Developers Beware! Hackers Using Fake Job Offers to Attack Developers
.webp)
Hackers had been focusing on developers by utilizing wrong job gives to hijack GitHub accounts.
This alarming progress has raised essential concerns among corporate files security groups, particularly since developers in most cases like administrative ranking entry to to essential repositories.
The assault begins with an electronic mail that appears to be like to be from GitHub, providing a sublime job feature with a $180,000 annual wage and generous advantages.
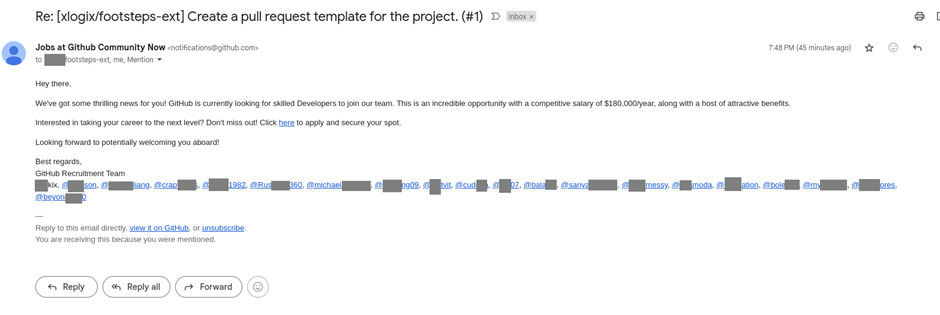
The emails are despatched from [email protected], a authentic GitHub take care of, which makes them appear legitimate, as per a chronicle by Kaspersky.
Nonetheless, there are refined crimson flags, a lot like using a notification take care of for HR communications and electronic mail matters that don’t match the job offer whisper material.
No matter these discrepancies, the promise of a lucrative wage entices some recipients to click on the hyperlink supplied.
Phishing Occupation Internet web whisper online on GitHub
Clicking the hyperlink directs the recipient to a wrong GitHub career way, using addresses like githubtalentcommunity[.]on-line and githubcareers[.]on-line.
These phishing sites like since been taken down, nevertheless no longer sooner than causing essential hurt. On the wrong way, developers are triggered to log in to their GitHub chronicle and authorize a unique OAuth utility.
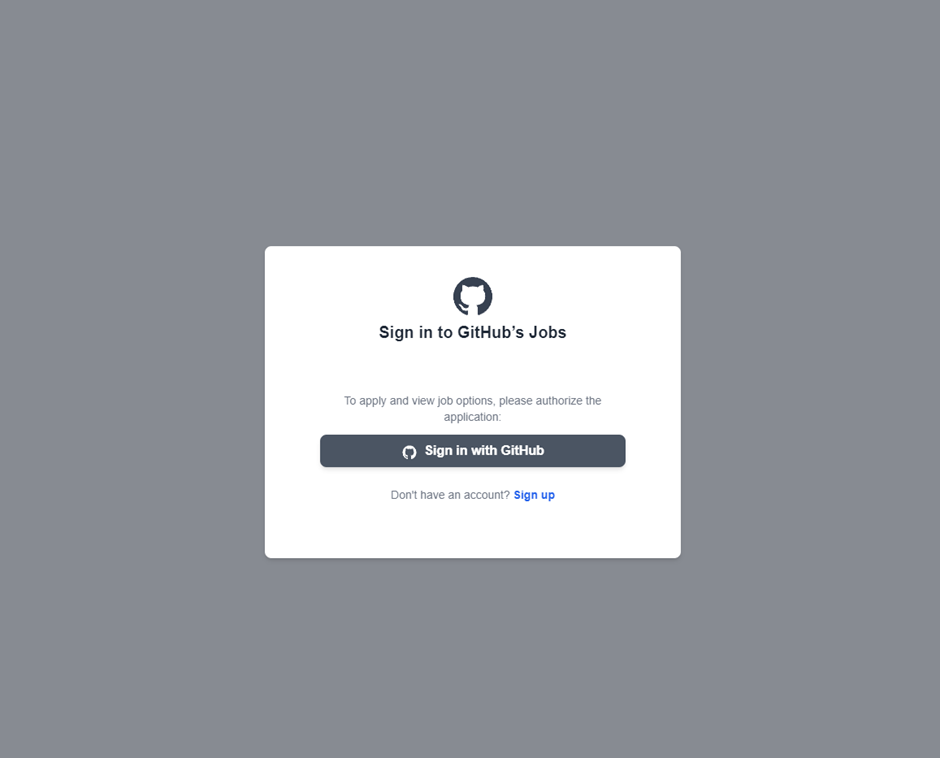
This malicious OAuth utility requests in depth permissions, along side ranking entry to to non-public repositories, non-public files, and the capacity to delete repositories.
One other variant of the phishing electronic mail claims that GitHub has been hacked and requires the user’s authorization to mitigate the implications. Each tactics purpose to trick developers into granting unhealthy permissions.
The Subsequent Factor: Repository Wipe and Ransom Ask
If a developer falls for the rip-off and authorizes the malicious OAuth utility, the attackers fleet exploit the granted permissions.
They wipe your whole victim’s repositories and rename them, leaving gradual easiest a README.me file.
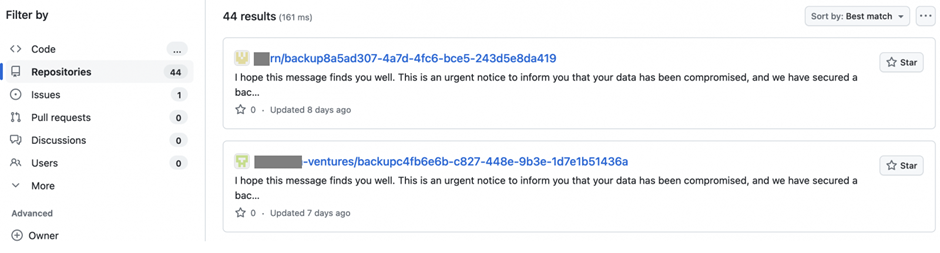
The README.me file accommodates a ransom reward, stating that the tips has been compromised nevertheless a backup exists.
To restore the tips, the victim is instructed to contact a Gitloker user on Telegram.
These phishing emails are despatched using the GitHub discussion machine, leveraging already compromised accounts to ticket loads of customers, who then receive emails from the authentic GitHub take care of.
How to Give protection to In opposition to Such Assaults on GitHub Accounts
To safeguard against these refined phishing assaults, developers must unruffled note these ideas:
- Eye Email Info: Continuously check the fundamental points of an electronic mail, along side the matter, textual whisper material, and sender take care of. Discrepancies are likely signs of phishing.
- Preserve some distance from Clicking Suspicious Links: At the same time as you receive a suspicious electronic mail from GitHub, achieve no longer click on any hyperlinks. Teach the email to GitHub crimson meat up.
- Be Cautious with OAuth Applications: By no methodology authorize unknown OAuth applications. Frequently review and take away any suspicious applications out of your GitHub chronicle.
By staying vigilant and following these guidelines, developers can offer protection to their accounts and prevent seemingly files breaches.
Source credit : cybersecuritynews.com

