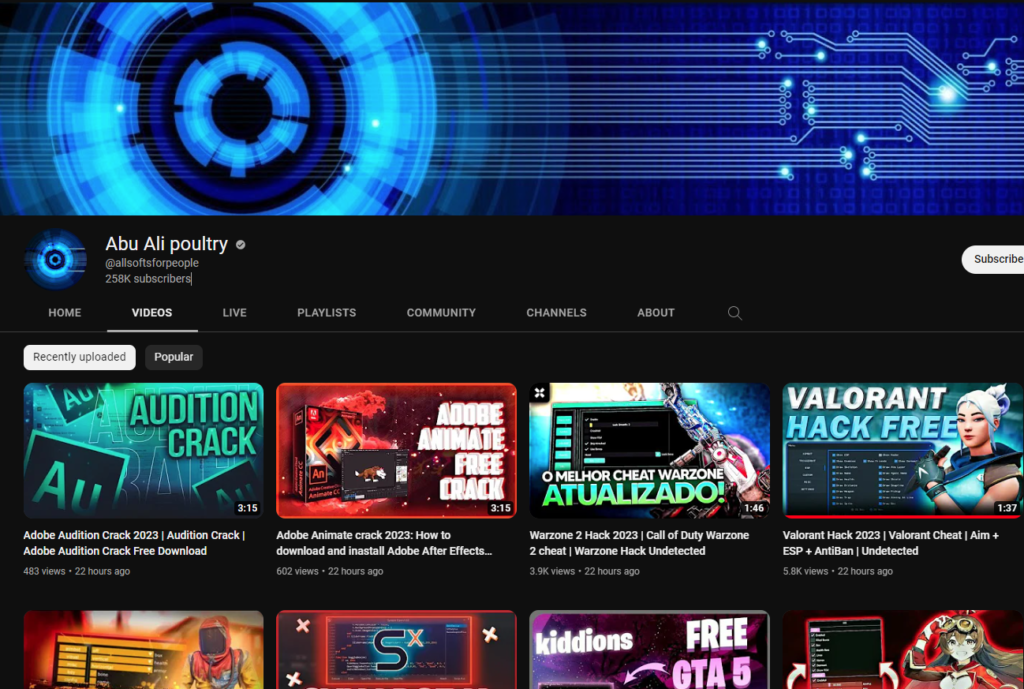
Hackers Using YouTube as a Malware Distribution Platform Via Hacked YT Channel

Morphisec Possibility Labs researchers dangle honest at the moment uncovered a sneaky loader called “in2al5d p3in4er” (Invalid Printer) that delivers Aurora data stealer malware via YouTube videos.
Utilizing an evolved anti-VM technique, the in2al5d p3in4er loader, constructed with Embarcadero RAD Studio, particularly targets endpoint workstations.
Late in 2022, Aurora seemed on the threat landscape for the first time, and it’s an data stealer written in Lag programming language.
Abusing YouTube as a Distribution Platform
Aurora is a commodity malware dispensed via untrue cracked instrument download sites and YouTube videos to other threat actors having a gape to use it.
YouTube has develop to be a elegant distribution platform for threat actors having a gape to spread malware to come by admission to sensitive data.
Due to the its mass recognition, YouTube has develop to be one of many first decisions for threat actors.
Hackers dangle came upon a unique solution to spread malware by hacking unique YouTube accounts and posting videos with malicious links or downloads via those compromised accounts or channels.
Whereas the hackers also use optimized SEO tags to take the visibility of videos in search results, that would possibly presumably presumably also magnify the clicking-via rate (CTR).
Since threat actors are actively producing elegant income by stealing YouTube accounts for a price, these services and products are genuinely actively marketed by hackers in several underground forums and marketplaces.
Man made intelligence (AI) is broken-down by the carrier to generate videos, making it more uncomplicated and faster to carry out budget-backed bid material that looks convincing.
