Critical Vulnerability in WordPress Stripe Payment Plugin Exposes Customer Data

The WordPress Stripe Cost Gateway plugin has been inclined to Unauthenticated Afraid Dispute Object Reference (IDOR) Vulnerability. WooCommerce developed this plugin.
The plugin model is 7.4.1 and has almost about 900K installations worldwide. On the total, funds are redirected to externally hosted checkout pages where the checkout and payment process occurs.
The exhaust of this plugin is to create customers preserve on the wordpress self-discipline within the course of the payment.
CVE-2023-34000: IDOR vulnerability in WooCommerce Stripe Cost Gateway plugin
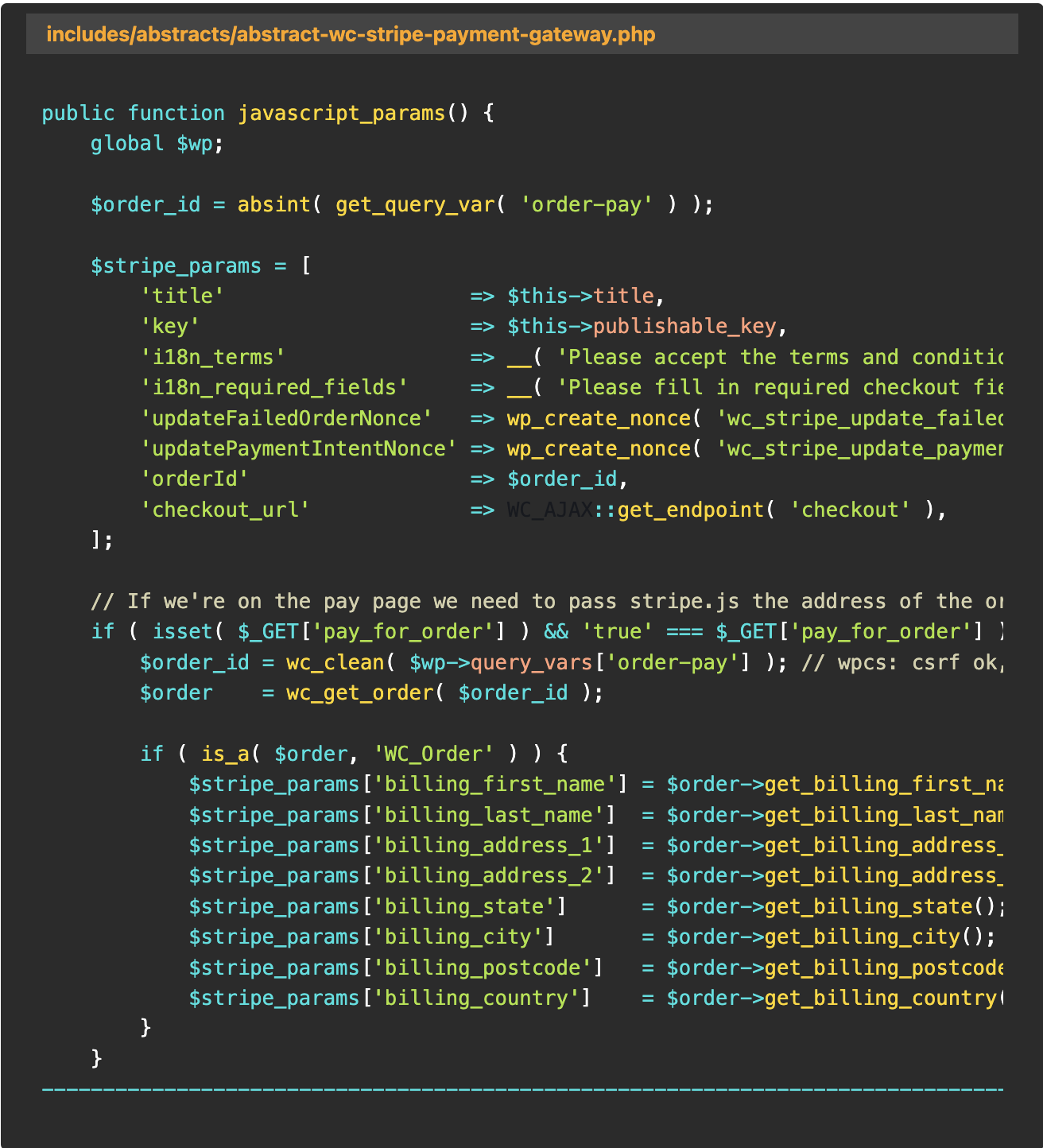
A risk actor can exploit the javascript_params and payment_fields feature to retrieve sensitive recordsdata from the database, including For my half Identifiable Files (PII), email addresses, shipping addresses, and the person’s elephantine identify reported PathStack.
Publicity of the above recordsdata is assumed to be severe and could perchance lead to more attacks, comparable to rip-off emails that strive to take over accounts and grab credentials.
Affected Products
WooCommerce Stripe Gateway Plugin model 7.4.0 and below
Fastened in Model
WooCommerce Stripe Gateway Plugin model 7.4.1
Vulnerability Shrimp print
The plugin’s ‘javascript_params’ and ‘payment_fields’ functions are prone attributable to spoiled articulate object handling and a lack of glean admission to alter mechanisms.
Attributable to these flaws within the code, any WooCommerce articulate recordsdata could perchance also even be viewed by an unauthorized third celebration with out first verifying the legitimacy of the question or the rightful owner of the articulate.
Statistics compiled by WordPress.org present that bigger than half of of all active plugin installations exhaust a prone model.
The mandatory updates to take care of this flaw private been made available within the market by WooCommerce. Customers are informed to pork up to model 7.4.1, which addresses this flaw.
Source credit : cybersecuritynews.com


