Internal Communication Gaps Exposes Organizations to Cyber Attacks
.png)
The alignment between security groups and govt administration is crucial.
Then again, a prime dialog gap interior organizations is increasingly turning into vulnerable, exposing them to delicate cyber threats.
This downside is highlighted in the 2024 Global CISO Chronicle by Dynatrace, which underscores the challenges and attainable dangers constructing from these interior misalignments.
Combine ANY.RUN in Your Company for Effective Malware Prognosis
Are you from SOC, Probability Review, or DFIR departments? If that is so, you would be part of an on-line neighborhood of 400,000 fair security researchers:
- Precise-time Detection
- Interactive Malware Prognosis
- Easy to Be taught by Contemporary Safety Team contributors
- Gain detailed stories with maximum records
- Field Up Virtual Machine in Linux & all Windows OS Variations
- Interact with Malware Safely
In record so that you just can take a look at all these components now with fully free gain entry to to the sandbox:
The file reveals that 83% of Chief Recordsdata Safety Officers (CISOs) imagine their boards and CEOs desire a greater understanding of their security posture to successfully assess enterprise threat and compliance necessities.

This lack of workmanship can lead to inadequate preparedness in opposition to cyber threats, as strategic decisions might per chance per chance well now not fully imagine the cybersecurity implications.
One of the most predominant components is the technical jargon in general used by security groups, which can alienate non-technical senior executives.
The Dynatrace file emphasizes the need for CISOs to translate cybersecurity challenges into enterprise impacts to capture the C-suite’s attention and foster a custom of shared accountability for security.
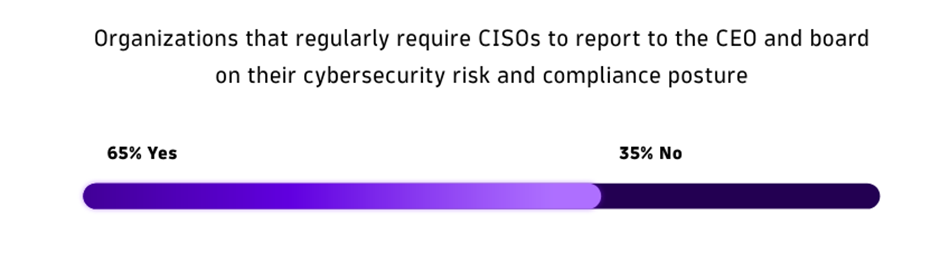
The Industry Affect of Cyber Assaults
Cyber assaults can devastate organizations, from financial losses attributable to interrupted operations to extreme reputational wound if buyer records is compromised.
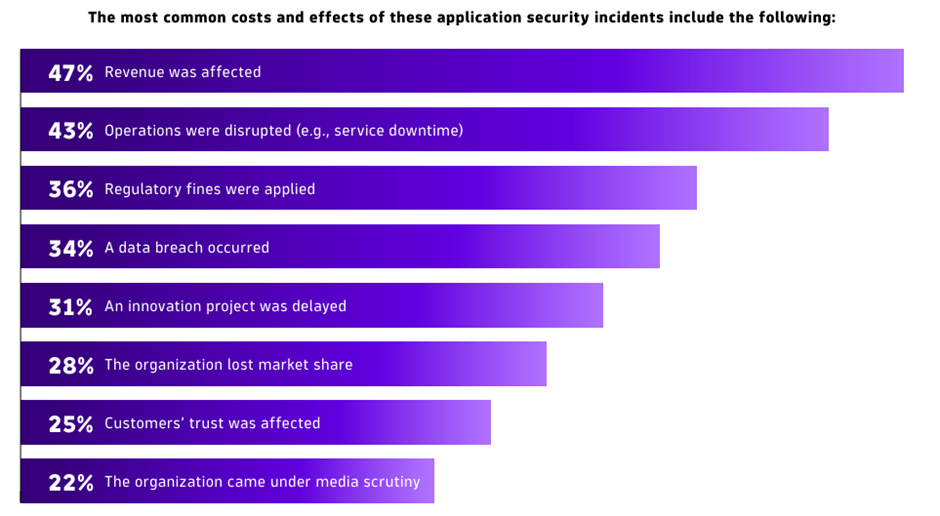
The file notes that 72% of organizations possess skilled a security incident connected to their applications in the previous two years, highlighting the extreme nature of sturdy cybersecurity measures.
Strategic Ideas
To bridge the dialog gap, the file suggests so much of suggestions:
- Enhanced Reporting: Safety leaders have to accrued refine their reporting mechanisms to assemble particular, actionable insights that resonate with the C-suite’s strategic wishes.
- Training and Engagement: Traditional workshops and simulations can motivate demystify cybersecurity for non-technical executives, making them more engaged in decision-making.
- Unified Safety Framework: Adopting a comprehensive security framework that integrates assorted sides of cybersecurity can motivate demonstrate a unified observe of dangers and defenses, making it more uncomplicated for the board to contend with and attend major measures.
As cyber threats grow more delicate, the need for strategic alignment interior organizations turns into more extreme.
By closing the interior dialog gaps, organizations can guarantee a more strong defense in opposition to cyber threats, conserving their belongings and reputation in the digital age.
Dynatrace file serves as a indispensable be-cautious demand organizations worldwide.
It highlights the urgent need for strategic alignment between security groups and govt administration to crimson meat up cybersecurity measures successfully.
Because the digital landscape continues to conform, so must the suggestions we employ to guard our most priceless belongings from cyber threats.
Source credit : cybersecuritynews.com

