WP-Members Plugin Expose WordPress Sites To Injection Attacks

A security researcher reported a critical vulnerability within the WP-Participants Membership Plugin that enables attackers to inject malicious scripts and doubtlessly rob over net snort.
Administrators also can rob ultimate thing regarding the unauthenticated saved XSS flaw that changed into contemporary within the X-Forwarded header. To guard their customers, researchers appreciate been rewarded for his or her to blame disclosure.

On March Seventh, the plugin dealer launched a partial patch (v3.4.9.2) and a elephantine repair (v3.4.9.3) quickly after and upgraded to doubtlessly the most recent version to mitigate the threat.
A critical vulnerability (CVSS: 7.2) exists in WordPress’s WP-Participants Membership Plugin versions as a lot as about a.4.9.2, which arises from insufficient sanitization and escaping of the X-Forwarded header.

Malicious attackers can exploit this to inject arbitrary scripts into the database, which then attain on every occasion a user visits the edit user net page.
Whereas a partial repair changed into implemented in version 3.4.9.2, a entire resolution arrived most effective in version 3.4.9.3. Upgrading to doubtlessly the most recent version is a critical to addressing this security threat.
Technical Diagnosis Of The Vulnerability:
An attacker can exploit a unhealthy-characteristic scripting vulnerability in WP-Participants by injecting malicious code into the X-Forwarded header for the interval of user registration.
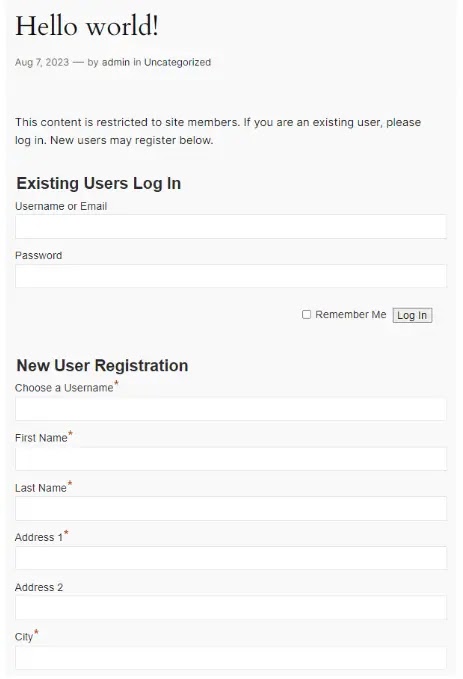
It’s achieveable by intercepting the registration search info from with a proxy and modifying it to comprise the attacker’s script, whereas the vulnerable plugin stores the attacker-offered script because the user’s IP take care of, allowing execution on every occasion that user info is displayed.

The `rktgk_get_user_ip` characteristic in a vulnerable plugin relies on unsanitized HTTP headers (`HTTP_CLIENT_IP` or `HTTP_X_FORWARDED_FOR`) to discover a user’s IP take care of.
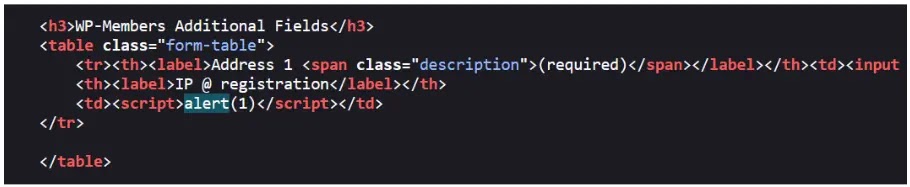
It permits attackers to inject malicious scripts into these headers, that are then saved because the user’s IP and when an administrator views or edits this kind of user legend, the injected script executes within the administrator’s browser session attributable to the mirrored XSS vulnerability.
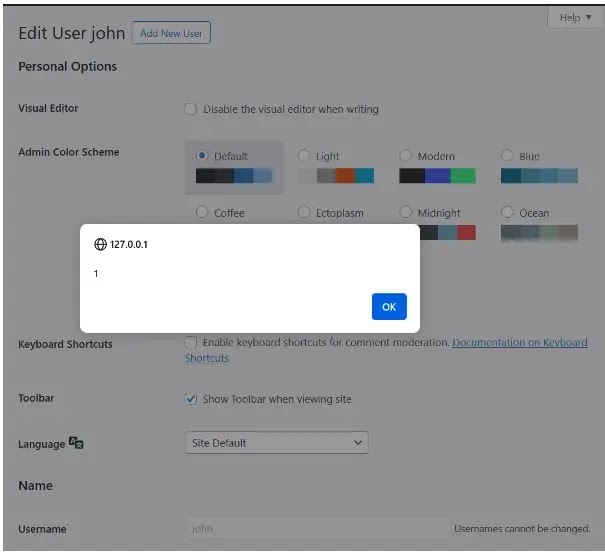
The administrator legend also can very effectively be compromised, malicious customers also can very effectively be created, or customers also can very effectively be redirected to net snort that are execrable.
Wordfence contacted the dealer and coordinated a patch; whereas version 3.4.9.2 addressed segment of the jabber, contemporary payloads also can aloof be caused.
Version 3.4.9.3 completely patched the vulnerability; updating the plugin and advising customers to part this info with others who tell the plugin is recommended.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide
Source credit : cybersecuritynews.com


