Hackers Attacking Infra Teams With Fake PuTTY & FileZilla Ads
.webp)
A stylish malvertising campaign is concentrated on gadget administrators all over North The United States.
The attackers are utilizing false classified ads for traditional gadget utilities to distribute a unhealthy rigidity of malware identified as Nitrogen.
Step 1: Luring Victims with Malicious Commercials
The campaign exploits the belief users establish in search engine classified ads. By displaying sponsored search outcomes for utilities admire PuTTY and FileZilla, the attackers can trap of their victims.
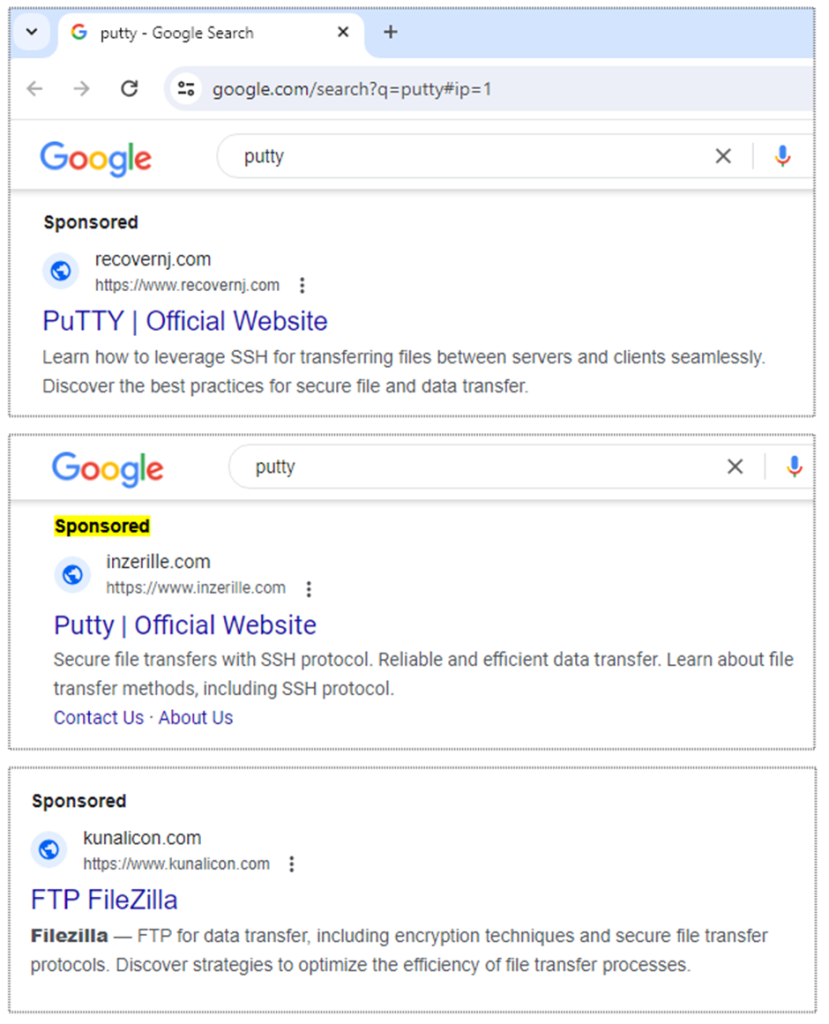
These classified ads are convincing and tailored to the search habits of IT mavens, making them particularly efficient.
AI-Powered Protection for Industry Email Security
Trustifi’s Evolved possibility security prevents the widest spectrum of refined attacks earlier than they attain a user’s mailbox. Stopping ninety 9% of phishing attacks neglected by other electronic mail security alternatives. .
Once clicked, these malicious classified ads lead users to download what they have confidence to be reliable gadget installers.
On the different hand, these installers are trojanized versions designed to infect the user’s gadget with Nitrogen malware.
