New Fake E-Shopping Attack Hijacking Users Banking Credentials
A unfaithful e-shop rip-off advertising and marketing and marketing campaign has been focusing on Southeast Asia since 2021, as CRIL observed a surge in job in September 2022, with the advertising and marketing and marketing campaign expanding from Malaysia to Vietnam and Myanmar.
The attackers exhaust phishing net sites to distribute a malicious APK (Android application kit), which steals client credentials by SMS and may perchance now additionally take screenshots and affect the most of accessibility services and products on the victim’s gadget, giving the attackers extra preserve watch over.

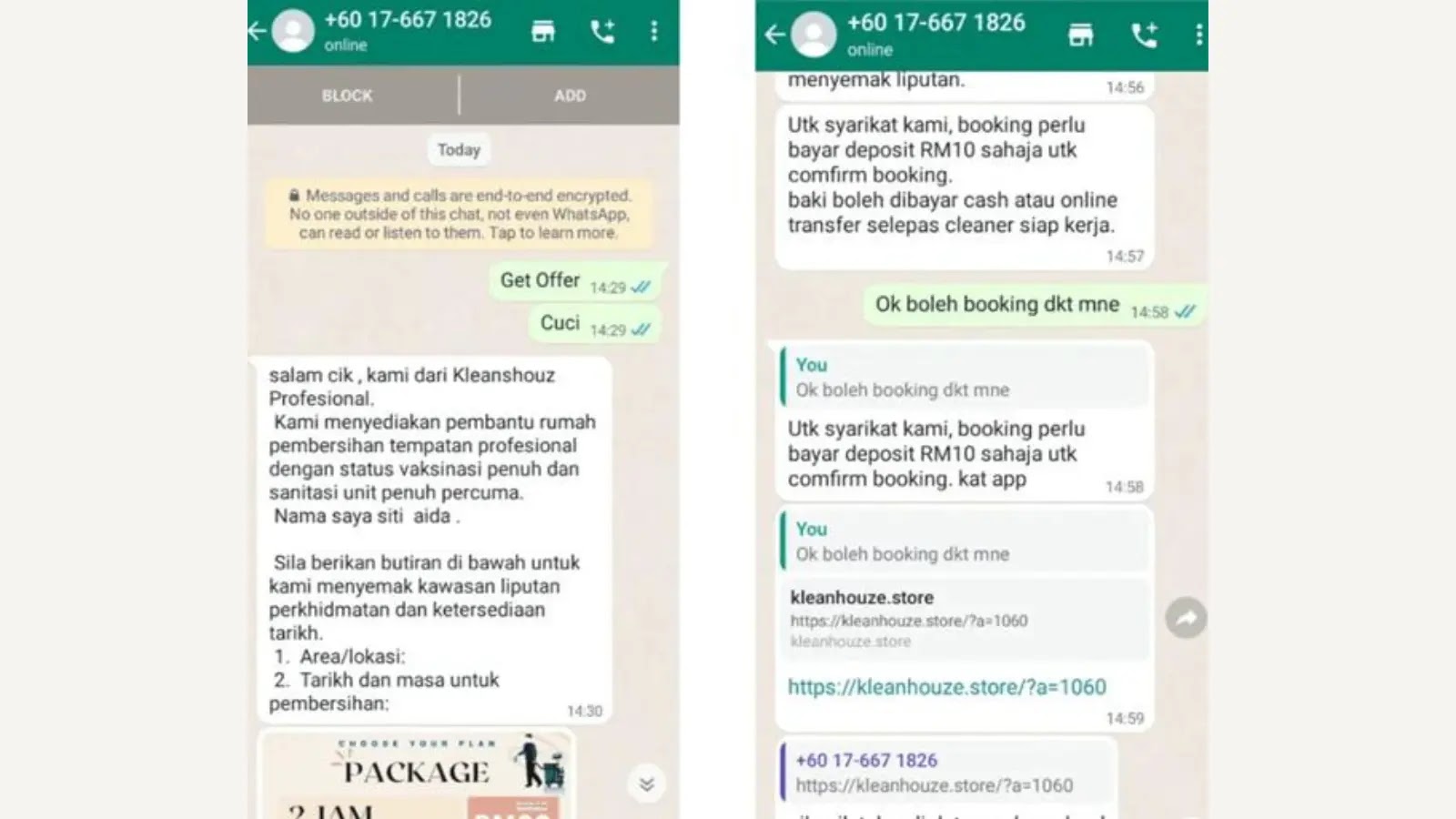
Cybercriminals have launched a unfaithful e-shop advertising and marketing and marketing campaign in Malaysia since 2021 by impersonating cleansing services and products on social media, tricking victims into contacting them by job of WhatsApp.

