Hackers Use TMChecker Remote Access Tool to Attack Popular VPN & Mail Servers
.webp)
A brand contemporary utility has surfaced on the Darkish Web, signaling a shift in cybercriminals’ solutions for gaining unauthorized remote fetch entry to to company networks.
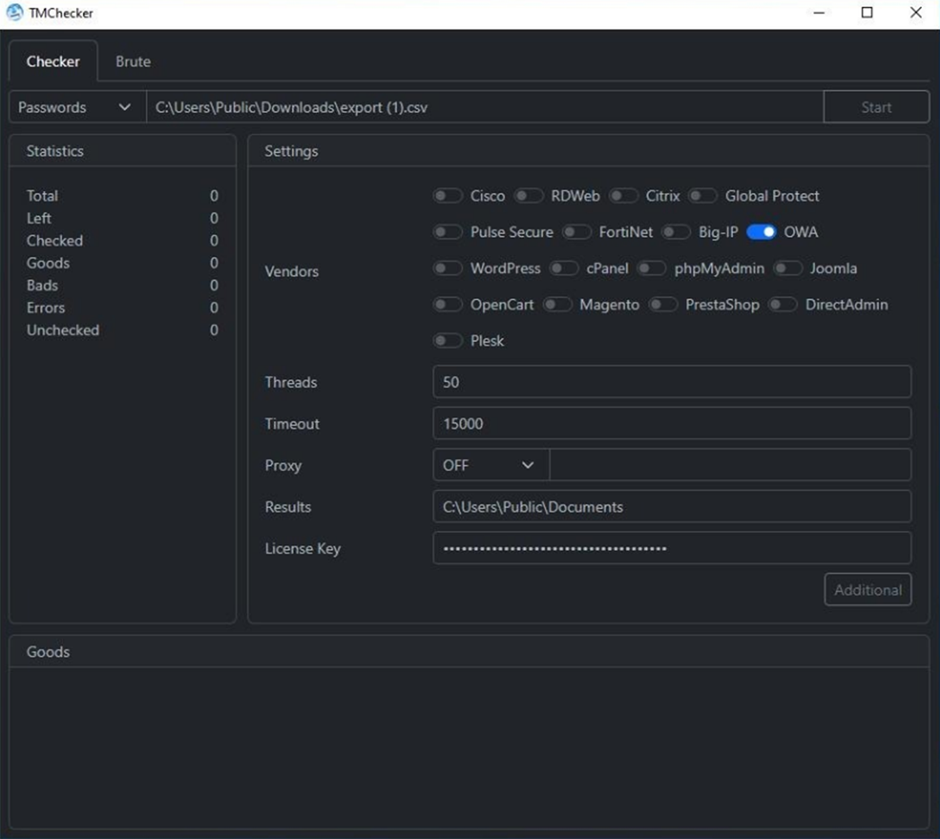
TMChecker, a utility honest no longer too long ago identified by ReSecurity, is designed to attack remote-fetch entry to services and in model e-commerce functions.

It combines company fetch entry to login checking capabilities with a brute-force attack equipment.

Developed by a threat actor identified as “M762” on the XSS cybercrime forum, TMChecker is equipped on a month-to-month subscription foundation for $200.
This utility is a step sooner than its counterparts like “ParanoidChecker,” focusing on company remote fetch entry to gateways, assuredly the principle intrusion vectors for ransomware infections and other excessive-level assaults.
In accordance with a legend by ReSecurity, TMChecker helps 17 a entire lot of services, in conjunction with comparatively comparatively about a VPN solutions, enterprise mail servers, database management tools, and e-commerce platforms.
Incident in Ecuador: A Case Watch
A well-known incident bright TMChecker change into once focusing on an electronic mail server of a authorities organization in Ecuador (gob. ec).
This tournament underscores the utility’s effectiveness in compromising actual credentials to company VPN and electronic mail accounts, which is willing to be archaic by ransomware operators and initial fetch entry to brokers (IABs).
M762’s Telegram Channel: A Hub for Cybercriminals
The gloomy-hat developer at the support of TMChecker, M762, operates a Telegram channel with over 3,270 subscribers.
Whereas it’s unclear what number of of those subscribers are energetic possibilities, the channel’s following presents insight into the profitability of this adversarial Tool-as-a-Carrier (SaaS) mannequin.
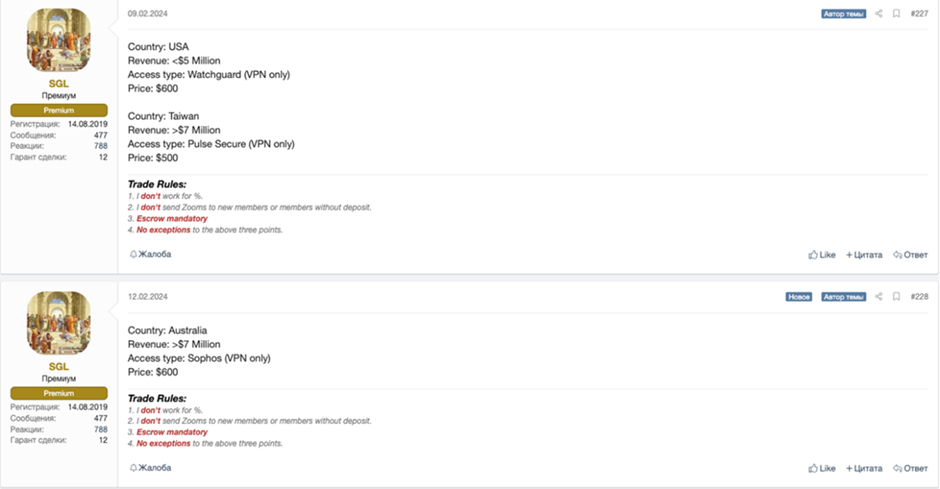
TMChecker’s intensive targets vary from VPN gateways and web hosting administration panels to e-commerce engines like Magento and PrestaShop.
This mammoth focusing on spectrum indicates the utility’s ability to compromise comparatively comparatively about a programs, making it a flexible asset for cybercriminals.
Significance: The Upward thrust of Human-Operated Ransomware Attacks
The emergence of TMChecker aligns with the originate bigger in human-operated ransomware assaults, as reported by Microsoft.
These assaults have the energetic abuse of remote monitoring and management tools, allowing hackers to traipse away at the support of less evidence compared to computerized assaults.
The model is anticipated to continue in 2024, with ransomware actors attempting for to maximise returns by working for a entire lot of gangs.
The creation of TMChecker represents a main threat to organizations, significantly in the context of company mergers and acquisitions (M&A).
With the utility’s capacity to lower the boundaries to entry for cybercriminals, the private sector must bolster its cyber-due diligence processes.
As cybercriminals continue to refine their tooling for remote fetch entry to compromise, organizations must remain vigilant and proactive in their cybersecurity efforts to offer protection to against these evolving threats.
With Perimeter81 malware safety, which that you must perhaps perhaps per chance block malware, in conjunction with Trojans, ransomware, spyware and adware, rootkits, worms, and zero-day exploits. All are incredibly wicked and can wreak havoc for your network.
Discontinue updated on Cybersecurity info, Whitepapers, and Infographics. Notice us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