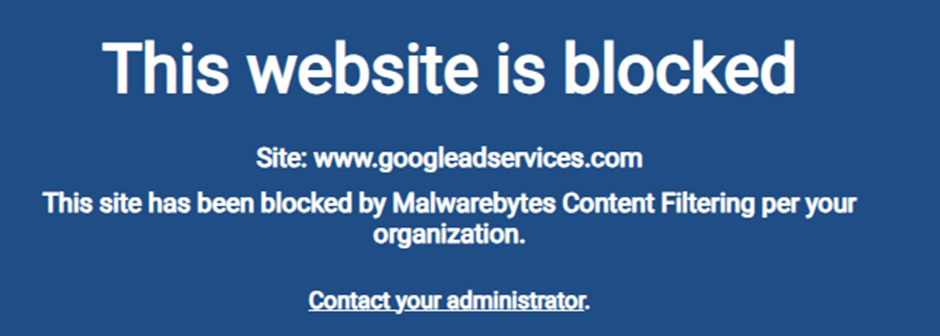
This malware serves as a gateway for attackers to function preliminary to find admission to to non-public networks, which can then be exploited for data theft or to deploy ransomware such as BlackCat/ALPHV.
Despite experiences to Google, the malicious classified ads proceed to bustle, prompting the cybersecurity community to share detailed recordsdata on the tactics, tactics, and procedures (TTPs) former by the attackers and indicators of compromise (IOCs) to assist gadget administrators shield towards these threats.
A most up-to-date article published in Malwarebytes Labs highlighted that hackers are in point of fact concentrated on infrastructure teams utilizing false classified ads for PuTTY and FileZilla.
Step 2: Deception Via Lookalike Sites
The attackers have arrange a refined malvertising infrastructure that makes use of cloaking tactics to evade detection.
Searching on the declare, users who click on the classified ads can also be redirected to a harmless decoy establish or a video of Rick Astley—a tactic former to mock security researchers.
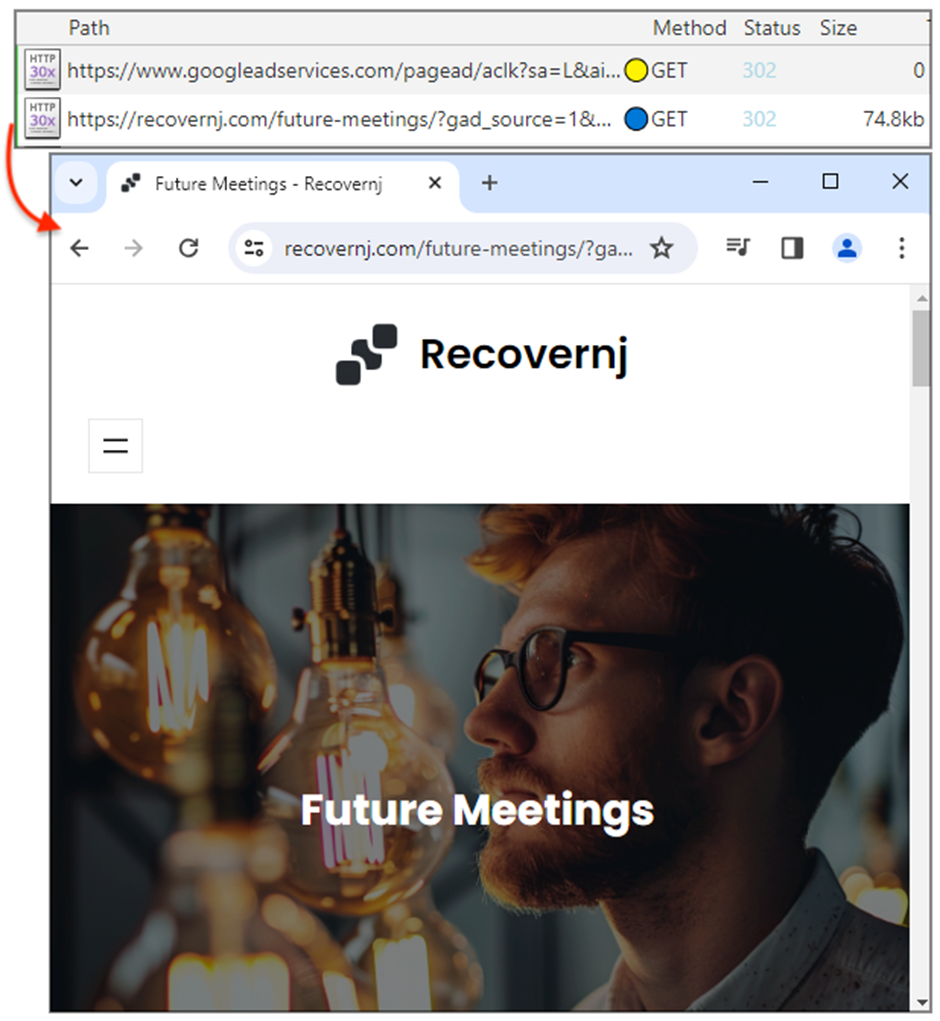
On the different hand, for skill victims, the redirect outcomes in lookalike sites convincing replicas of the reliable gadget pages they are impersonating.
