Notorious State-Sponsored Hacker Group Stealthy Infrastructure Uncovered

Neighborhood-IB’s cybersecurity researchers made a indispensable discovery, revealing undisclosed assault infrastructure employed by the extremely filled with life snarl-backed workers SideWinder. Their targets primarily encompassed entities positioned in:-
- Pakistan
- China
In a collaborative describe, cybersecurity firms Neighborhood-IB and Bridewell disclosed the existence of a comprehensive network consisting of 55 domains and IP addresses exploited by the malicious actor.
Whereas the phishing domains that the researchers title mimic many organizations from diversified sectors, alongside side the next:-
- News
- Government
- Telecommunications
- Monetary
SideWinder Say-Sponsored Hacker Neighborhood
Working since 2012, SideWinder is a lengthy-standing probability actor identified for its power stammer. Their assault suggestions closely rely on spear-phishing suggestions to compose unauthorized discover entry to to targeted techniques.
SideWinder effectively establishes a foothold within the specified environments by employing spear-phishing as a predominant intrusion system.
The workers’s scheme fluctuate is widely connected with espionage activities linked to India’s pursuits, indicating a obtain connection.
Centered Countries
Here beneath, we now enjoy mentioned the entire countries that the operators of this APT workers veritably scheme:-
- Pakistan
- China
- Sri Lanka
- Afghanistan
- Bangladesh
- Myanmar
- Philippines
- Qatar
- Singapore
Infrastructre of SideWinder Hacker Neighborhood
In February of this year, Neighborhood-IB printed compelling proof pointing towards SideWinder’s probably involvement in focused on over 61 organizations in Asia.
The affected entities encompassed authorities, militia, law enforcement, and diversified other sectors. The timeframe for these assaults spanned from June to November 2021, highlighting the extent and period of SideWinder’s advertising and marketing and marketing campaign.

Whereas fair not too lengthy ago, it has been observed that SideWinder evasively attacked Pakistani authorities organizations by the stammer of server-primarily based mostly polymorphism.
In the next worldwide locations, the authorities organizations were mimicked by the domains that were identified fair not too lengthy ago:-
- Pakistan
- China
- India
The WHOIS records of all these domains present an identical values with registration crucial points. These domains possess fraudulent authorities-themed files aimed towards downloading a subsequent undisclosed payload.
These originate of files originating from Pakistan were uploaded to VirusTotal in March 2023. One amongst the files is a Microsoft Discover file allegedly originating from the Pakistan Navy Battle College (PNWC).

In slack November 2022, a Windows shortcut (LNK) file was as soon as chanced on and uploaded to VirusTotal from Beijing.
The LNK file is designed to assemble an HTA file from a remote server, impersonating the electronic mail gadget of Tsinghua University. It serves the reason of running an HTML application.
It has been chanced on that SideWinder’s infrastructure is laced with a malicious Android APK file (226617) chanced on right thru the additional investigation and disguised as “Ludo Game.”
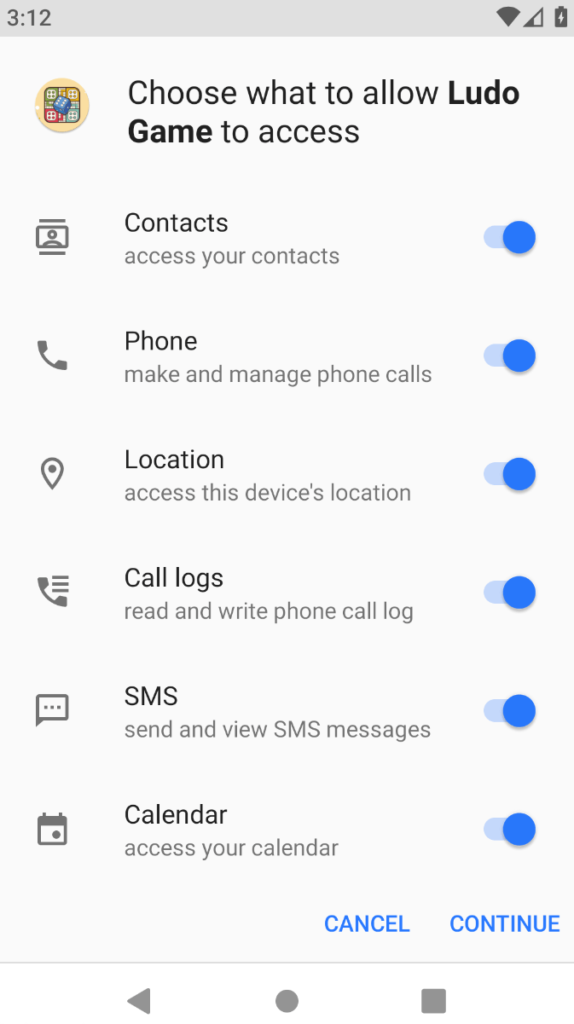
Upon successful set up of this malicious app, it asks customers for the next discover entry to on their instrument:-
- Contacts
- Build
- Phone logs
- SMS messages
- Calendar
Chance actors may maybe per chance without problems show screen the instrument and harvest aesthetic user knowledge by gaining discover entry to to such permissions on the Android instrument.
Organizations ought to easy prioritize enforcing industrial electronic mail protection solutions to counter SideWinder’s reliance on targeted spear-phishing effectively.
The stammer of probability intelligence solutions proves to be a more perfect system to enhancing indicators of compromise and staying told about pertinent threats.
By deploying such solutions, organizations can effectively safeguard their techniques and networks from the preliminary vectors employed by SideWinder.
Source credit : cybersecuritynews.com

