Microsoft .NET Framework & Visual Studio Flaw Let Attackers Write or Delete Files

A vulnerability, CVE-2023-36049 has been identified within the Microsoft .NET Framework and Visible Studio, posing a serious menace to the integrity of FTP servers.
If exploited, this flaw will also allow attackers to write or delete recordsdata, compromising the protection of functions and records.

The .NET Framework, a cornerstone of device pattern on Microsoft Windows, facilitates the creation and execution of functions within a managed execution ambiance.
Nonetheless, a flaw in its fabricate linked to going through FTP instructions has opened a door for cyber attackers.
FTP, or File Switch Protocol, is a venerable community protocol for transferring computer recordsdata between a consumer and server on a computer community.
It operates on a dual-connection system, one for instructions and the thoroughly different for records transfer.
The vulnerability stems from the .NET Framework’s contaminated individual input validation, particularly in how FTP narrate parameters and FTP URI requests are processed.
FTP instructions salvage the following syntax:
Vulnerability Unveiled
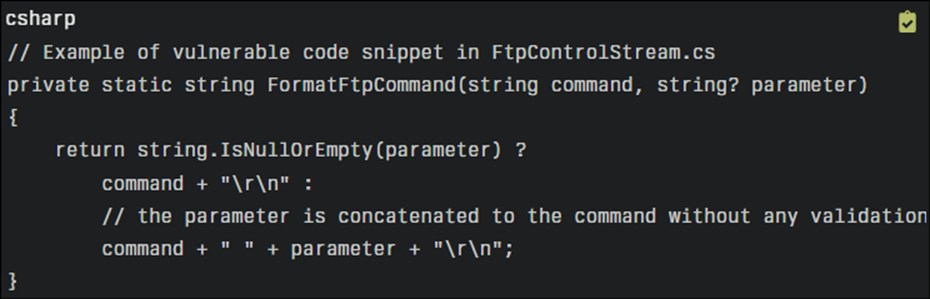
A detailed evaluation finds that the flaw is attributable to the .NET Framework’s FtpControlStream class, which inadequately validates FTP narrate parameters, permitting attackers to inject malicious instructions.
For instance, when going through parameters that consist of Carriage Return Line Feed (CRLF) characters, the system fails to properly sanitize the input, ensuing in probably unauthorized file operations.
The Pattern Micro Overview Personnel recently uncovered a vulnerability in .NET Framework and Visible Studio, permitting privilege escalation.
Are you from SOC and DFIR groups? – Join With 400,000 neutral Researchers
Malware evaluation will even be rapid and straightforward. Appropriate let us demonstrate you the ability to:
- Work along side malware safely
- Pronounce up digital machine in Linux and all Windows OS variations
- Work in a team
- Fetch detailed stories with most records
Whereas you treasure to salvage to check all these system now with fully free procure entry to to the sandbox: ..
Justin Hung and Yazhi Wang of the team salvage detailed the pain in a document throughout the Pattern Micro Vulnerability Overview Provider.
The vulnerability has since been patched. Attackers can exploit this vulnerability by sending specially crafted requests to FTP servers.
A hit exploitation will also allow unauthorized americans to write or delete recordsdata on the server, potentially ensuing in records loss, records corruption, or unauthorized procure entry to to nonetheless records.
The assault vector is terribly referring to for functions that rely on the .NET Framework for FTP operations.
Given the frequent utilize of the .NET Framework in endeavor environments, this vulnerability has a foremost probably affect.
Mitigation and Response
Microsoft has replied to this serious vulnerability by releasing a patch.
The update addresses the flaw by bettering the validation route of for FTP narrate parameters and URI requests.
Administrators and builders need to negate this patch promptly to present protection to their systems from probably attacks.
For these unable to negate the patch straight, a transient mitigation technique comprises refusing FTP URIs from untrusted sources and filtering FTP web page visitors to detect and block suspicious assert.
Monitoring FTP web page visitors for a whole lot of instructions despatched in a single packet can wait on name attempts to utilize this vulnerability, though this suggests will also yield incorrect positives in celebrated web page visitors.
The invention of this vulnerability underscores the importance of rigorous input validation in device pattern.
Asserting the protection of device frameworks and functions as cyber threats evolve is paramount.
Customers and directors are entreated to negate the supplied patch and apply most efficient practices for community safety to safeguard against probably exploits.
You would possibly maybe block malware, along side Trojans, ransomware, spyware and adware, rootkits, worms, and nil-day exploits, with Perimeter81 malware protection. All are incredibly tainted, can wreak havoc, and difficulty your community.
Finish up-to-the-minute on Cybersecurity news, Whitepapers, and Infographics. Note us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