These sites are designed to be as misleading as that you would possibly perhaps per chance perhaps per chance per chance also have confidence, rising the probability that any individual will download the malware-encumbered installers.
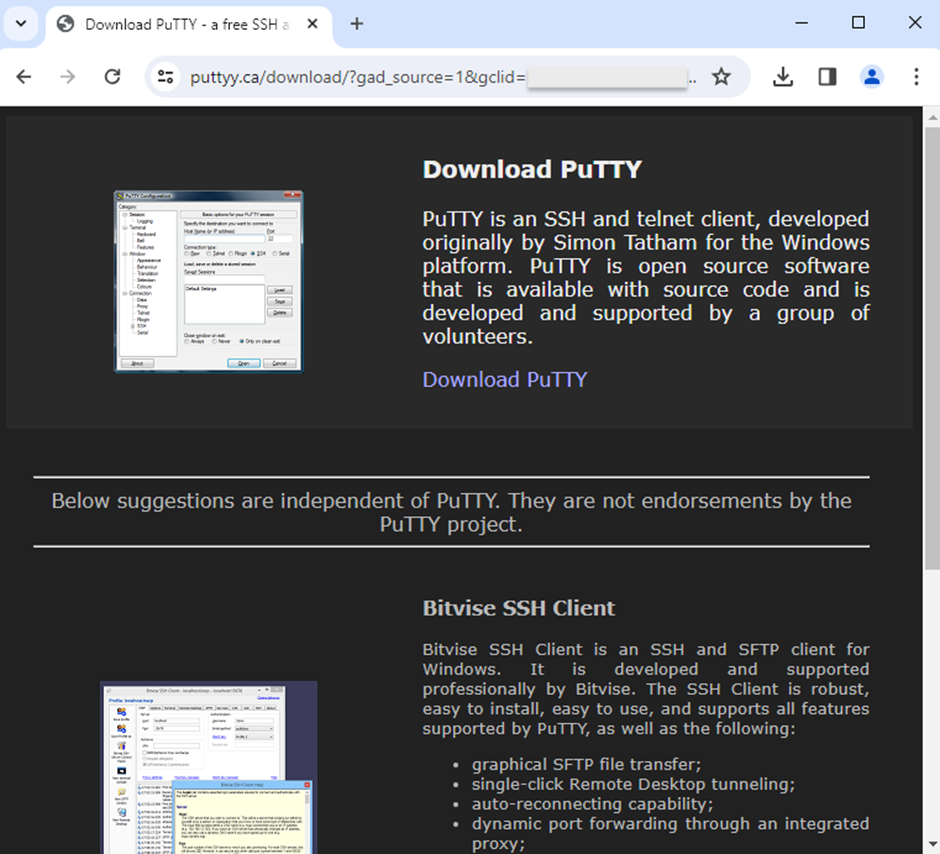
Step 3: Deploying Malware and Conserving In opposition to Assaults
The remaining step on this malicious chain is deploying the Nitrogen malware by the flawed installers.
