Hackers Using Fake Certificates to Infiltrate Corporate Networks

Utilizing inaccurate certificates, attackers kill unauthorized catch admission to to company network resources.
Attackers utilize such certificates to trick the Key Distribution Center (KDC) to catch into the aim firm’s network.
Shadow Credentials are an example of such an assault. This methodology enables an attacker to take over an AD particular person or computer account.
Certificates-essentially essentially based fully TGT- Requests
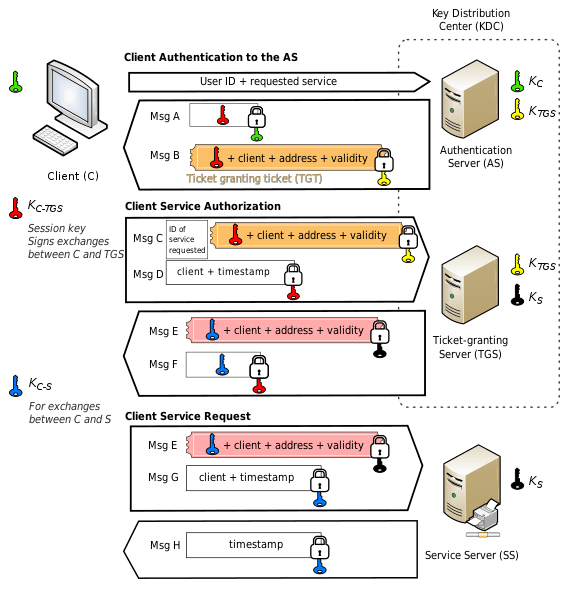
In Kerberos authentication, a Label Granting Label (TGT) is an particular particular person authentication token issued by the Key Distribution Center (KDC).
A key distribution center (KDC) in cryptography is a system that’s guilty for offering keys to the customers in a network that shares peaceable or private files.
TGT is broken-all the most effective device down to request catch admission to tokens from the Label Granting Provider (TGS) for particular resources/techniques joined to the domain.
Really, a TGT is proof of profitable particular person authentication, in overall by password.
The alternate capability to catch TGT is by utilizing a certificate. The KDC need to believe the offered certificate, and the certificate need to open as a lot as the enviornment requested in the TGT.
The fashion is named Public Key Cryptography for Preliminary Authentication (PKINIT).
Having Active Checklist Certificates Providers and products (AD CS) in the corporate network to squawk certificates for domain customers would in actuality perform it rather easy to position up authentication.
Nonetheless, not all company networks have AD CS. The msDS-KeyCredentialLink attribute used to be invented for this motive, where the certificate would perchance be written.
(msDS-KeyCredentialLink attribute broken-all the most effective device down to link an RSA key pair with a pc or particular person object in notify to authenticate with acknowledged key pair towards the KDC to construct up a Kerberos TGT)
As a result of this truth KDC will believe this certificate and squawk a TGT. But the difficulty is the enviornment that writes the msDS-KeyCredentialLink attribute to some object might perchance also have the ability to catch a trace for this object.
Illustration of the Assault
Take hold of into consideration logan_howard, having write catch admission to in the AD domain, writes a public key to msDS-KeyCredentialLink attribute for a website online controller object using Whisker.
Whisker is a C# instrument for taking over AD customers and computer accounts by manipulating their msDS-KeyCredentialLink attribute.
The topic receives the TGT issued to the domain controller.
With the TGT, the enviornment receives a TGS trace to synchronize password files in the domain.
The attacker then “synchronizes” the hash from the domain administrator account to impersonate the administrator for the motive of gaining catch admission to to files and intriguing laterally within the corporate network.
As a fraction of the analysis, Securelist will get the KDC to believe a explicit certificate, including stolen or solid ones. This triggered tournament 4768 on the domain controller.
This tournament might perchance maybe presumably own artifacts from the certificate broken-down for authentication, with three fields: CertIssuerName, CertSerialNumber, and CertThumbprint.
Kaspersky created quite lots of TGT request events consistent with a solid certificate generated using Whisker.
The assault is barely efficient and is prone to be detected handiest when a solid certificate is broken-down. “Files of the infrastructure (ideally including a listing of all energetic keys) and monitoring will wait on the safety educated in this,” acknowledged Securelist, a cybersecurity and analysis firm.
Source credit : cybersecuritynews.com


