Hackers Using Malware-Driven Scanning Attacks To Pinpoint Vulnerabilities
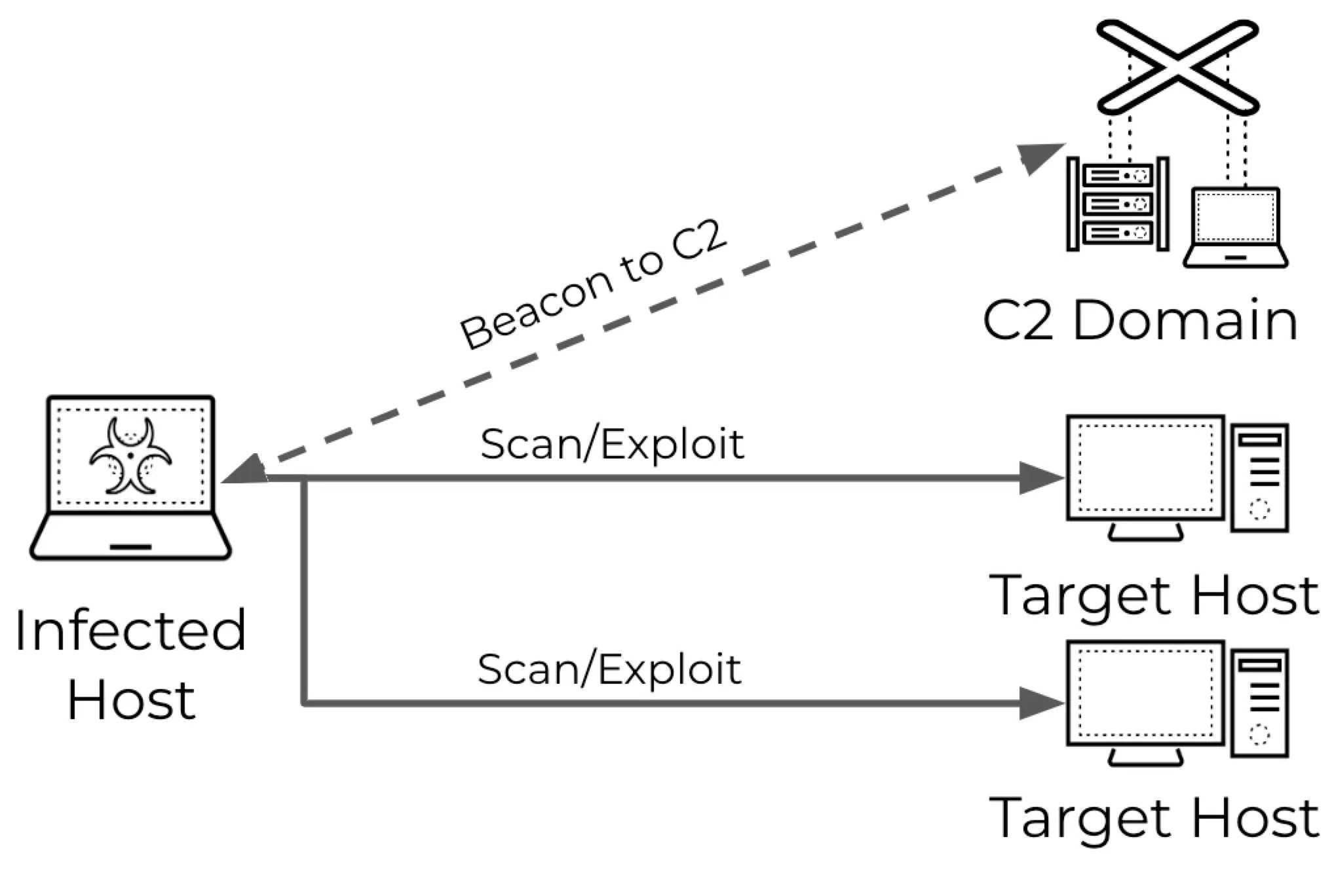
Attackers are now the usage of malware-contaminated devices to scan procedure networks as a replacement of straight away scanning them. This formula helps them to veil their identification, evade geographical restrictions (geofencing), and grow their botnets.
Compromised hosts provide extra sources to open expansive-scale scans than a single attacker machine might perhaps perhaps perhaps organize. Systems can effectively detect established and unusual scanning patterns by examining scan traits love request volume and matching them with diagnosed menace signatures.

Attackers convey scanning ways to probe procedure networks for weaknesses, which is willing to title launch ports, utility vulnerabilities, and even working methods.
By exploiting these vulnerabilities, attackers can rep unauthorized procure entry to or disrupt methods.

Within the instance, the attacker scans random-college.edu the usage of an HTTP POST request to title the MOVEit vulnerability (CVE-2023-34362), which is willing to manual to a compromise if winning.
Inspecting website online visitors logs across extra than one networks has identified a indispensable lengthen in scanning convey concentrating on likely vulnerabilities.
One example eager an unusually excessive request volume (7,147 occasions in 2023) to endpoints associated with the MOVEit vulnerability (CVE-2023-34362).
The requests seemed sooner than the vulnerability was publicly diagnosed, and the telemetry further revealed over 66 million requests in 2023 that will perhaps perhaps perhaps be linked to scanning.

Attackers were seen the usage of unusual URLs within their exploits to avoid security measures.
Palo Alto Networks identified two such cases: a Mirai variant the usage of “103.245.236[.]188/skyljne.mips” and an are attempting to milk Ivanti vulnerabilities with “forty five.130.22[.]219/ivanti.js”.
In both instances, the scanning requests preceded the detection of subsequent malicious payloads, highlighting the importance of proactive scanning detection for neatly timed menace mitigation.
Attackers convey malware to hijack contaminated devices and switch them into scanning machines by communicating with attacker-managed servers for directions and scanning procedure domains upon receiving a scan insist.

The formula permits attackers to evade detection and convey the sources of compromised devices for expansive-scale vulnerability scanning, the put the targets can fluctuate looking on the attacker’s wishes, that are targeted assaults in opposition to particular entities or stylish scanning to infect extra devices.
A Mirai variant exploit takes excellent thing a couple of Zyxel router vulnerability that does no longer take a look at inputs totally ample to get a malicious file and reproduction itself, which was weak in a disbursed attack the put 2,247 devices scanned 15,812 targets.
The botnets wait on incorporating unusual vulnerabilities and defenders prefer to patch vulnerabilities and change detection methods to dam unusual variants, while monitoring scanning activities across extra than one networks can support detect unusual scanning patterns extra hasty.

Ivanti Vulnerability Scanning:
Chained vulnerabilities (CVE-2023-46805, CVE-2024-21887) were honest no longer too prolonged ago weak in an attack marketing campaign in opposition to Ivanti merchandise, the put the attackers weak direction traversal in a GET request to procure round authentication for a direction that had a insist injection vulnerability.

It allowed them to invent commands and doubtlessly rep procure entry to to inclined methods by the usage of the attack to harvest the IP addresses of likely targets from a DNS logging provider.
Attackers procedure frequent technologies love routers, internet utility frameworks, and collaboration instruments, as files displays stylish vulnerability scans concentrating on routers, in conjunction with fresh assaults on Ubiquiti EdgeRouters and Cisco/NetGear routers by Russian and Chinese hackers, which would be no longer restricted to particular router producers.
Secure your emails in a heartbeat! To find your ideal email security vendor, Take a Free 30-Second Assessment.
Source credit : cybersecuritynews.com


