GhostSec & Stormous Operators Launched Twin Ransomware Attacks
.webp)
A hacking community has developed with a fresh ransomware variant identified as GhostLocker 2.0.
This community, in collaboration with the Stormous ransomware operators, has initiated double extortion ransomware assaults targeting varied firms globally.

The joint efforts of GhostSec and Stormous beget resulted in the creation of a fresh ransomware-as-a-service program named STMX_GhostLocker, providing various choices for his or her mates.
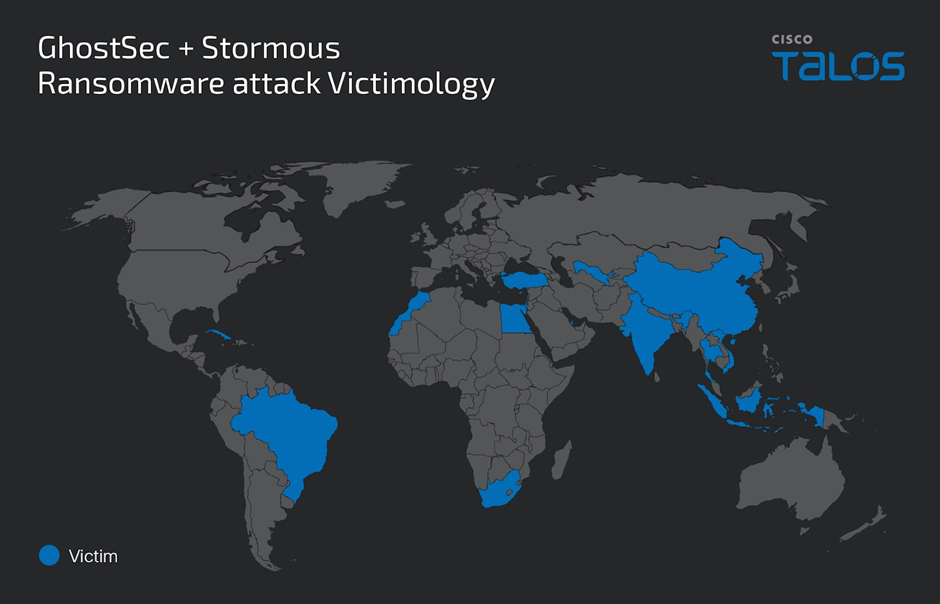
Global Impact of Ransomware Attacks
The victimology of these assaults spans across a pair of countries, including Cuba, Argentina, Poland, China, and tons of others.
Are you from SOC and DFIR teams? – Be half of With 400,000 honest Researchers
Malware diagnosis will possible be rapidly and simple. Wonderful permit us to cloak you the style to:
- Accept as true with interplay with malware safely
- Home up virtual machine in Linux and all Home windows OS variations
- Work in a crew
- Bag detailed stories with most data
Whilst you happen to can beget to test all these aspects now with fully free win admission to to the sandbox: ..
These cybercriminal activities beget affected victims in various commercial sectors, as disclosed by the teams of their Telegram channels.
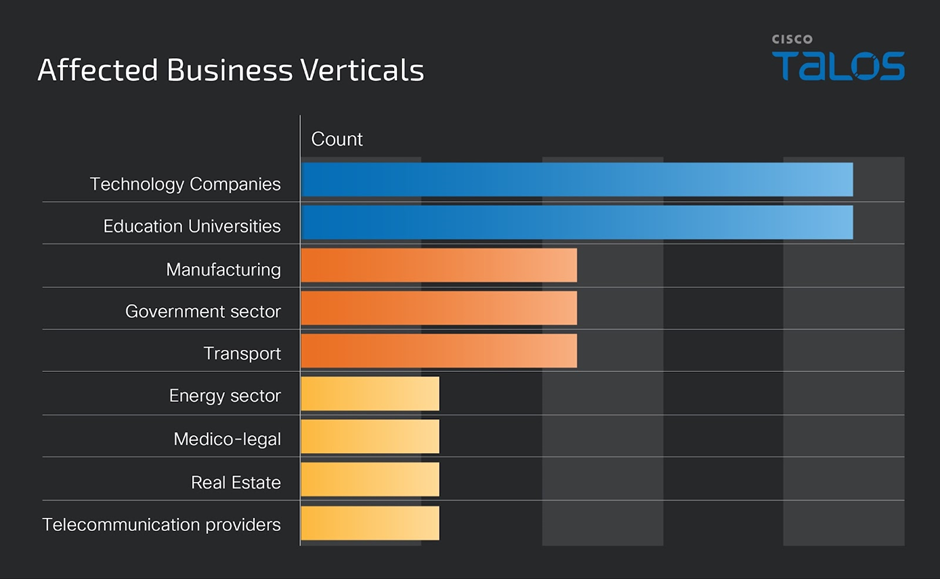
Severely, GhostSec has been actively targeting Israel’s industrial methods and critical infrastructure, with reported assaults on organizations love the Ministry of Defense in Israel.
