New Phishing-as-a-Service Tool Used in the Wild to Target Organizations

The cybersecurity researchers at Cisco Talos not too prolonged in the past affirmed that chance actors are concentrating on the broadly-ancient Microsoft 365 cloud-primarily based productiveness platform throughout the Greatness phishing platform, and never best likely that, even they also observed an risky surge between December 2022 and March 2023.
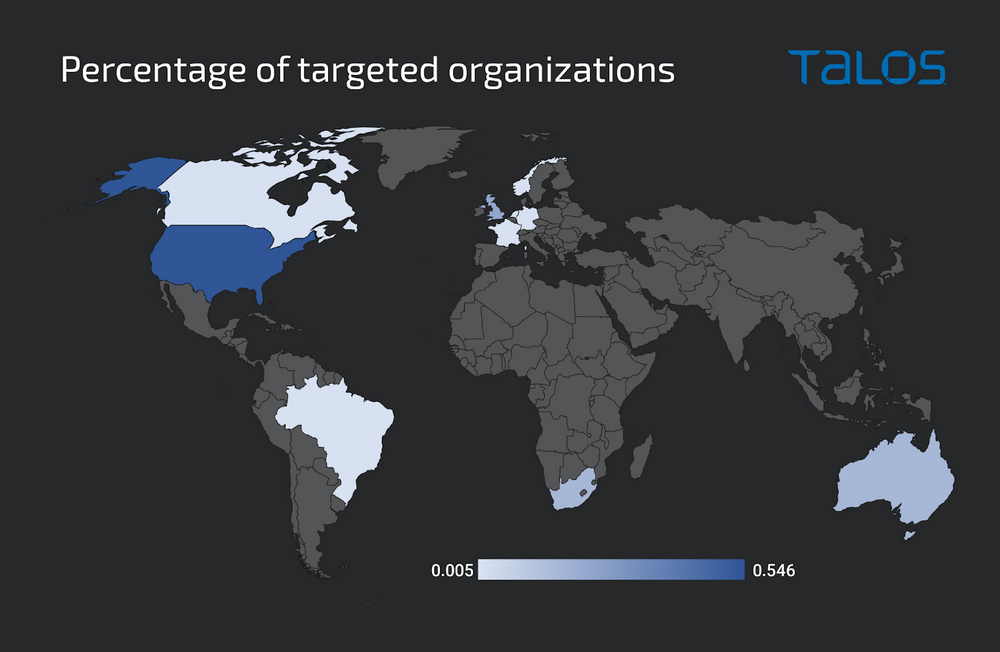
Experiencing a considerable surge in operations, the ‘Greatness’ Phishing-as-a-Service (PhaaS) platform has build its sights on organizations utilizing Microsoft 365 in the countries delight in:-
- The US
- Canada
- The U.Ample.
- Australia
- South Africa
Here below, we receive mentioned the sectors and industries from the build the victims are primarily centered, and the majority of them are positioned in the United States:-
- Manufacturing
- Healthcare
- Technology
- Training
- Precise estate
- Building
- Finance
- Trade services and products
Assault Waft of Greatness
An total Phishing-as-a-Service named “Greatness” gives the total considerable tools to successfully attain a phishing advertising and marketing and marketing campaign. Customers best likely must win admission to its admin panel through an API key and present the target e-mail checklist to open an attack.

By providing the main infrastructure, comparable to hosting the phishing page and producing the HTML attachment, the PhaaS platform empowers associates to customize e-mail content and alter default settings.
After sending a phishing e-mail with an HTML attachment, the service executes an obfuscated JavaScript code in the browser, which contacts the “Greatness” server to retrieve the phishing page.
Moreover, it injects the target company’s ticket and background image from their legit Microsoft 365 login page robotically.

