark reminder of the ever-show and ever-changing nature of cyber threats.
Participants and institutions alike must remain proactive of their cybersecurity efforts, continuously updating and refining their defenses to provide protection to in opposition to those delicate and extremely targeted attacks.
With Perimeter81 malware protection, you need to to perhaps presumably block malware, including Trojans, ransomware, spyware and adware, rootkits, worms, and nil-day exploits. All are incredibly tainted and could per chance perhaps presumably wreak havoc for your network.
Cease as much as this point on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