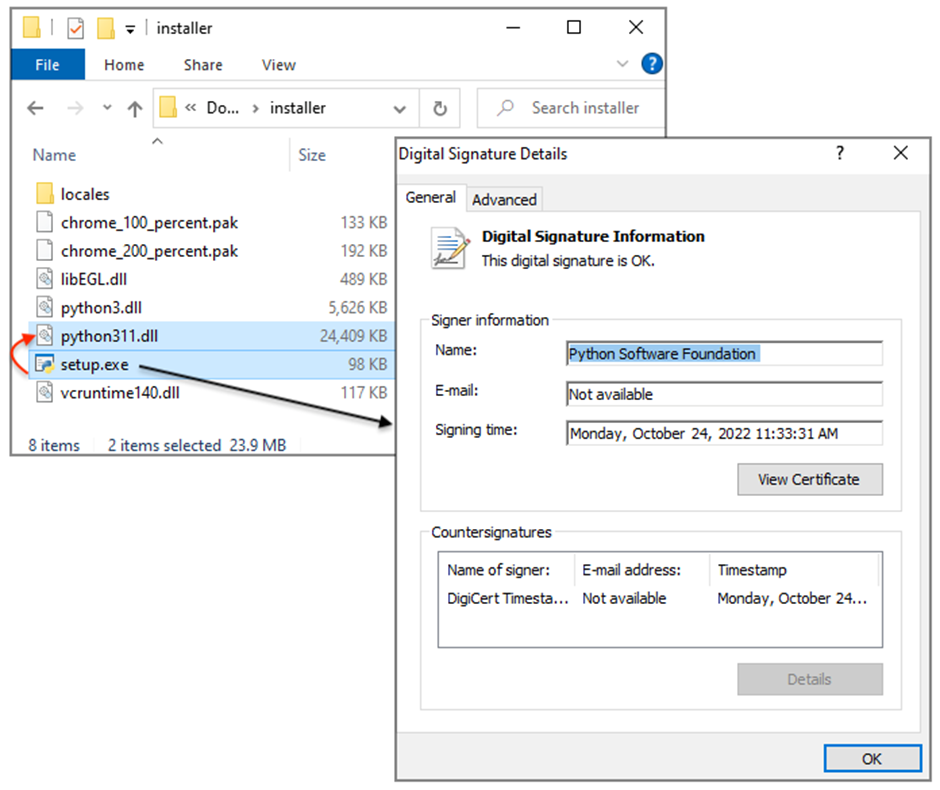
The malware makes use of a approach identified as DLL sideloading, the establish a reliable executable is former to originate a malicious DLL file.
On this occasion, a apparently innocuous setup.exe file sideloads a unhealthy file named python311.dll, which is associated with Nitrogen.
