Network Security Checklist – Complete Guide To Protect Enterprise Networks (2024)
Network Security Checklist – Complete Manual To Shield Endeavor Networks (2024)
Network security is paramount in lately’s digital landscape, the put organizations face extra and further sophisticated threats.
This handbook gifts an extensive Network Security checklist with examples to imply you may presumably perhaps also place sturdy protection and gash again vulnerabilities.
Network Security Musts: The 7-Level Checklist – Gather Free – E-Ebook

Network Security and Risks 2024
Network security is major for digital info and system protection. Defending networks and info against unauthorised win exact of entry to, abuse, and misfortune requires many steps. Network security is repeatedly changing, with novel threats and difficulties. Key community security factors and risks:
Cyber Threats: Malware, ransomware, phishing, and DDoS assaults can purpose networks. These dangers can location off info breaches, financial losses, and impress misfortune.
Instrument and Hardware Vulnerabilities: Networks use susceptible plan and hardware. Attackers can leverage these vulnerabilities to accomplish win exact of entry to or disrupt companies. In fashion updates and patches are wished to fix these vulnerabilities.
Insider threats: Organizational insider threats can potentially pose a security misfortune. Insiders with community win exact of entry to can purposefully or inadvertently violate security. Staunch win exact of entry to restrictions and internal job monitoring are major.
Rising Technologies: Cloud computing, IoT, and AI present novel security risks. These applied sciences are extra and further included into community infrastructures, making security wanted.
Compliance and Regulatory Risks: Organizations must discover info privateness and cybersecurity guidelines. Legal sanctions and buyer distrust may per chance presumably perhaps arrive from noncompliance.
Third-Occasion issues: Third-occasion distributors and repair providers can lengthen security issues for organizations. These third parties must meet excessive security requirements.
Some distance-off Work Security: Security of faraway connections and equipment start air the workplace is major as faraway work grows.
Social Engineering: It entails tricking folks into disclosing deepest info or compromising community security. Workers need social engineering consciousness and response training.
Zero-Day Exploits: These assaults purpose plan or hardware vulnerabilities earlier than the developer fixes them. They’re complex to present protection to against since they are unknown.
APTs: Long-term, focused cyberattacks wherein an attacker will get community win exact of entry to and goes undiscovered. Complex APTs build a matter to classy defenses.
Network Security Checklist With Guaranteeing Sturdy Security
Network Infrastructure Security:
1.1 Firewall Configuration:
- Be definite firewalls are accurately configured to restrict unauthorized win exact of entry to.
- Configure default grunt guidelines and permit simplest major web site visitors.
- Frequently replace firewall firmware and security insurance policies.
1.2 Intrusion Detection and Prevention Programs (IDPS):
- Deploy IDPS to detect and end malicious actions.
- Always video display community web site visitors for suspicious behavior and rob on the spot poke.
1.3 Virtual Non-public Networks (VPNs):
- Make use of VPNs to place stable connections between faraway areas.
- Encrypt info transmission to present protection to against eavesdropping.
1.4 Wireless Network Security:
- Switch default passwords and enforce sturdy encryption protocols (e.g., WPA2 or WPA3).
- Allow MAC to deal with filtering and disable SSID broadcasting.
- Frequently replace firmware for wireless win exact of entry to aspects.
Gather admission to Alter Measures:
2.1 User Authentication:
- Put into effect sturdy password insurance policies (e.g., minimum length, complexity requirements, traditional password changes).
- Allow multi-factor authentication (MFA) for added security.
- Disable default accounts and enforce story lockouts after failed login makes an attempt
2.2 Privileged Fable Administration:
- Prohibit win exact of entry to to privileged accounts.
- Frequently evaluation and replace win exact of entry to rights in step with job roles and responsibilities.
- Put into effect session monitoring and logging for privileged accounts.
2.3 Feature-Basically based Gather admission to Alter (RBAC):
- Assign win exact of entry to rights in step with job roles.
- Review and replace win exact of entry to permissions on a normal foundation.
- Get rid of win exact of entry to rights promptly for terminated workers.
Recordsdata Security and Encryption:
3.1 Recordsdata Classification:
- Classify info in step with its sensitivity level (e.g., confidential, internal, public).
