Earth Hundun Hacker Group Employs Advanced Tactics to Evade Detection
%20(1).webp)
Earth Hundun, a essential Asia-Pacific malware group, uses Waterbear and Deuterbear.
We first encountered Deuterbear in Earth Hundun’s arsenal in October 2022, signaling its implementation.
This document describes the excellent A long way-off Salvage accurate of entry to Trojan (RAT) we recovered from a C&C server from an Earth Hundun campaign in 2024.
We examined the Waterbear downloader’s network actions at first. A case see exhibits how the Waterbear RAT and its plugins were deployed within the 2nd phase and how Waterbear downloaders unfold across networks, complicating detection and monitoring.
Deuterbear now supports plugin shellcode formats and runs RAT sessions without handshakes.
Trendmicro analysis of Earth Hundun’s Waterbear and Deuterbear malware interactions with targets will sigh its subtle tactics.
Waterbear Case Seek
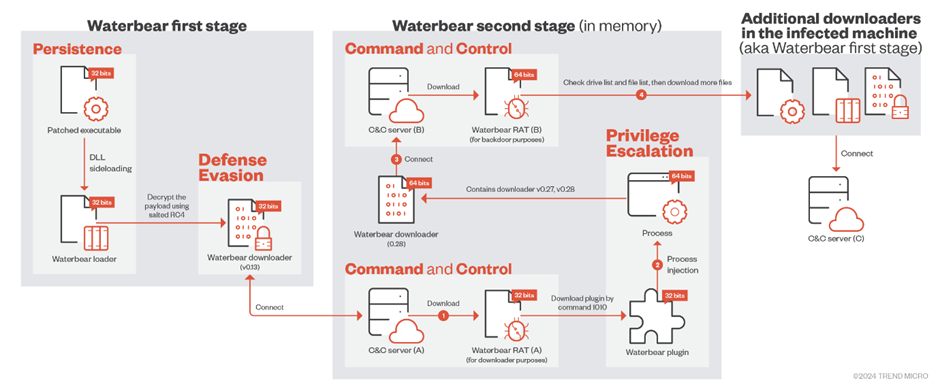
A earlier campaign’s flowchart exhibits Waterbear’s issue in a victim’s network and its proliferation of downloaders.
Initial Stage
In our earlier document, Waterbear dilapidated three files for the preliminary download.
These consist of a modified reputable executable, loader, and encrypted downloader.
The 2d Stage
Waterbear RAT (A) downloaded the plugin via RAT bid 1010 and activated its first export characteristic, “Open up,” to inject it accurate into a activity.
Looking on the target activity architecture, the plugin comprises unencrypted Waterbear downloaders 0.27 and zero.28.
No longer like 32-bit processes, 64-bit processes breeze 0.28, boosting downloads.
This hides their trails or connects to different C&C servers within the victim’s network, showing the possibility actor’s communication flexibility.
Waterbear RAT
Command Capabilities:
- File Administration: Commands for enumerating disk drives, listing files, uploading and downloading files, renaming, constructing folders, deleting files, executing files, shifting files, and disguising file metadata.
- Window Administration: Commands for enumerating, hiding, showing, closing, minimizing, maximizing windows, taking screenshots, and environment screenshot events.
- Route of Administration: Commands for enumerating, terminating, suspending, resuming processes, and retrieving activity module files.
- Community Administration: Commands for getting extended TCP tables and environment TCP entry states.
- Service Administration: Commands for enumerating and manipulating companies and products.
- Configuration Administration: Commands for getting and environment C&C configurations.
- A long way-off Shell Administration: Commands for starting, exiting, and getting the PID of a remote shell.
- Registry Administration: Commands for enumerating, constructing, environment, and deleting registry keys and values.
- Long-established Retain watch over: Commands for getting the present window, environment an infection marks, and terminating connections and RAT processes.
- Proxy Administration: Commands for updating C&C IP addresses, proxying files, shutting down connections, and managing socket handles.
Victim Recordsdata Transmission:
Before executing backdoor instructions, Waterbear sends detailed victim files to the C&C server, including admin repute, design version, host and consumer names, window textual exclaim material, adapter files, activity ID, and an infection marks.
Deuterbear RAT
Set up Pathway:
- Deuterbear uses a two-stage installation activity. The principal stage comprises decrypting and deploying a downloader, which surveys the design and installs the 2nd-stage parts.
- The principal stage parts are removed after persistence is carried out to avoid detection.
Command Capabilities:
- File Administration: Commands for listing files, uploading and downloading files, renaming files, and executing files.
- Route of Administration: Commands for enumerating and terminating processes.
- Configuration Administration: Commands for gathering and updating downloader configuration files.
- A long way-off Shell Administration: Commands for starting, exiting, and getting the PID of a remote shell.
- Long-established Retain watch over: Commands for getting the present window, environment an infection marks, and terminating connections and RAT processes.
- Plugins Administration: Commands for downloading, uninstalling, and executing plugins, including shellcodes and PE DLLs
Victim Recordsdata Transmission:
Equivalent to Waterbear, Deuterbear sends victim files to the C&C server sooner than executing backdoor instructions, including admin repute, consumer and host names, OS version, window textual exclaim material, adapter files, activity ID, and an infection marks.
Variations from Waterbear:
Deuterbear retains fewer instructions (20 when in comparison with over 60 for Waterbear) but supports more plugins to beef up flexibility.
It uses the the same HTTPS channel and RC4 web exclaim online visitors key as the downloader, laying aside the need for a handshake with the C&C server to update communication protocols.
Waterbear evolved into Deuterbear, a fresh malware.
Interestingly, Waterbear and Deuterbear evolve individually in achieve of replacing every different.
Reminiscence scans for downloads and the Waterbear and Deuterbear RATs can shield organizations from Earth Hundun assaults. Additionally, discovering the registry dilapidated to decrypt the Deuterbear downloader can attend win it within the design.
Source credit : cybersecuritynews.com

