Ghosttoken – Zero-Day Flaw Lets Attackers Gain Access to Google Accounts

Astrix’s Security Analysis Neighborhood reported a 0-day float within the Google Cloud Platform (GCP) linked to an OAuth float exploitation. This methodology modified into termed “Ghosttoken.”
Exploiting this flaw is completed by scheme of a malicious application, which is able to lead threat actors to construct obtain admission to to the sufferer’s Google narrative without raze.
For sure one of many biggest and provoking facts about this assault is that it remains in stealth and entirely unremovable without raze. Fortunately, Google released a patch for this vulnerability on April 7, 2023.
GhostToken: Exploration and Exploitation
Threat actors can use the GhostToken vulnerability to construct obtain admission to to a sufferer’s Google narrative with the abet of a malicious application.
Users can use Google’s application administration web page to learn about the gains with obtain admission to to their Google accounts and put off them if vital.
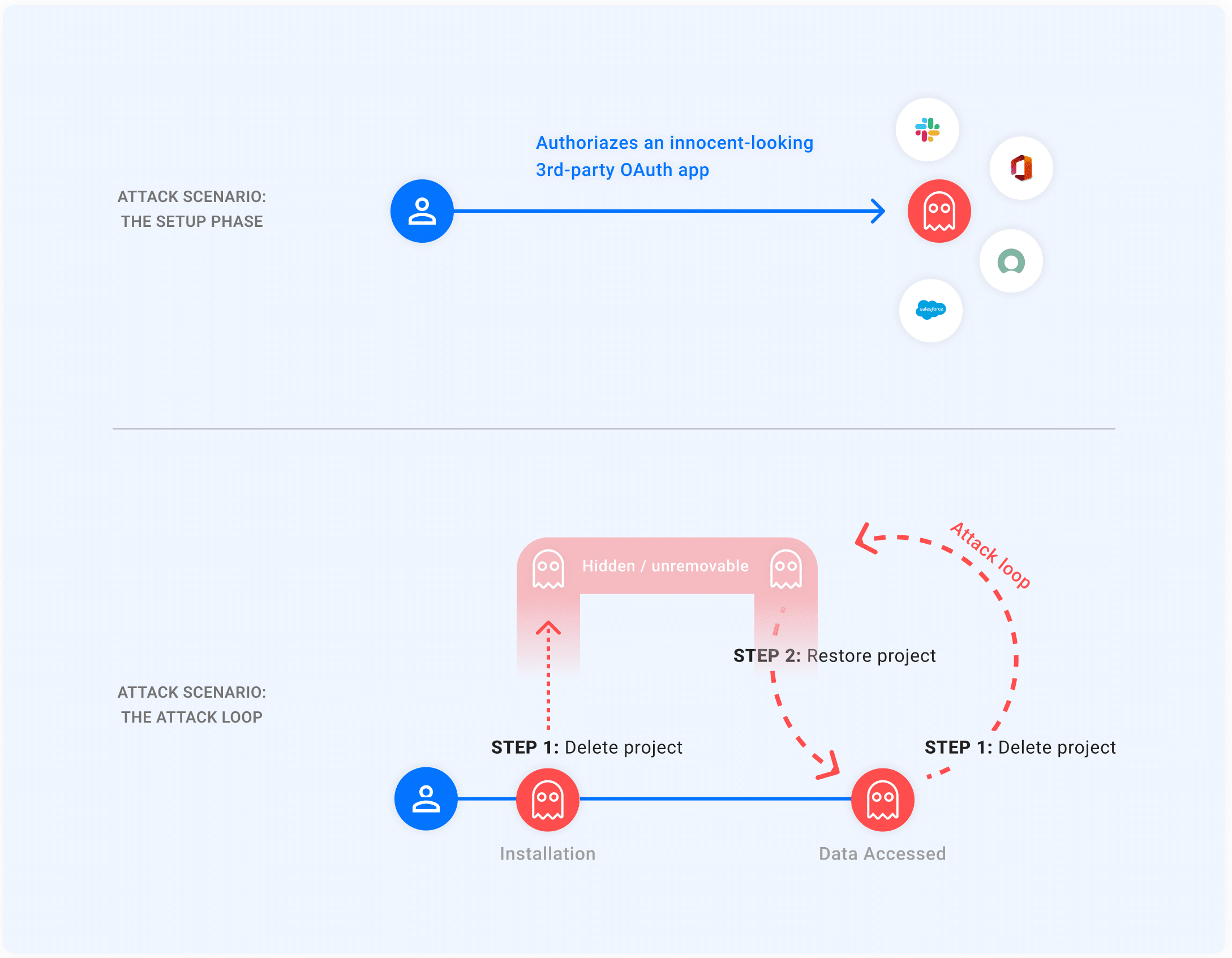
As soon as an individual authorizes an application with the OAuth float, the application receives a token from Google to obtain admission to the particular person’s Google narrative.
However, within the case of GhostToken exploitation, once the sufferer authorizes the malicious application, the threat actor can disguise it from the application management web page, making it sophisticated for users to search out and revoke obtain admission to to the malicious application.
The sufferer will not bear every other alternatives nonetheless to create a brand modern Google narrative.
As soon as the attacker gets their fingers on the Google narrative, they’ll delete an electronic mail, send an electronic mail, conduct a phishing assault, delete the motive force recordsdata, ascertain calendar events, and obtain admission to ravishing knowledge.
Hiding from the Application Administration Online page
As per Google, if an application wishes OAuth, the builders ought to create a GCP mission to obtain a mission identifier.
The builders moreover bear the privilege to delete and restore the application each time they need.
If an application within the GCP is deleted, it takes 30 days to totally delete the mission, internal which the application developer can restore it.
The application will not be visible on the Google Application Administration Online page at some point of the deleted enlighten.
Level to: When restoring the application, this will in all probability also bear the the same refresh token it had at some point of creation, which is able to be frail to restore the application fully.
Attackers use this safety loophole to disguise their gains from the application management web page.
Mitigation
As per this vulnerability, it is miles hard for the particular person to search out the malicious application because it is miles hidden from the application management web page. However, the users can revoke obtain admission to to the malicious application each time the attacker restores it.
Unfortunately, it is a shrimp timeframe and unpredictable when the attacker will restore the application.
Google’s Patch
As a fix, Google made the gains within the pending deletion enlighten appear on the application management web page, which the users can use to revoke the malicious application obtain admission to.
Building Your Malware Defense Approach – Download Free E-E book
Related Read:
- 2nd Google Chrome Zero-Day Worm Actively Exploited in Wild – Update Now!
- Novel Google Chrome Zero-Day Worm Actively Exploited in Huge – Emergency Update!
- Hackers Exploited Windows Zero-day For Ransomware Assaults
Source credit : cybersecuritynews.com


