Hackers Abuses SVG Image Files to Deliver GUloader Malware

Hackers are exploiting the versatility of SVG (Scalable Vector Graphics) recordsdata to distribute the GUloader malware.
Figuring out adverse actors’ ideas and instruments is essential to staying forward within the ever-changing cybersecurity subject.

Its stealthy ideas and talent to elude detection make this sophisticated malware loader a most well-known possibility to corporations and other folks.
Guloader uses evasion ideas, making it sophisticated for conventional safety measures to identify and mitigate. This highly elusive loader poses a most well-known possibility to every organizations and other folks.
It is probably you’ll possibly possibly analyze a malware file, network, module, and registry task with the ANY.RUN malware sandbox and the Threat Intelligence Search for that can enable you to work alongside with the OS without lengthen from the browser.
Rise of GUloader
GUloader is identified for its stealth and talent to evade extinct safety measures by polymorphic code and encryption.
This permits it to dynamically change its construction, making it sophisticated for antivirus utility and intrusion detection programs to detect its presence.
In conserving with the observations made by SpiderLabs, there modified into as soon as a famous amplify within the frequency of GuLoader utilization.
McAfee Labs has currently seen a marketing campaign where GUloader is dispensed by malicious SVG recordsdata despatched by email.
SVG recordsdata are continually extinct for 2-dimensional vector graphics and serve interactivity and animation by JavaScript and CSS.
Stylish browsers cherish Chrome, Firefox, and Edge can render SVG recordsdata natively, treating them as usual net pages. Cybercriminals are exploiting this inherent trust in SVG recordsdata to carry malware.
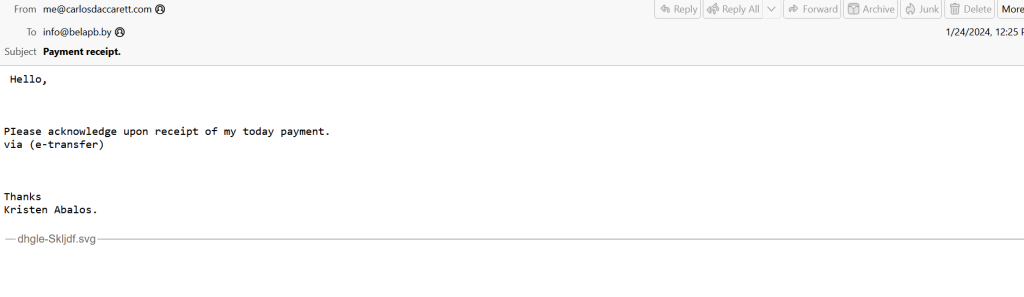
The infection begins when a user opens an SVG file attached to an email. This triggers the browser to download a ZIP file containing a Home windows Script File (WSF).
The WSF then executes, the usage of wscript to name a PowerShell inform that connects to a malicious area and executes hosted content, in conjunction with shellcode injected into the MSBuild application.
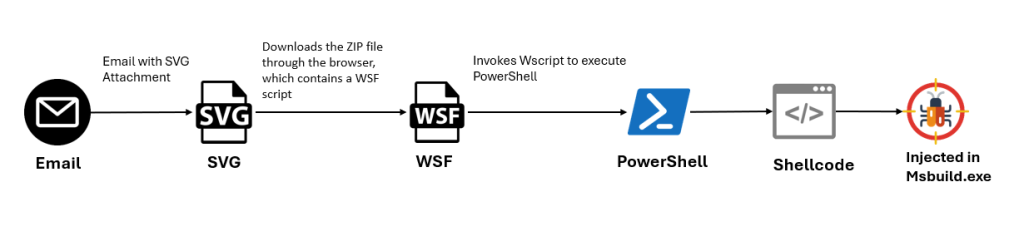
Technical Analysis of the Attack
The attack begins with a unsolicited mail email containing an SVG file named “dhgle-Skljdf.svg”. The SVG file contains JavaScript that creates a malicious ZIP archive when the file is opened.
The ZIP file as soon as dropped into the machine, displays an obfuscated WSF script that is sophisticated to examine.
This script invokes PowerShell to connect with a malicious area and pause the retrieved content, in conjunction with base64-encoded shellcode and a PowerShell script.
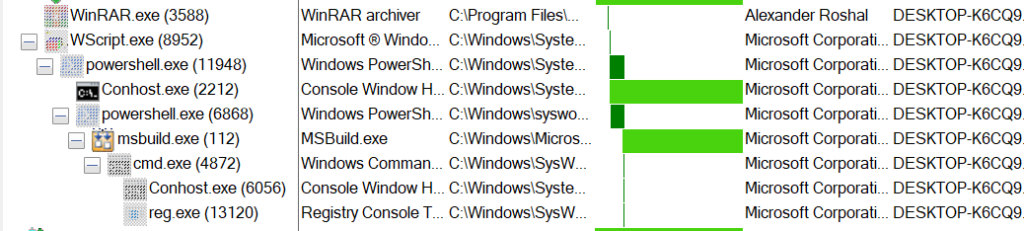
The PowerShell script makes an try to load the shellcode into the legit MSBuild job the usage of the Process Hollowing methodology.
After injection, the shellcode performs an anti-evaluation take a look at and modifies the Registry scuttle key to pause persistence.
The closing stage involves downloading and executing the closing malicious executable, GUloader, or malware variants.
Utilizing SVG recordsdata to carry malware cherish GUloader is a touching on constructing within the cybersecurity panorama.
Organizations and other folks should always take care of surprising email attachments cautiously, specifically those containing SVG recordsdata. Security professionals are encouraged to alter their detection programs to counter this evolving possibility.
IOCs
| File | SHA256/URL |
| 66b04a8aaa06695fd718a7d1baa19386922b58e797634d5ac4ff96e79584f5c1 | |
| SVG | b20ea4faca043274bfbb1f52895c02a15cd0c81a333c40de32ed7ddd2b9b60c0 |
| WSF | 0a196171571adc8eb9edb164b44b7918f83a8425ec3328d9ebbec14d7e9e5d93 |
| URL | hxxps://winderswonders[.]com/JK/Equitably[.]mix |
It is probably you’ll possibly possibly block malware, in conjunction with Trojans, ransomware, adware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly substandard, can wreak havoc, and hurt your network.
Discontinue up thus a long way on Cybersecurity info, Whitepapers, and Infographics. Be conscious us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