- Put into effect acceptable security controls in step with classification.
3.2 Recordsdata Encryption:
- Encrypt sensitive info at relaxation and for the duration of transit.
- Profit from sturdy encryption algorithms (e.g., AES-256) and stable serious management practices.
3.3 Backup and Wretchedness Recovery:
- Frequently aid up serious info and take a look at restoration processes.
- Store backups offsite or in stable cloud environments.
- Form and doc a complete pain restoration belief.
Network Monitoring and Incident Response:
4.1 Log Administration and Prognosis:
- Allow logging for community units and serious methods.
- Put into effect log evaluation tools to identify security incidents promptly.
- Shield logs for an appropriate duration as per trusty and compliance requirements.
4.2 Security Recordsdata and Match Administration (SIEM):
- Deploy a SIEM resolution for trusty-time monitoring and correlation of security events.
- Account for alert thresholds and automatic responses for ambiance friendly incident response.
4.3 Incident Response Realizing:
- Form a documented incident response belief that entails clear roles and responsibilities.
- Frequently take a look at and replace the belief to make definite effectiveness.
4.4 Security Awareness and Training:
- Behavior traditional security consciousness training for workers.
- Educate customers about phishing assaults, social engineering, and safe taking a stumble on practices.
Network Security Policies
Account for a Network Security Policy:
- The vital step in securing your community is to clarify a community security policy.
- This policy must clearly instruct what is anticipated of all workers and the effects for violating these insurance policies.
- The policy must also clarify the protection features that will likely be build in position to present protection to the community.
Examples of security insurance policies encompass:
- Password Policy: This policy must clarify the foundations for constructing and utilizing passwords, akin to minimum length, complexity requirements, and password expiration.
- Gather admission to Alter Policy: This policy must clarify who has win exact of entry to to what info and resources and how that win exact of entry to is granted.
- Acceptable Use Policy: This policy must clarify what is and is now not any longer allowed on the firm community, akin to personal use, downloading unauthorized plan, and gaining access to uninteresting inform.
Behavior In fashion Security Audits:
In fashion security audits are wanted for figuring out doable vulnerabilities in the community.
These audits must be performed internally and externally, including reviewing all community units and functions.
Examples of security audits encompass:
- Vulnerability Scans: These scans take a look at for vulnerabilities in the community that hackers may per chance presumably perhaps exploit.
- Penetration Testing: This take a look at entails simulating a trusty-world attack on the community to identify weaknesses.
- Security Evaluation: This evaluation gives an clarify of the novel instruct of the networkâs security and identifies areas that need enhance.
Install and Configure Firewalls:
Firewalls are an wanted factor of community security. They’re designed to video display and filter incoming and outgoing web site visitors to end unauthorized win exact of entry to to the community.
Firewalls may per chance presumably perhaps be hardware or plan-based and may per chance presumably be configured to block all pointless web site visitors. Examples of firewall configurations encompass:
- Port Blocking off: This entails blocking web site visitors to explicit ports which may per chance presumably perhaps be no longer wished for the operation of the community.
- IP Deal with Blocking off: This entails blocking web site visitors from explicit IP addresses or ranges of IP addresses known to be malicious.
- Stateful Inspection: This entails monitoring the instruct of community connections to make definite that simplest approved web site visitors is allowed.
Put into effect Intrusion Detection and Prevention Programs:
Intrusion Detection and Prevention Programs (IDPS) are designed to detect and end unauthorized win exact of entry to to the community.
They’re often hardware or plan-based and may per chance presumably be configured to alert administrators if suspicious job is detected.
Examples of IDPS configurations encompass:
- Signature-Basically based Detection: This entails evaluating community web site visitors to a database of known attack signatures.
- Anomaly-Basically based Detection: This entails evaluating community web site visitors to a baseline of serene job to detect any unparalleled behavior.
- Behavioral Prognosis: This entails monitoring person behavior to identify doable insider threats.
Stable Wireless Networks:
Wireless networks are namely at likelihood of assaults, as they are often left unsecured. To stable wireless networks, companies must:
- Use WPA2 or WPA3 Encryption: This ensures that info transmitted over the community is encrypted and stable.