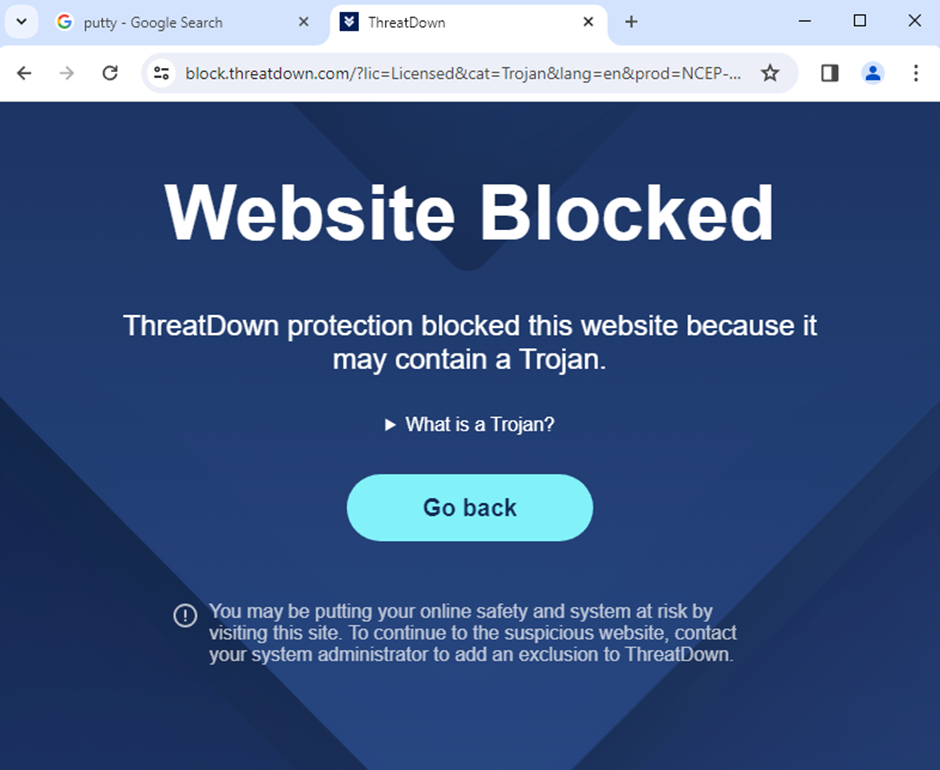
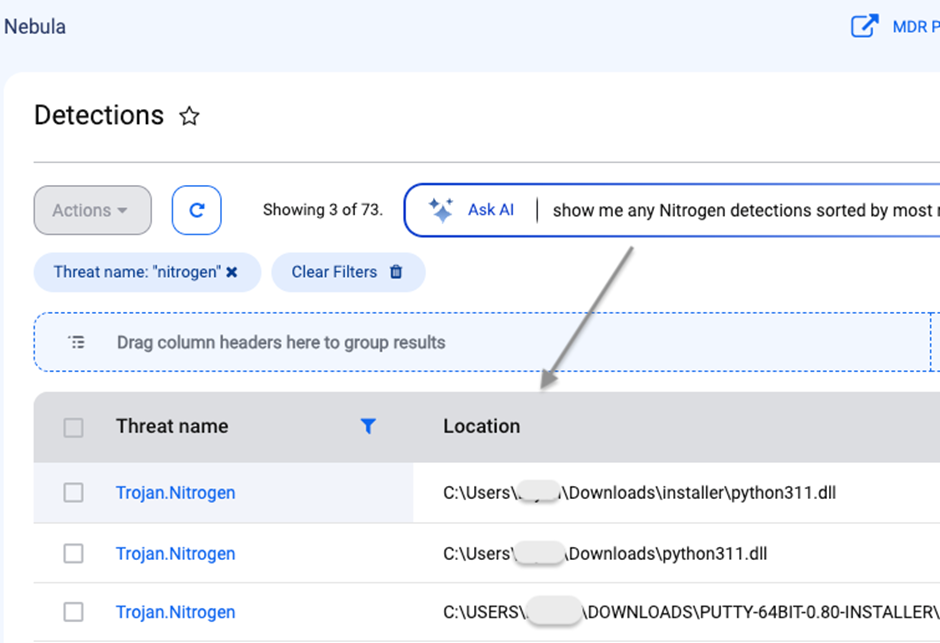
To combat this possibility, cybersecurity firm ThreatDown has blocked these malicious internet sites and finished without users from being tricked into downloading malware.
Their Endpoint Detection and Response (EDR) engine can quarantine the malicious DLL straight away, and gadget administrators can use the AI-assisted engine to appear and review detections.
The prevalence of malvertising as a vector for cyber attacks has highlighted the need for better user training particularly tailored to appreciate and steer definite of such threats.
While phishing practicing for electronic mail threats is acquainted, identical practicing for malvertising is no longer yet well-liked.
To present protection to endpoints from malicious classified ads, neighborhood policies would possibly perhaps per chance per chance even be implemented to prohibit traffic from both vital and lesser-identified ad networks.
Source credit : cybersecuritynews.com


