Hacker Groups Adding New Double DLL Sideloading Technique to Evade Detection

The cybersecurity security researchers at Sophos recently detected the “Dragon Breath” APT personnel (aka Golden Gape Dog, APT-Q-27) using complicated DLL sideloading variations to steer sure of detection.
The APT personnel deploys a recent attack vector that utilizes orderly applications love Telegram to malicious malware loader DLLs and sideloads 2nd-stage payloads.
DLL Sideloading
APT actors spend BlackSEO or malvertizing tactics to promote malicious versions of Telegram, LetsVPN, or WhatsApp apps that are localized for Chinese language users as bait to infect victims on Android, iOS, or Home windows platforms.
In conserving with Sophos file, this marketing campaign is primarily concentrated on Chinese language-speaking Home windows users in the following countries:-
- China
- Japan
- Taiwan
- Singapore
- Hong Kong
- The Philippines
Attackers had been exploiting DLL sideloading, which takes advantage of Home windows’ disturbed loading of Dynamic Hyperlink Library (DLL) recordsdata since 2010.
To execute DLL sideloading, the attacker places a malicious DLL with the identical title as a required, legitimate DLL in the application checklist.
Upon launching the executable, the operating machine prioritizes the malicious DLL positioned in the local checklist over the legitimate one in the machine folders.
As a result, the malware can execute and stay its supposed actions. At this stage, the attacker’s DLL incorporates malicious code to spend the depended on and signed application, thereby gaining elevated privileges on the host machine.
The marketing campaign in question entails victims executing the installer of the specified apps, which ends in installing varied substances on the machine.

Technical Analysis
Moreover, the installer generates a shortcut on the desktop and establishes an entry for machine startup.
In case the victim makes an strive to initiate the recently fashioned desktop shortcut, which is similar outdated first pass, quite than executing the application, the machine triggers the following tell:-
- “C:Customers{redacted}AppDataRoamingTg_B518c1A0Ff8CappR.exe /s /n /u /i:appR.dat appR.dll”
Upon execution, the JavaScript code is designed to birth out the Telegram app user interface in the foreground. Meanwhile, varied sideloading substances are installed in the background with out the user’s records.
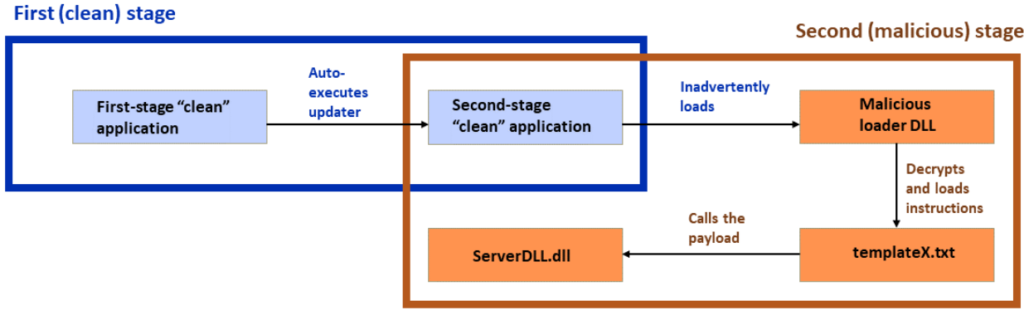
Subsequently, the installer hundreds a 2nd-stage application via ‘libexpat.dll,’ a recent and orderly dependency to birth out a 2nd immaculate application, functioning as an middleman stage of the attack.
In a variation of the attack, the ‘Beijing Baidu Netcom Science and Abilities Co.’, Ltd signs the orderly 2nd-stage loader, renamed “Utility.exe” from “XLGame.exe.
One other attack variation entails an unsigned orderly loader known as “KingdomTwoCrowns.exe,” which seems to encourage no motive as opposed to obfuscating the execution chain. Meanwhile, the third variation uses a digitally-signed orderly loader named “d3dim9.exe,” which belongs to HP Inc.

Using the “double DLL sideloading” methodology, APT groups can evade detection, develop persistence, and obfuscate their assaults, making it remarkable for defenders to adapt to their attack patterns and steady their networks effectively.
Despite the attack variation, the final payload DLL is regularly decrypted and completed on the machine from a txt file known as ‘templateX.txt.’
Apart from this, in most modern instances, DLL sideloading has become one of primarily the most sought malicious tactics hackers create primarily the most of.
Building Your Malware Protection Procedure – Download Free E-E book
Source credit : cybersecuritynews.com