- Switch Default Settings: Default settings on wireless units are often shrinking, so it’s wanted to commerce them to something extra stable.
- Use Tough Passwords: Tough passwords must be oldschool to end unauthorized win exact of entry to to the community.
Complete Network Security Checklist: Defending Your Digital Infrastructure
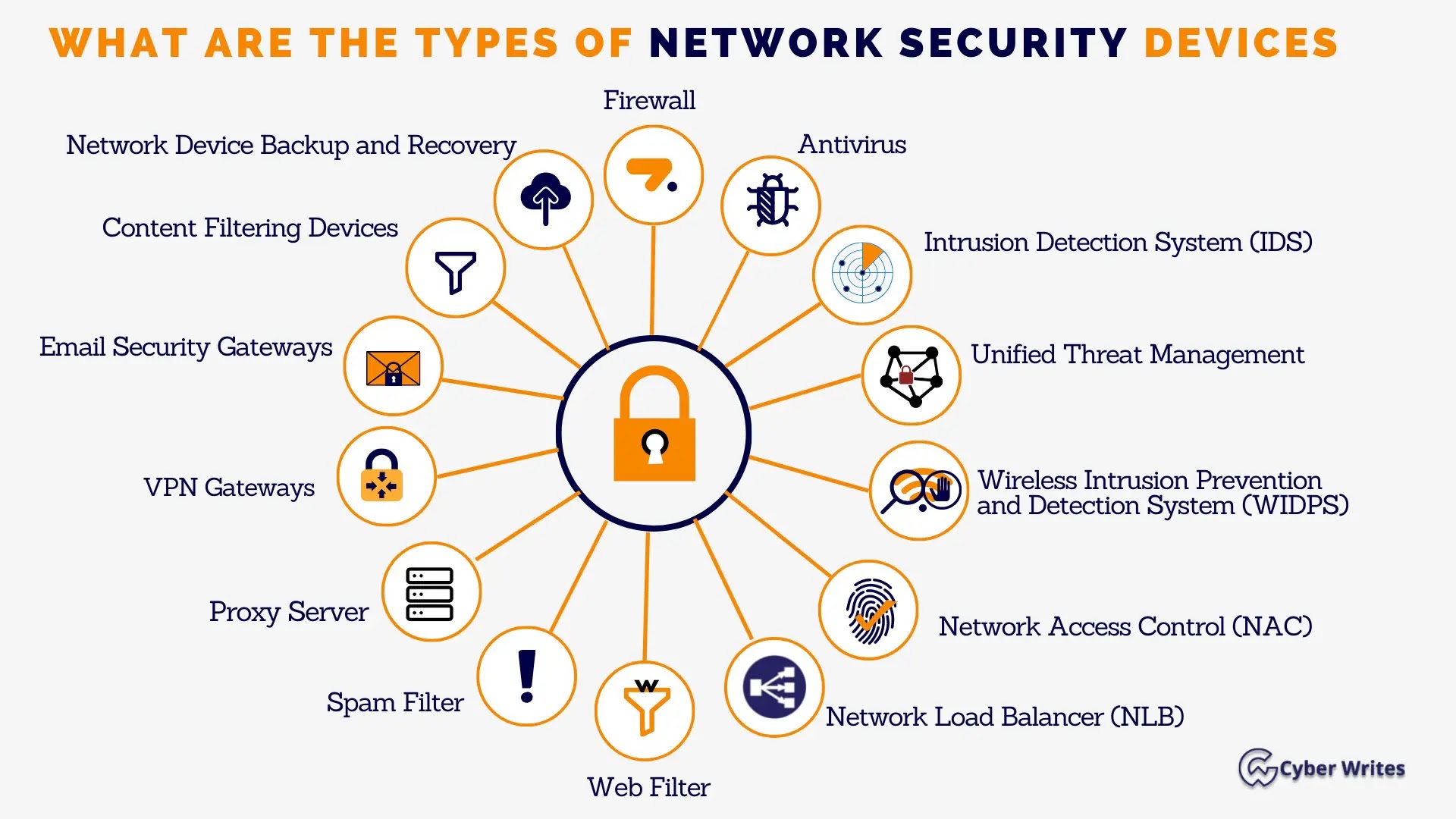
In lately’s interconnected world, community security is major in safeguarding sensitive info and preserving digital resources.