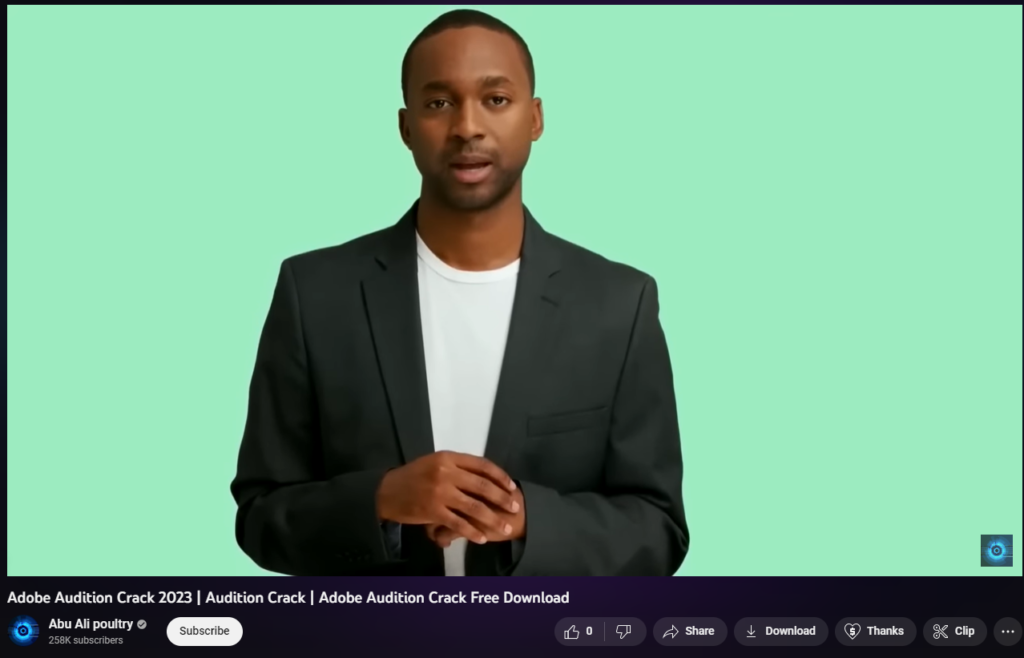
Victims who click on the links in YouTube video descriptions are taken to untrue web sites that trick them into downloading malware disguised as reliable instrument.
To seem reliable, these untrue web sites use the following issues to carry out the looks that they’re staunch:-
- Identical URLs
- Identical trademarks
- Identical branding

These decoy web sites persuade customers to download functions containing malware and trick them into getting into their sensitive or private data.
Technical diagnosis
Morphisec asserted that this loader assessments the vendor ID of a diagram’s graphics card and terminates itself if the cost doesn’t match a listing of well-liked IDs, which involves:-
- AMD
- Intel
- NVIDIA
Utilizing one plan called “activity hollowing,” the loader decrypts the final payload and injects it into a valid activity called “sihost.exe.”
Whereas injecting the final payload into the reliable activity, the loader dynamically decrypts the total required Windows API and uses the XOR key ‘in2al5d p3in4er‘ to decrypt the API names.
The loader employs Embarcadero RAD Studio to carry out executable data that would possibly presumably presumably be broken-down on diversified platforms, which helps it evade detection by safety instrument.
Malware loaders esteem in2al5d p3in4er are the constructing blocks of an attack, offering an preliminary foothold between the attacker and the compromised diagram.
They motivate as a crucial first stage, facilitating the shipping of extra complex and detrimental payloads.
The threat actors are guilty for in2al5d p3in4er malware are leveraging social engineering tactics and the use of them in combination with the malware to carry out a first-rate influence.
They aim unique YouTube accounts to redirect the viewers to untrue and reliable-having a gape web sites.
To terminate attacks from in2al5d p3in4er, instructing workers about figuring out social engineering schemes is mandatory.
Building Your Malware Protection Approach – Web Free E-E book
Moreover, Be taught
New DDoS Botnet Malware Infecting Windows, Linux, and IoT Devices
New Darkish Net Websites Permits Hackers to Embed Malware to Legit Android Apps
FFDroider Stealer Malware Steals Fb, Instagram & Twitter Yarn Credentials
Source credit : cybersecuritynews.com

