DogeRAT Android Malware Mimic Popular Apps to Steal Sensitive Data

DogeRAT (A ways away Safe admission to Trojan) is an originate-source Android malware that targets a huge customer sinister from varied firms, in particular banking, and leisure.
CloudSEK’s TRIAD group detected it. Despite the indisputable truth that this marketing and marketing campaign essentially focused customers in India, it aims to be accessible to all americans.
Specifics of the DogeRAT Android Malware
The malware is being disseminated disguised as a decent app via social networking and messaging apps.
The malware can hold important files from the sufferer’s machine after it has been installed, along side contacts, messages, and banking credentials.
In particular, the malware can additionally be gentle to hijack the sufferer’s machine and produce corrupt projects love sending spam messages, making unauthorized purchases, enhancing files, discovering out name logs, and even snapping photos with the infected machine’s front- and rear-going via cameras.
The impersonated apps consist of Opera Mini – a rapid internet browser, Android VulnScan, YOUTUBE PREMIUM, Netflix Top class, ChatGPT, Lite 1 [Facebook], and Instagram Knowledgeable.
It modified into once learned that the malware’s creator had marketed DogeRAT in two Telegram channels.
The author of the RAT has equipped a top fee version of DogeRAT, which incorporates extra points corresponding to taking screenshots, stealing photos from the gallery, performing as a keylogger, stealing files from the clipboard, and having a brand recent file supervisor as well to better persistence and seamless bot connections with the infected machine.
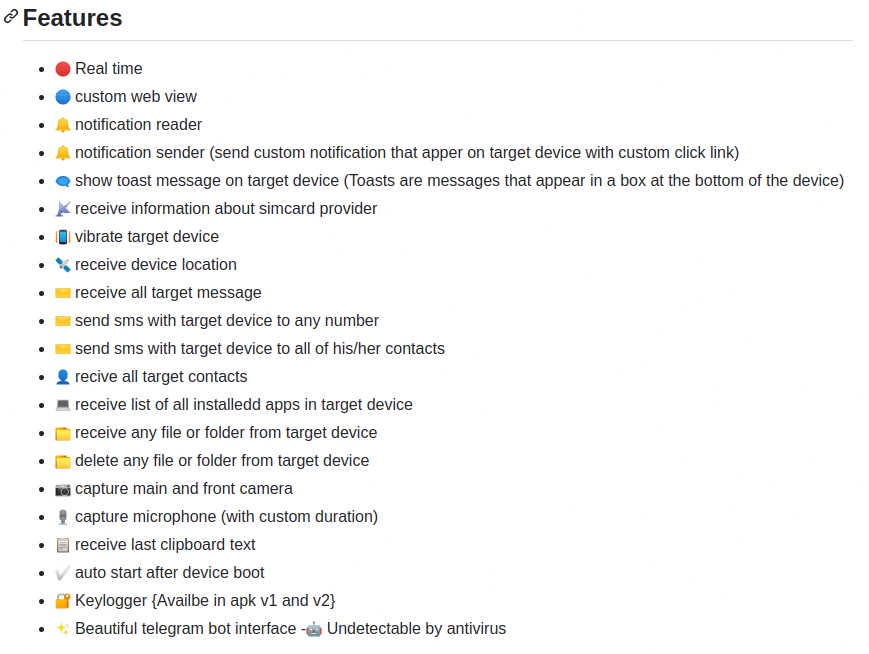
The free version of DogeRAT, screenshots, and video classes demonstrating its points, has been made readily available on GitHub in a further effort to arrangement it more approachable for other felony actors.

“This Java-essentially essentially based android RAT uses a if truth be told straightforward server-facet code written in NodeJs to maintain interplay with Telegram Bot and an infected machine via an internet socket,” researchers value.
“In this wretchedness, the Telegram Bot is working as the Converse and Agree with an eye on panel for the threat actor who creates the setup and deploys the DogeRAT.”
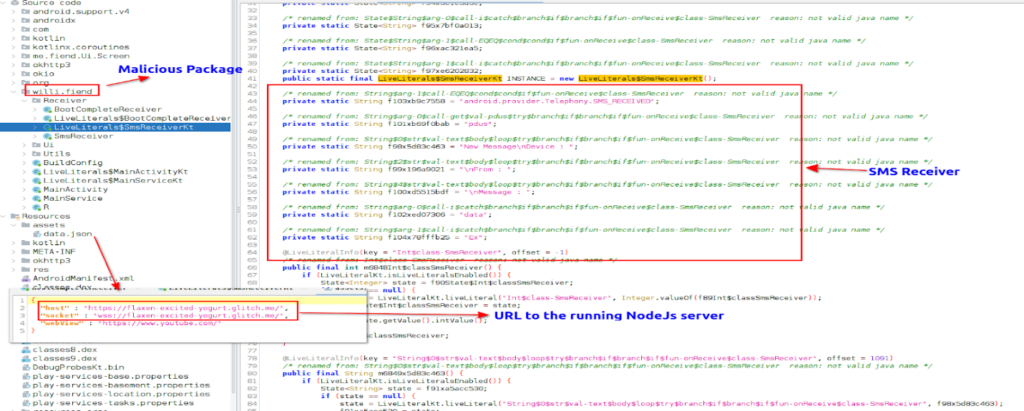
Experiences divulge the trojan at the beginning gains gain admission to to many rights, corresponding to name log gain admission to, audio recording, discovering out of SMS messages, media, photos, etc.

Consequently of this truth, researchers divulge this marketing and marketing campaign serves as a “stark reminder” of the monetary incentives riding scammers to present a hold to their methods consistently.
To offer protection to your digital resources, one maintain to be vigilant and hold protective precautions.
“They are not staunch little to creating phishing internet sites, but additionally distributing modified RATs or repurposing malicious apps to make rip-off campaigns that are low-cost and uncomplicated to dwelling up, yet yield excessive returns,” researchers.
Source credit : cybersecuritynews.com


