COSMICENERGY – New OT Malware Causes Electric Power Disruption

A Russian govt-linked malware concentrated on energy transmission became once chanced on lately by researchers at Mandiant at some stage in be taught, suggesting its doable employ in training workout routines for cyberattacks on electrical grids.
The malware COSMICENERGY, named by Google’s menace intelligence company Mandiant, became once uploaded to VirusTotal in December 2021 from Russia, however no proof suggests its staunch deployment.
This malware explicitly targets IEC-104 gadgets cherish RTUs aged in electrical transmission and distribution operations, potentially leading to energy disruptions in varied areas cherish:-
- Europe
- The Heart East
- Asia
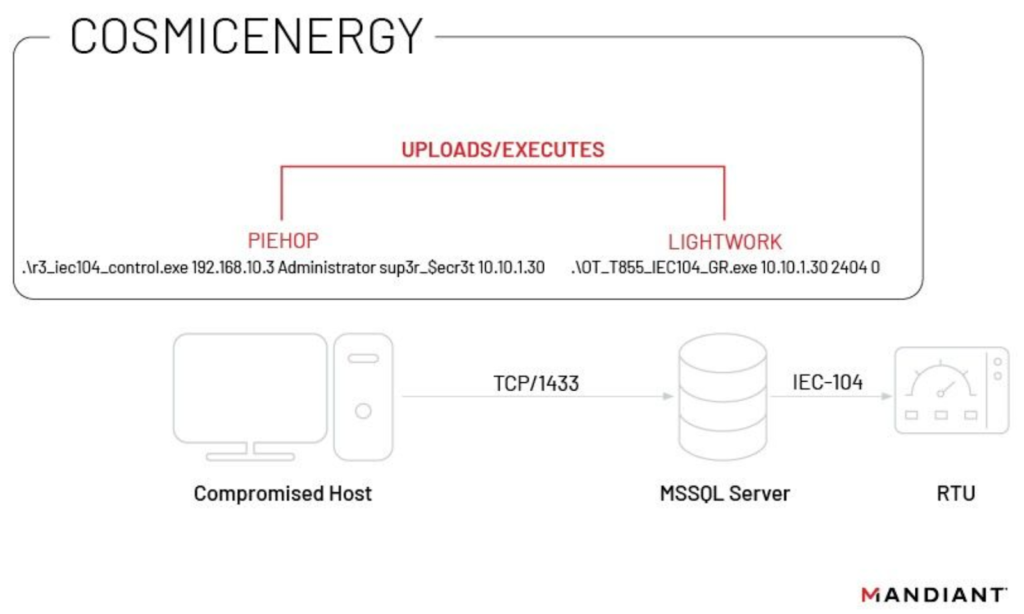
COSMICENERGY Diagnosis
COSMICENERGY is a determined instrument developed by a contractor for energy disruption workout routines. It resembles malware cherish INDUSTROYER and INDUSTROYER.V2, aged to impress electricity transmission via IEC-104.
This malware reveals that rising offensive OT capabilities is popping into more uncomplicated as attackers be taught from outdated assaults. It poses a proper menace to electrical grid property, so house owners would possibly maybe well aloof act to stop its deployment.
While it also resembles the 2016 INDUSTROYER incident, the utilization of IEC-104 instructions and presumably an MSSQL server to derive admission to OT. COSMICENERGY permits some distance off management of energy line switches and circuit breakers for disruption via its ingredients:-
- PIEHOP
- LIGHTWORK
That you would factor in Affiliation with the Russian Authorities
Within the evaluation of COSMICENERGY, a code whine linked it to the “Solar Polygon” project.
The researchers chanced on a match to a cyber vary developed by Rostelecom-Solar, a Russian firm conducting energy disruption workout routines.
The muse and motive of COSMICENERGY stay unclear. Presumably developed by Rostelecom-Solar or an associated social gathering for simulated energy grid assaults.
They’re potentially aged in workout routines cherish Rostelecom-Solar’s collaboration with the Russian Ministry of Energy in 2021 or SPIEF in 2022.

The dearth of proof makes it possible that one other actor reused the cyber vary code to derive this malware.
Possibility actors in most cases repurpose crimson team instruments for proper-world assaults, cherish TEMP.[]Veles is the utilization of METERPRETER in the TRITON attack.
Similarities with Reward OT Malware
Right here below, now we own talked about the whole key similarities with the sleek OT malware:-
- Abuse of timid by derive protocols
- Assert of originate-provide libraries for protocol implementation
- Assert of Python for malware pattern and/or packaging
COSMICENERGY’s capabilities align with outdated OT malware; its discovery finds vital traits in OT threats.
Contemporary OT malware poses a real away menace attributable to rare discoveries and reliance on timid OT ingredients which is possible to be no longer possible to be mounted soon.
Discovery of COSMICENERGY signifies lower obstacles for offensive OT threats, presumably attributable to crimson team involvement.
Usually, such capabilities own been exiguous to successfully-resourced or command-backed actors.
On the identical time, the contractors and crimson team instruments are incessantly aged by menace actors in proper-world OT assaults.
Discovery Methods
Right here below, now we own talked about the whole discovery programs that Mandiant researchers present:-
- In discovering and aggregate host-based mostly entirely logs for serious systems cherish HMI, EWS, and OPC servers.
- Overview logs for Python script or unauthorized code execution proof.
- Name and investigate unauthorized Python executables on OT systems or systems with OT derive admission to.
- Video display systems with OT derive admission to to derive wanted recordsdata, artifacts, and libraries as proof of executing Python scripts.
- Video display MSSQL Servers for OT procedure and community derive admission to.
- Stare reconnaissance and enumeration inform, unauthorized community connections (TCP/1433), irregular/authenticated utilization, and SQL extended saved procedures enabling Windows shell teach execution.
Source credit : cybersecuritynews.com


