GobRAT Malware Attacking Linux Routers to Deploy Backdoor

In February 2023, JPCERT/CC confirmed malware attacks on routers in Japan, namely targeting Linux routers with a recent Golang RAT referred to as GobRAT.
The attacker exploits publicly accessible routers WEBUIs, leveraging potential vulnerabilities to infect them with the GobRAT indirectly.
After an web-uncovered router is compromised, a loader script is deployed to carry GobRAT, which disguises itself as the Apache daemon direction of (apached) to handbook clear of being detected.
How the Assault Chain Works
The attacker begins by targeting a publicly accessible router with an begin WEBUI, exploits vulnerabilities thru script execution, and indirectly spoils the GobRAT.
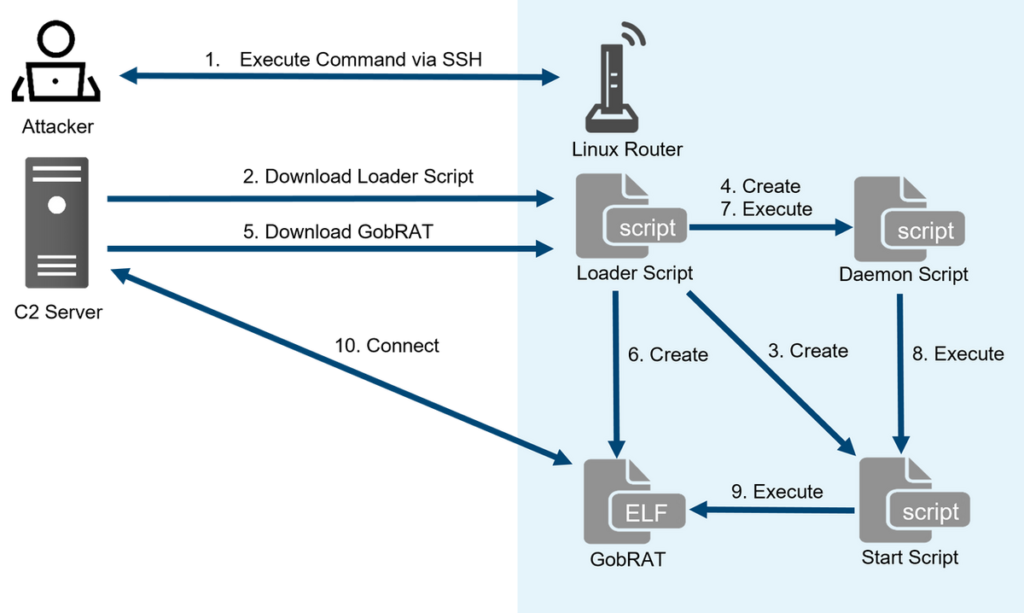
The Loader Script is a multifunctional loader, encompassing tasks cherish script skills, GobRAT downloading and containing a laborious-coded SSH public key for the assumed backdoor.
Loader Script makes use of crontab to waste certain the persistence of the file direction for Originate Script, whereas GobRAT lacks this potential, highlighting the capabilities of the Loader Script.
Right here below, we have talked about the capabilities of Loader Script:-
- Disable Firewall operate
- Earn GobRAT for the target machine’s structure
- Earn a Originate Script and waste it continual
- Earn and chase Daemon Script.
- Register an SSH public key in /root/.ssh/authorized_keys
The Originate Script code, to blame for executing GobRAT, distinguishes itself by recording the startup time in a file referred to as restart[.]log, whereas also working GobRAT below the guise of a sound direction of named apached.
The Daemon Script screens the web site of the Originate Script each and each 20 seconds. It initiates it if it’s no longer working, indicating its potential operate in facing unexpected terminations of the Originate Script.
Right here below, we have talked about the final checks that the GobRAT performs:-
- IP tackle and MAC tackle of itself
- Uptime by uptime bellow
- Network conversation web site by /proc/bag/dev
GobRAT makes use of TLS for records conversation with its C2 server, employing a 4-byte records measurement indicator adopted by gob serialized records, which is a Roam-explicit protocol frail for receiving instructions and transmitting bellow execution results.
Commands Performed by Malware
GobRAT, targeting routers, makes use of twenty-two instructions from the C2 server, mainly alive to on conversation capabilities cherish frpc, socks5, and C2 reconfiguration.
Right here below we have talked about the final indispensable instructions:-
- Manufacture machine Data
- Carry out reverse shell
- Read/write recordsdata
- Configure contemporary C2 and protocol
- Originate socks5
- Carry out file in /zone/frpc
- Strive to login to sshd, Telnet, Redis, MySQL, and PostgreSQL services and products working on one more machine
Whereas apart from this, Lumen Unlit Lotus Labs only currently found that HiatusRAT, a malware, has been exploiting industry-grade routers to peek on victims in Latin The united states, Europe, and North The united states for the past three months.
Source credit : cybersecuritynews.com


