Kimsuky APT Hackers Dropping Malware Via Weaponized CHM (MS Compiled HTML) Files

AhnLab Security Emergency Response Heart (ASEC) researchers came at some stage within the Kimsuky APT neighborhood’s most modern strikes, at some stage in which attackers have been the consume of CHM recordsdata to distribute malware to the centered machines, downloading additional scripts or malware to harvest user recordsdata.
Kimsuky is a North Korean direct-backed hacker neighborhood that targets South Korean judge tanks, industry, nuclear vitality operators, and the South Korean Ministry of Unification for espionage purposes. The Kimsuky APT neighborhood has presumably been operating since 2012.
Cyber Security News reported the earlier Kimsuky risk actors’ activities in 2020 when few findings arose and developed the risk neighborhood’s spyware talents and talents.
As per the diagnosis of numerous attacks carried out in Could well well also, ASEC came at some stage in that they’ve faded diversified matters equivalent to cryptocurrency, tax accounting, and contracts in disbursed recordsdata in position of North Korean-linked matters.
Kimsuky APT File Distribution Vector
“CHM malware in distribution generates a fashioned lend a hand window upon execution and performs malicious behaviours throughout the malicious script internal.”
A CHM file is a compressed HTML file that affords lend a hand field topic. It will have text, photos, and hyperlinks.
“It’s not straightforward for users to peep the malicious behaviours, having been deceived with the lend a hand window disguised as a conventional file.”
The support window the user generates takes profit of most modern events or matters in step with which the target discipline works to originate it more legit.
For Example, the lend a hand window generated on the user’s machine would possibly perchance well well presumably also merely hyperlink to a disguised tax investigation return salvage web say or expose to explicit users’ financial transaction pages.
The stolen deepest recordsdata of someone became faded to originate it more legit. In diversified cases, attackers have been the consume of stolen reservation notice small print, cryptocurrency transactions of explicit folks, and family registration of sure folks, ASEC researchers acknowledged.
In such scenarios, users would possibly perchance well well presumably also merely turn out to be the victim and click on the doc to quit the malware.
CHM Malware Behaviour
As soon as the user clicks the CHM file, additional scripts are downloaded to exfiltrate user recordsdata and malware.
BAT and VBS recordsdata had been before all the pieces dropped once CHM carried out, which additional downloaded CAB File.
The CAB file incorporates scripts to exfiltrate user recordsdata and fetch additional malicious recordsdata.
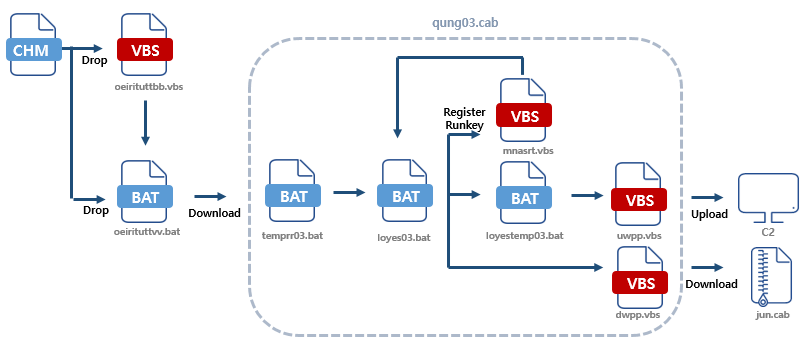
Person recordsdata is aloof through loyestemp03.bat, and uwpp.vbs sends the aloof recordsdata and the PC name to “hxxp://vndjgheruewy1[.]com/uun06/uwpp.php” The risk actor checks the stolen user recordsdata, and easiest when the system is a target of assault uploads additional malicious recordsdata to the Hiss and abet watch over.
If the system is a target, the risk actor uploads recordsdata with the name of the infected PC.
Contaminated PCs many times are trying to catch throughout the script registered to RunKey, and when diversified recordsdata are uploaded, the recordsdata are downloaded.
It then decompresses the downloaded recordsdata throughout the amplify expose earlier than executing them.
“Circumstances of the consume of CHM recordsdata in APT attacks are additionally many times came at some stage in. Users need to fastidiously test the senders of emails and chorus from opening recordsdata from unknown sources.
They’ll also merely aloof additionally device routine PC checks and update their security merchandise to the most modern version.” Researchers warned.
Organize and stable Your Endpoints Efficiently – Free Accept
Indicators of Compromise
b5a873ee6b839cbd03789115fc3ae944
9861999409cdbc1f7c4c1079d348697c
7c7b8dd6dd4ba7b443e84287671f0e79
98764ae00cee9f2cc87530601c159387
d62dcb76fa0fb4b725ea9c8643874ae7
e9e56ee78e019e09d5dbe0bb373adf09
ef58a1326b98feccc90c4d37a8ce2fe2
ae6fdb8945991b587ab790c2121345ce
075160d6c8d82b96d1ae7893761695a6
e5b0430290dc71193b7ea2fc829a9910
Source credit : cybersecuritynews.com