Using the GhostLocker and StormousX ransomware malware, Talos found that the GhostSec and Stormous gangs had been collaborating on loads of double extortion assaults.
Evolution of GhostLocker Ransomware
GhostSec launched an upgraded model of their ransomware called GhostLocker 2.0, showcasing continuous construction efforts with plans for additional iterations love GhostLocker V3.
The ransom cloak plot has developed to include instructions for victims to true their encryption ID and interact in negotiations internal a specified timeframe to stop data disclosure.
The ransomware’s capabilities include encryption of recordsdata with a “.ghost” extension and dialog with a Expose and Protect watch over (C2) server situated in Moscow.
Instruments and Tactics Employed
To boot to ransomware assaults, GhostSec has been utilizing instruments love the “GhostSec Deep Scan tool” and “GhostPresser” to compromise websites. The Deep Scan toolset enables comprehensive scanning of websites for vulnerabilities and applied sciences aged, while GhostPresser specializes in exploiting WordPress sites thru XSS assaults.
These instruments sing the community’s sophistication in cyber operations and continuous enhancement of their capabilities.
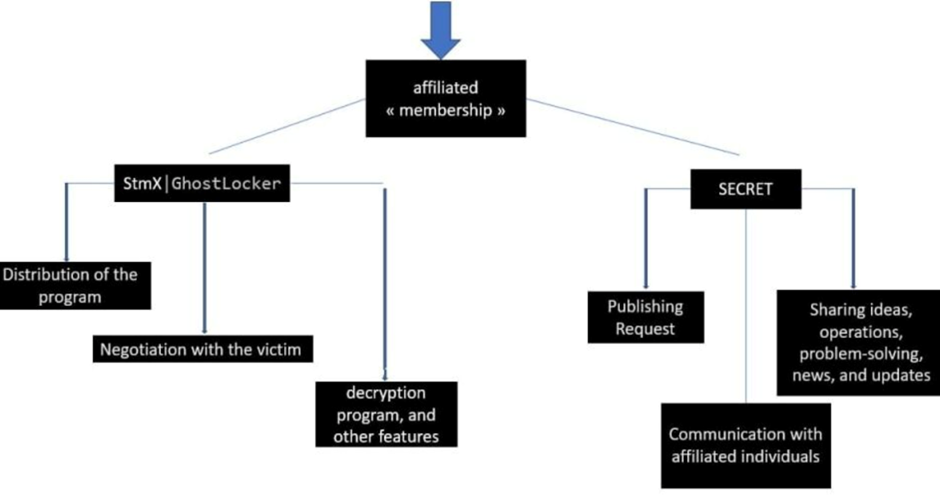
Stormous and GhostSec beget jointly launched the STMX_GhostLocker program on the TOR community, providing products and services for mates to enroll in and sing sufferer data.
This system offers various categories of products and services for mates, including paid choices and aspects for contributors having a be taught to sell or submit data. The blog dashboard showcases sufferer counts and disclosed info, with reported ransom quantities reaching as a lot as USD 500,000.
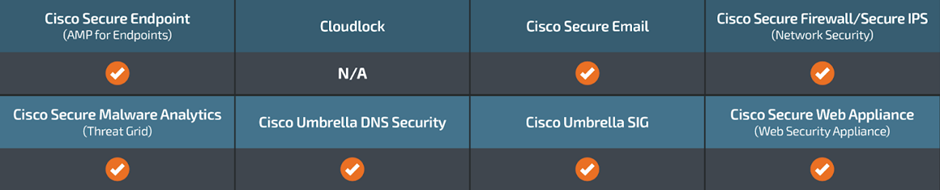
Cybersecurity Measures
The most important solutions to stop malware execution, block malicious websites and emails, detect malicious relate linked to threats love GhostLocker 2.0, and present multi-element authentication for community security.
This collaborative effort between GhostSec and Stormous in launching twin ransomware assaults underscores the evolving panorama of cyber threats targeting firms worldwide.
Using progressed instruments and suggestions highlights the need for mighty cybersecurity measures to strive against such malicious activities successfully.
You would possibly want to maybe presumably block malware, including Trojans, ransomware, spy ware, rootkits, worms, and zero-day exploits, with Perimeter81 malware safety. All are incredibly monstrous, can wreak havoc, and damage your community.
Discontinue updated on Cybersecurity info, Whitepapers, and Infographics. Phrase us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


