Microsoft Observed Huge-Surge In Attacks Targeting Internet-Exposed OT Devices In WWS
%20(1).webp)
Microsoft has reported a principal broaden in cyberattacks focusing on internet-uncovered, poorly secured operational abilities (OT) devices.
These attacks have in particular focused on the US’ water and wastewater systems (WWS).

A form of nation-backed actors, in conjunction with the IRGC-affiliated “CyberAv3ngers” and pro-Russian hacktivists, were implicated in these attacks.
Vulnerability of OT Systems
OT systems procure an eye on severe genuine-world processes and are prevalent across comparatively just a few industries, in conjunction with building HVAC systems, water provide, and energy vegetation.
These systems prepare a ought to-have parameters equivalent to tempo and temperature in industrial processes.
A cyberattack on an OT system can switch procure an eye on over these parameters to attackers, doubtlessly causing malfunctions or total system outages.
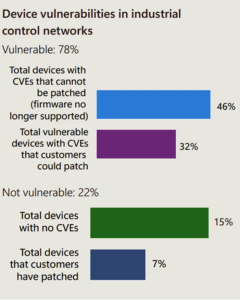
In accordance with Microsoft studies, Many OT devices are at as soon as linked to the internet, making them without disclose discoverable by attackers the expend of internet scanning tools.
Unlucky security configurations, equivalent to old passwords or old-customary instrument with known vulnerabilities, extra exacerbate the threat.
The attractiveness of OT systems and the benefit of exploiting old configurations were demonstrated correct by procedure of the Israel-Hamas war, where a lot of OT-focused actors broadcasted their attacks on Israeli companies by procedure of Telegram channels.
Excessive-Profile Case: Aliquippa Water Plant Attack
In November 2023, a high-profile cyberattack focused the Aliquippa water plant in Pennsylvania.
The attack, attributed to the IRGC-affiliated “CyberAv3ngers,” resulted within the outage of a tension guidelines pump and the defacement of the instrument with the attacker’s emblem.
The US Department of Treasury sanctioned officials within the Iranian Islamic Innovative Guard Corps Cyber-Digital Notify (IRGC-CEC) about the attack.

The Aliquippa incident is section of a broader pattern of attacks on OT systems.
The Cybersecurity and Infrastructure Security Agency (CISA) launched advisories in December 2023 and Also can honest 2024, highlighting the overall profile of focused OT systems:
Web-uncovered with old signal-in configurations. These advisories emphasized the need for improved security features to give protection to in opposition to identical attacks.
To mitigate the threat of cyberattacks on OT systems, Microsoft recommends the next measures:
- Undertake Total Security Solutions: Implement solutions adore Microsoft Defender for IoT to show screen and give protection to OT devices.
- Enable Vulnerability Assessments: Name and patch unpatched devices the expend of tools adore Microsoft Defender Vulnerability Administration.
- Decrease Attack Ground: Gain rid of pointless internet connections to OT devices and terminate pointless birth ports.
- Implement Zero Belief Practices: Educate network segmentation to stop lateral circulate by attackers and isolate OT devices from IT networks.
The surge in cyberattacks on OT devices underscores the urgent need for improved security features.
Organizations ought to adopt comprehensive security solutions, conduct in style vulnerability assessments, and enforce only practices to give protection to their severe infrastructure from cyber threats.
Source credit : cybersecuritynews.com

