Google Drive Security Flaw Let Hackers Exfiltrate Data Without Any Trace

Google Drive is without a doubt one of potentially the most outmoded cloud-based storage platforms, and attributable to its huge recognition and capabilities, it’s actively focused by threat actors.
Knowledge theft is a prevalent draw employed by malicious actors when they like entry into a platform. It serves as a overall attack vector for stealing files.
Mitiga’s be taught team has no longer too long ago performed a comprehensive investigation into knowledge exfiltration programs interior Google Workspace, highlighting the importance of this attack draw and platform.
This be taught aligns with their ongoing efforts to explore and realize cloud and Instrument as a Service (SaaS) assaults and forensic practices.
Attack on Google Drive
Malicious actors generally scheme to exploit vulnerabilities interior Google Drive to sort unauthorized entry to restful files and particular person knowledge.
Consultants conducting an in-depth prognosis uncovered a vital security flaw interior Google Workspace, revealing a troubling deficiency in its forensic measures.
This vulnerability enables threat actors to stealthily exfiltrate knowledge from Google Drive without leaving any detectable traces.
Google Workspace offers enhanced transparency by utilizing “Drive log occasions” to visual show unit and note diverse actions performed on a firm’s Google Drive sources.
Google Workspace Safety
Google Workspace files occasions exciting exterior domains, such as sharing an object with users delivery air the organization, guaranteeing comprehensive monitoring and monitoring.
These occasions are captured and logged to make a complete describe of interactions with exterior users.
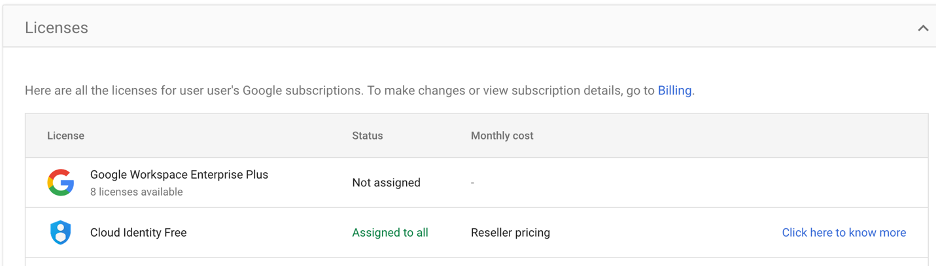
The application of this practice is specific to actions performed by users holding a paid license, which kinds the core limitation of the teach of affairs, nonetheless this restriction is a key voice that desires to be mounted.
All Google Drive users are in the starting attach provided with a “Cloud Id Free” license because the default possibility. This license grants fashioned entry and performance to the actual person interior the Google Drive ecosystem.
Right here, the directors must place a paid license to users, namely the “Google Workspace Project Plus” license to free up extra facets.
Exploitation
The absence of positive visibility poses a terrific voice in two main eventualities, main to likely concerns, and here below we like talked about these eventualities:-
A threat actor compromises a particular person’s story
If a threat actor manages to compromise an admin particular person’s story, they’ll take possess watch over of diverse serious actions. In this teach of affairs, the system generates log files entirely for the actions of revoking and assigning licenses.
Diverse activities or occasions can also merely no longer be recorded or logged. If a threat actor infiltrates a particular person story that lacks a paid license nonetheless has entry to the organization’s personal power, it raises critical security concerns.
Employee offboarding
This teach of affairs arises when an employee departs from the firm, and their license is revoked before their Google particular person story is properly disabled or eliminated.
With out prior notification, the employee holds the aptitude to glean interior files without prolong from their personal power.
In scenarios where a firm’s particular person doesn’t like a paid license nonetheless restful has entry to their personal power, they’ll glean the flexibility’s files without producing any log files.
This poses a doable possibility when the actual person departs from the organization, as their ability to glean files remains untraceable.
Concepts
Mitiga’s security analysts like reached out to Google’s security team referring to the topic, nonetheless they’ve no longer got an legitimate response to incorporate into this advisory.
Right here below, we like talked about your total ideas offered by the consultants:-
- Below the “Admin Log Events,” must visual show unit your total occasions about license assignment and revoke.
- It’s miles considerable to generally originate threat hunts interior Google Workspace, namely specializing in detecting and investigating this particular process.
- You would maybe perhaps perhaps successfully establish and mitigate likely threats and security breaches by conducting these proactive searches.
- To successfully detect conditions where files are being copied from a shared power to a non-public power and therefore downloaded, monitoring the “source_copy” occasions in the course of your hunts is the biggest.
Struggling to Discover The Safety Patch in Your Arrangement? –
Strive All-in-One Patch Manager Plus
Source credit : cybersecuritynews.com

