Hackers Selling Powerful Infostealers on Underground Forums

The role of information stealers (aka stealers) within the cybercrime world has been rising, in accordance with researchers at the SecureWorks Counter Risk Unit (CTU).
Whereas threat actors accomplish use of them to keep discontinuance the next data from the networks and computer programs that are compromised or breached:-
- Login credentials
- Monetary tiny print
- Private data
- System data
Infostealers are recurrently deployed onto computer programs and devices through assorted capability, at the side of:-
- Phishing assaults
- Compromised net sites
- Download of malicious tool
By utilizing these above-mentioned TTPs, the threat actors install the information stealer onto the procedure’s system and set apart unauthorized access to soundless data.
Infostealers, as soon as put in, price powerful efficiency by executing and exiting . Interior a short runtime of seconds to minutes, these malicious programs total the assortment and transmission of stolen data.
Infostealers on Underground Boards
The provision of infostealers extends to a subscription-based mostly mannequin, with prices assorted from $50 to larger than $1,000 USD per month.
These subscriptions grant users access to a C2 server operated by the developer, enabling the execution and keep watch over of the stealer.
The infostealer provider typically affords assorted toughen functions, enabling users to with ease access, get, and share the stolen data through a few channels.
Additionally, self-hosted stealer reveal and keep watch over (C2) servers are equipped individually as a one-time buy, offering users with more keep watch over over their operations.
Interior underground boards, threat actors convene in a collaborative ambiance to engage in discussions concerning ongoing tasks, request of enhancements for his or her instruments, and offer reports of malware.
These boards aid as a shared verbalize for cybercriminals to alternate data, share abilities, and search data from enhancements to their malicious activities.
These boards highlight the organized and interconnected nature of the cybercrime neighborhood, fostering innovation and cooperation of their illicit endeavors.
Underground boards comprise subforums and sections encompassing various matters alongside administrative domains for management, at the side of if truth be told goal appropriate marketplaces with strict regulations for selling illicit objects esteem infostealers.
Underground boards, marketplaces, and assorted on-line platforms cater to threat actors seeking stealer logs, offering them with a technique to develop necessary sources and data esteem:-
- Credentials
- Monetary data
- Private data
- Banking tiny print
- Cryptocurrency wallets
- Other soundless data
Marketplaces offering such sources are recurrently accessible completely through Tor or the I2P (Invisible Files superhighway Mission) anonymity products and companies, as this ensures the privateness and anonymity of contributors.
These platforms enforce stringent tips and regulations, dictating the permissible kinds of information that will additionally be exchanged internal their confines.
Mediums and Market places
Here below we absorb mentioned your total long-established marketplaces that the threat actors most search data from:-
- Russian Market
- Genesis Market
- 2easy
- Telegram
- RaidForums
Infostealer variants
Here below, we absorb mentioned your total identified infostealer variants:-
- RedLine
- Raccoon
- Vidar
- Taurus
- Rhadamanthys
- Command-subsidized stealers
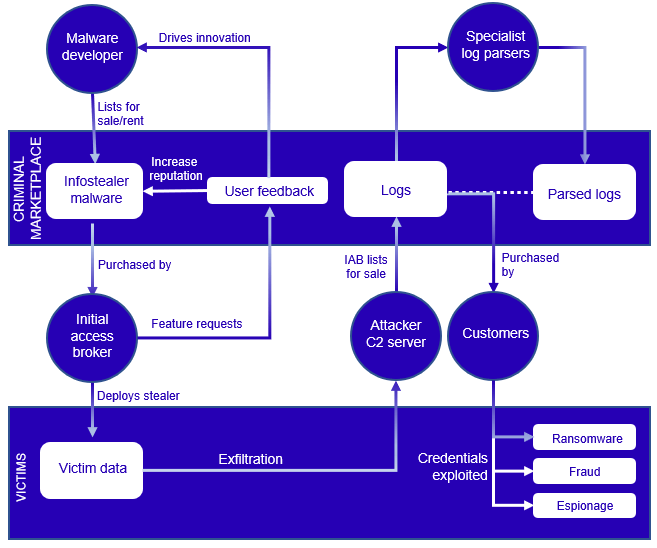
The ecosystem of the Infostealer
The same to the broader cybercriminal ecosystem, the efficient advent and implementation of infostealers depend on a various location of expert contributors fulfilling assorted roles and duties.
The development and deployment of these malicious programs necessitate abilities across assorted areas.
Key contributors within the cybercrime ecosystem inquisitive about the come and distribution of infostealers are:-
- Builders
- Initial access brokers (IABs)
- Customers.
The emergence of MaaS (Malware-as-a-Carrier) operations has severely lowered the technical boundaries for of us who’re seeking entry into the cybercrime panorama.
Staunch through Secureworks’ incident response engagements in 2022, stolen credentials played a prominent role, emphasizing the severity of the discipline.
Infostealer malware gifts a gigantic and tangible threat to contributors and organizations alike, underscoring the necessity for sturdy cybersecurity measures.
As time progresses, this verbalize malware variant continues to conform and repeat heightened levels of sophistication, posing challenges for victims in terms of detection and elimination.
Mitigating this threat requires contributors and organizations to adopt a proactive methodology to securing their programs. To keep sooner than emerging threats, it is needed to enforce sturdy security measures and steps esteem:-
- Guarantee that to use sturdy passwords.
- Frequently change tool.
- Frequently change the system.
- Guarantee that to permit auto-updates.
- Guarantee that to epmply multi-component authentication.
- Guarantee that to keep urged about cybersecurity finest practices.
Source credit : cybersecuritynews.com