It led users to download malicious APKs by phishing net sites.
The malware particularly focused login credentials for Malaysian banks, alongside side Hong Leong, CIMB, Maybank, and others, demonstrating a rising style of social engineering ways blended with phishing assaults to take banking knowledge.
AI-Powered Protection for Replace Email Safety
Trustifi’s Evolved probability safety prevents the widest spectrum of sophisticated assaults earlier than they reach a client’s mailbox. Strive Trustifi Free Threat Scan with Subtle AI-Powered Email Protection .
A unfaithful e-shop advertising and marketing and marketing campaign observed by Cyble has been expanding its operations throughout Southeast Asia, where attackers exhaust phishing net sites disguised as authentic fee gateways to distribute malware.

The malware then delivers unfaithful login pages designed to take bank credentials; in Vietnam, the advertising and marketing and marketing campaign focused HD Financial institution possibilities with a net-based situation mimicking the bank’s online portal.

They additionally historic a remark and preserve watch over server to preserve watch over the malicious operation, as in Myanmar, the advertising and marketing and marketing campaign historic a the same tactic but focused more than just a few banks and employed a Burmese language phishing net page.
A brand contemporary wave of phishing net sites focusing on Malaysian online purchasers has been identified by mimicking authentic e-commerce platforms that lack sophistication and provide excellent classic capabilities and unfaithful iOS download buttons.

The malware within the succor of the rip-off has additionally been updated, incorporating capabilities treasure hide sharing and exploiting accessibility services and products to take client data.
Essentially the most modern version targets 18 Malaysian banks and makes use of two URLs, one for phishing and preserve watch over and one other for hide sharing.
Technical Important points:
eCart malware disguises itself as a shopping app but is designed to take client data. Upon installation, it requests accessibility permission to electrify computerized clicks and gestures.

It then communicates with a ways-off servers to provoke hide sharing and ship logs, utilizing the Janus plugin to manipulate gestures and obfuscate strings with Paranoid to hinder diagnosis.

It attempts to replace the default SMS app and be triumphant in hide capture permissions where hide sharing wasn’t purposeful on account of misconfiguration; its inclusion suggests the malware’s capacity for extra sophisticated assaults.
The malware advertising and marketing and marketing campaign uses unfaithful e-shops to trick users into logging in with stolen credentials, which then presents unfaithful products and uses a unfaithful FPX fee net page to take banking knowledge from 18 Malaysian banks.
In line with Cyble, the attackers have upped their sport by alongside side hide-sharing and exploiting accessibility services and products, exhibiting an effort to attract a wider viewers and take extra data.

They exhaust a phishing e-mail (T1660) containing a malicious e-shop app hyperlink (hxxps://www[.]worldshopping-global[.]com/) to be triumphant in preliminary access (TA0027).

Once place in, the malware registers broadcast receivers (T1624.001) to take incoming SMS messages (T1636.004) and inject inputs (T1516) to doubtlessly mimic client actions.
It additionally captures screenshots (T1513) the exhaust of a Janus WebRTC plugin, and exfiltrated data, alongside side SMS messages, is distributed to a remark and preserve watch over server (T1646) at hxxps://superbunapp[.]com.
The attackers additionally exhaust the same ways with a unfaithful trading application distributed by job of a obvious phishing net situation (hxxps://ecart-global[.]com).
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideSource credit : cybersecuritynews.com


