Lazarus Hacking Group Attack IIS Web Servers to Install Web Shell

The AhnLab Safety Emergency Response Center (ASEC) confirmed fresh assaults on Windows IIS web servers by the nationally supported Lazarus team.
On the total, threat actors exploit susceptible web server versions to install web shells or carry out malicious instructions at some stage in their scans.
Lazarus, a financially motivated hacking team, is believed to fund North Korea’s weapons construction programs whereas also taking part in espionage operations.
Lazarus Targets IIS Servers
Organizations, no subject their size, snarl Windows IIS web servers to host varied websites, at the side of websites, applications, and products and companies cherish Outlook on the Web from Microsoft Alternate.
Since the liberate of Windows NT, this has been one in all possibly the most versatile alternate choices on the market, supporting protocols akin to:-
- HTTP
- HTTPS
- FTP
- FTPS
- SMTP
- NNTP
Within the match of inadequate administration or outdated configurations, servers obtain the doable to encourage as susceptible salvage entry to points for hackers to infiltrate a community.
Symantec previously reported hackers using malware on IIS to carry out instructions undetected, whereas a separate document uncovered the hacking team ‘Cranfly’ using IIS web server logs for unknown malware alter.
The ASD log means that Windows server systems are under assault, with malicious activities going down thru the w3wp.exe route of of the IIS web server.
Lazarus exploits IIS servers thru vulnerabilities or misconfigurations, leveraging the w3wp.exe route of to price files, at the side of a valid ‘Wordconv.exe,’ a malicious DLL (‘msvcr100.dll’), and an encoded file known as ‘msvcr100.dat’ inner the identical folder.
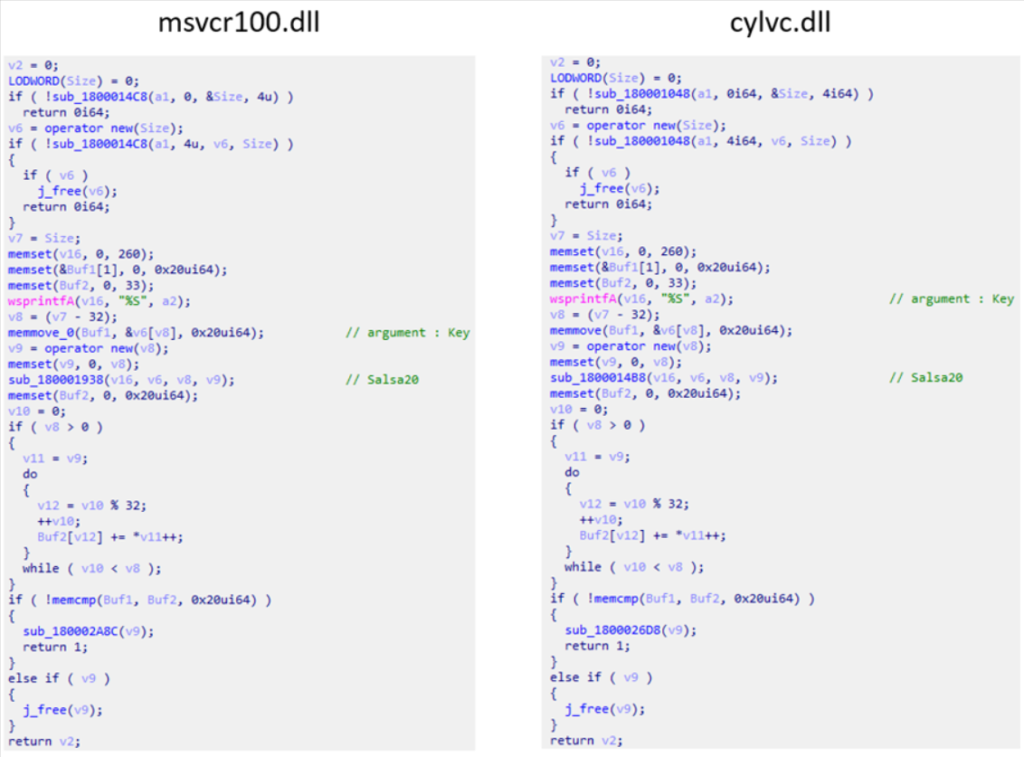
After initiating ‘Wordconv.exe,’ the DLL’s malicious code decrypts the Salsa20-encoded executable from msvcr100.dat, executing it in reminiscence to evade detection by antivirus instruments.
Throughout the second section, Lazarus exploits a Notepad++ plugin to generate a second malware (‘diagn.dll’), which then decodes a modern payload using a mounted key and executes it in reminiscence to steer clear of detection.
The LSASS dumping signifies doable credential theft job, despite the indisputable reality that the explicit motive of the payload stays unknown to ASEC.
After acquiring presumably stolen valid person credentials, the final section of the Lazarus assault alive to community reconnaissance and lateral circulate thru port 3389 (Faraway Desktop).
On the quite quite lots of hand, ASEC has no longer detected any subsequent malicious actions following the attackers’ lateral unfold inner the community.
ASEC advises organizations to show screen for irregular route of execution as a result of Lazarus’ broad snarl of DLL sideloading in their assaults.
As a result of their active world assault campaigns, this highly unhealthy team highlights the importance for corporate security managers to snarl assault ground administration, figuring out susceptible property and prioritizing the utility of possibly the most traditional security patches at any time when feasible.
To forestall the threat team from taking part in activities cherish info exfiltration and lateral circulate, firms might presumably well also mild proactively show screen irregular route of execution relationships, especially pondering the threat team’s predominant snarl of the DLL aspect-loading technique at some stage in preliminary infiltrations, and take preemptive measures accordingly.
Source credit : cybersecuritynews.com