After obtaining the victim’s password, the PaaS will simulate the victim’s identity to log in to Microsoft 365 and inquire of the victim to authenticate utilizing the MFA methodology specified by Microsoft 365 if enabled.
The service receives MFA and completes the login direction of to amass session cookies, that are then dropped at the affiliate through Telegram or the win panel.
In total, there are three formula that the service contains, and right here below we receive mentioned them:-
- A phishing kit
- The service API
- A Telegram bot or e-mail address
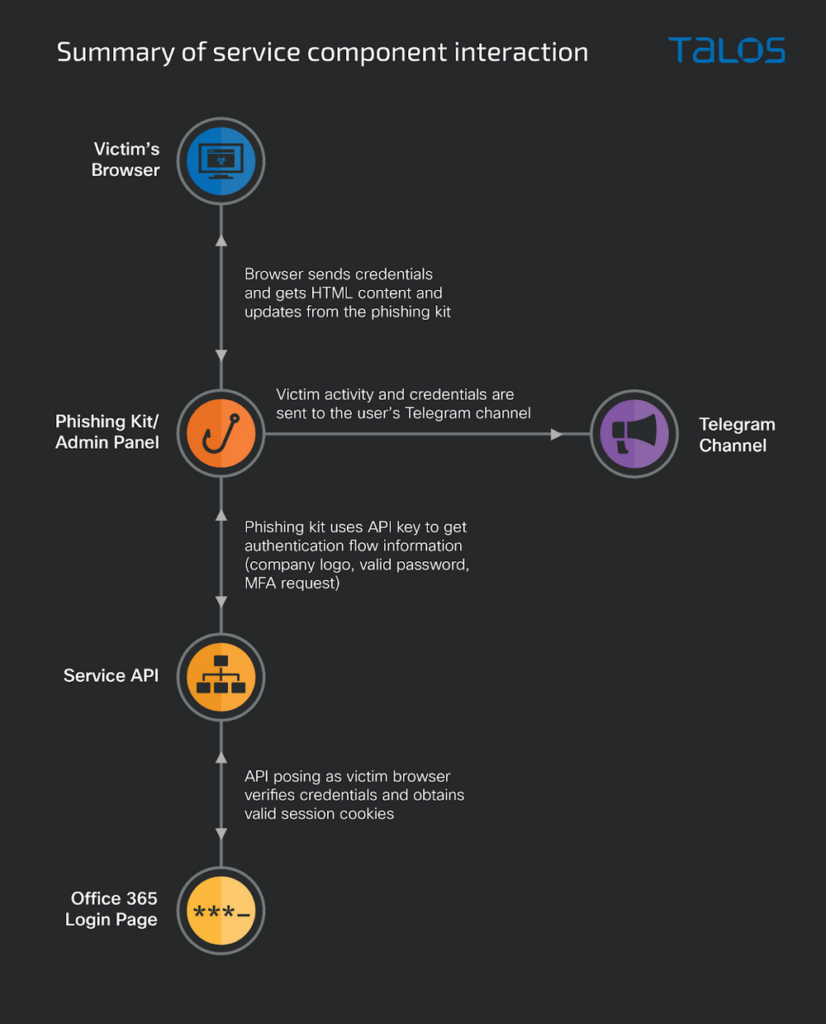
To use Greatness, associates require a sound API key, with out which the phishing page won’t load, and they’ll configure their API key in the panel.
The service API collaborates with the phishing kit to originate a “man-in-the-middle” attack by validating the affiliate’s key, blocking off unauthorized IP addresses, and facilitating seamless dialog with the negate Microsoft 365 login page, enabling the sequence of victim files in actual-time.
By exploiting the PaaS affiliate’s capability to extract usernames, passwords, and even authenticated session cookies (especially in cases of MFA utilization), the inclusion of a Telegram bot ensures swift notification of valid cookies, enabling urged win admission to for the attacker to excessive-price targets.
Moreover, the chance actors also use the stolen credentials to construct several hundreds of illicit actions delight in deploying ransomware or breaching corporate networks.
Struggling to Be aware The Security Patch in Your Machine? –
Strive All-in-One Patch Manager Plus
Source credit : cybersecuritynews.com

