Cybercriminals Use Fake Blue Screen of Death (BSOD) Message to Trick Victims
Cyble Analysis and Intelligence Labs no longer too long within the past uncovered a fake grownup web express that is designed to trick unsuspecting users into visiting it. As soon as a user visits this grownup living, a sinful executable file is routinely downloaded onto their tool, striking their privateness and safety at possibility.
The malicious executable file in set up a matter to has been cleverly disguised to seem at bask in a harmless video file. This became as soon as completed by the usage of the icon of the customary VLC media player, which is a widely known and trusted program for playing multimedia express.
Alternatively, upon closer inspection, it becomes decided that the file is no longer a legit video, but somewhat a unpleasant program. Upon execution of the sinful executable file, the sufferer’s pc show veil will occupy some adjustments.
At the beginning, the cursor will recede, making it complex for the user to navigate and engage with their tool. Additionally, a mistaken pop-up window will appear, designed to seem at bask in a legit notification from the machine.
The pop-up will mix in with the background, making it laborious to detect, and will likely safe counterfeit recordsdata or directions.
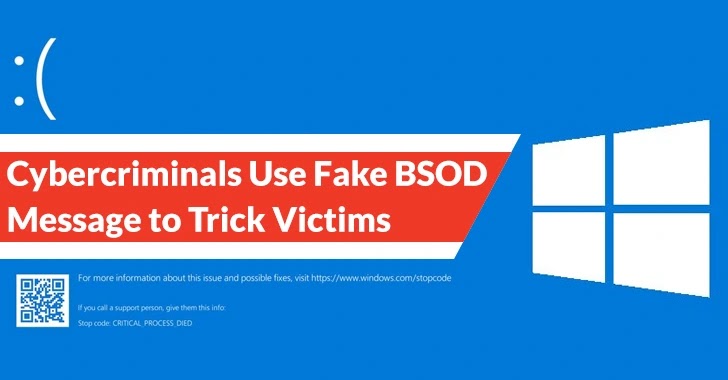
The deceptive pop-up window that seems on the sufferer’s tool has been designed to imitate a frequent error show veil that many Home windows users are conscious of:-
- Blue Hide of Loss of life (BSOD)
BSOD Messages to Trick Victims
This error show veil is displayed on Home windows-primarily primarily based pc systems when a machine error occurs, causing the pc to shatter and exhibiting a blue show veil with an error message.
Unscrupulous tech scammers had been known to make employ of a sneaky tactic intriguing mistaken BSOD screens in show to deceive and exploit unsuspecting pc users.
These scammers will show a bogus BSOD show veil, leading the user to mediate that their tool has been infected with a plague or malware, after which present to form a resolution for a price.
Indubitably, these scammers safe no diagram of fixing any complications and are as a replace trying to extract money from their victims thru dishonest skill.
As soon as the fake BSOD show veil is displayed, the user is presented with a message that strongly advises them to contact a particular cell phone amount for technical strengthen.
Those that call this may maybe occasionally be connected with the very scammers who created the incorrect BSOD show veil within the first plot after which they’re going to persuade the sufferer into paying an needless price for the unwanted strengthen or provider.
A fresh discovery made by Cyble Analysis and Intelligence Labs has uncovered a fake web express that is intelligent in phishing actions.
This web express, that can also additionally be accessed at hxxps[:]//mydoc.hsc-lb[.]find/, has been stumbled on to be spreading a tech unsolicited mail executable that poses a significant possibility to users who unknowingly procure it.
Visiting the find express poses a significant possibility to users as it has been stumbled on to routinely provoke the procure of a unpleasant executable file.
That is accomplished thru a redirect assignment that sends the user to the take care of hxxps[:]//mydoc.hsc-lb[.]find/milf-pornvideo-pornhubhdviideos[.]exe with out their recordsdata.
In show to lift out their spoiled actions, scammers veritably exploit the automated procure feature that is on hand thru many customary web browsers.
The executable file that is downloaded from the aforementioned web express is a 32-bit .NET binary that is specifically designed to target users of Home windows working systems.
After the 32-bit .NET binary file is executed, it initiates the creation of a brand fresh Home windows Make with the default title of “Form1”. Now, from the useful resource directory, the background image of this make is retrieved with abet of the following plan:-
- Assets[.]ResourceManager.GetObject
Following their preliminary actions, the scammers make employ of a particular coding methodology that entails the usage of the “Hide.PrimaryScreen.Bounds” property. By imposing this vogue, they are in a living to fill the entire lot of the show veil with a mistaken Blue Hide of Loss of life (BSOD) image.
At this stage, the binary takes a significant step in its operation by initiating a SoundPlayer object. This object is assigned the identifier “soundPlayer” and is linked to a particular audio file named “backgroundmusic.”
The audio file itself is stored within the sources directory of the executable file. When the audio message is performed, it informs the user that their pc has been locked attributable to suspicious process or a plague an infection.
The message strongly advises the user to steal instantaneous action by calling a selected strengthen amount. Scammers make employ of a massive resolution of how to trick unsuspecting users.
Among these ways is the usage of pretend pop-u.s.a.or notifications, which may maybe also very smartly be designed to lie to users into believing that they’re experiencing a significant mission with their tool.
Ideas
Right here below we have got supplied the entire solutions supplied by the safety experts:-
- Keep no longer click on on links that appear suspicious.
- Guarantee to discontinue no longer procure files from unknown sources.
- Downloads must be triggered for affirmation or blocked altogether in your browser settings.
- Technical strengthen or services supplied via unsolicited messages or calls must be avoided.
- Ensure antivirus instrument is up-to-date on the machine.
- Guarantee that that your working machine and instrument are on a protracted-established foundation up up to now.
Source credit : cybersecuritynews.com