A complete community security checklist is major to make definite your community’s integrity, confidentiality, and availability.
This text will present an extensive checklist of community security features and relevant examples to imply you may presumably perhaps also make stronger your digital infrastructure.
Gather admission to Alter:
1.1 Put into effect sturdy person authentication mechanisms, akin to multifactor authentication (MFA), to end unauthorized win exact of entry to. Instance: Require workers to use a combination of passwords and biometric authentication (e.g., fingerprints or facial recognition) to win exact of entry to serious methods.
1.2 Do in force the theorem of least privilege (PoLP), granting customers simplest the major permissions to style their initiatives. Instance: Restrict person win exact of entry to to sensitive info by implementing role-based win exact of entry to management (RBAC), guaranteeing that every person has the minimum required privileges.
1.3 Frequently evaluation and replace win exact of entry to privileges, revoking win exact of entry to for workers who absorb changed roles or left the organization. Instance: Behavior periodic audits to substantiate that dilapidated workers or contractors can now no longer win exact of entry to serious methods.
Network Infrastructure Security:
2.1 Retain community units (routers, switches, firewalls) as a lot as this point with the latest firmware and security patches. Instance: Frequently take a look at for dealer updates and promptly discover them to deal with known vulnerabilities.
2.2 Put into effect community segmentation to isolate sensitive methods from much less stable areas and restrict the functionality affect of a breach. Instance: Separate the finance division’s community from the traditional employee community to gash the likelihood of unauthorized win exact of entry to to financial info.
2.3 Deploy intrusion detection and prevention methods (IDS/IPS) to video display community web site visitors and detect and block malicious job. Instance: House up an IPS to detect and end known attack patterns, akin to denial-of-carrier (DoS) assaults or SQL injections.
Recordsdata Security:
3.1 Encrypt sensitive info at relaxation and in transit to end unauthorized win exact of entry to. Instance: Use Stable Sockets Layer (SSL)/Transport Layer Security (TLS) certificates to encrypt info transmitted over the fetch, akin to login credentials or financial info.
3.2 Frequently aid up serious info and verify the integrity of backups to make definite snappy restoration in case of info loss or system compromise. Instance: Comprise day after day or weekly backups of wanted info to a stable offsite location and periodically take a look at the restoration job.
3.3 Put into effect info loss prevention (DLP) mechanisms to video display and management the poke of sensitive info. Instance: Configure DLP plan to detect and block the transmission of sensitive info, akin to bank card numbers or social security numbers, by capability of email or removable storage units.
Endpoint Security:
4.1 Put into effect sturdy endpoint security plan akin to antivirus and anti-malware solutions on all endpoints (computers, laptops, mobile units). Instance: Install respectable antivirus plan that customarily updates its virus definition database and performs trusty-time scanning to detect and rob away malware.
4.2 Do in force strict patch management practices to protect working methods and functions up to this point with the latest security patches. For instance, configure methods to download and install security updates promptly and robotically address vulnerabilities.
4.3 Educate workers about social engineering assaults and phishing scams to gash aid the likelihood of unauthorized win exact of entry to by capability of compromised endpoints. Instance: Behavior traditional security consciousness training classes to educate workers to acknowledge and file suspicious emails or phone calls.
Monitoring and Incident Response:
5.1 Put into effect a security info and tournament management (SIEM) system to amass and analyze logs from various community units and methods.
Instance: Use a SIEM tool to correlate events from firewalls, intrusion detection methods, and servers, enabling early detection of security incidents.
Conclusion
Enforcing a complete community security checklist is major to preserving your organization’s community infrastructure and info from evolving threats.
By following the pointers outlined above and adapting them to your explicit ambiance, you may presumably perhaps also place sturdy security features and mitigate doable vulnerabilities.
Have in mind, community security is an ongoing job, requiring traditional assessments, updates, and a proactive capability.
Source credit : cybersecuritynews.com





