NSA and CISA Shared Best Practices To Harden CI/CD Cloud Deployments

Launched by the Nationwide Security Company (NSA) and the Cybersecurity and Infrastructure Security Company (CISA), the cybersecurity files sheet (CSI) titled “Defending Accurate Integration/Accurate Provide (CI/CD) Environments” supplies suggestions and most productive practices for bettering defenses in cloud implementations of pattern, security, and operations (DevSecOps).
Securing a CI/CD ambiance critically depends on being responsive to the many security threats that would per chance per chance per chance impact operations and taking motion to protect in opposition to everyone.
The CI/CD environments and application supply chains are prime targets for cybercriminals, as proven by the rising selection of intrusions over time.
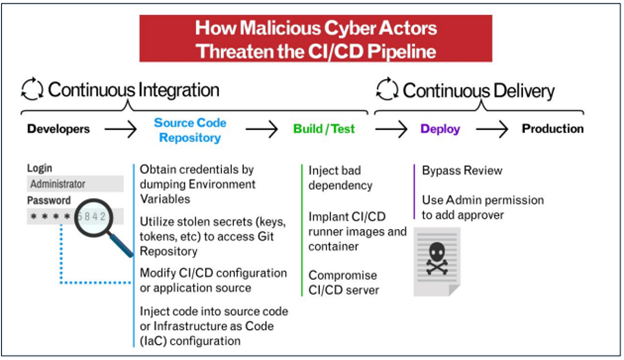
CI/CD Environments – In model Targets
The Accurate Integration/Accurate Provide (CI/CD) pattern potential helps organizations retain a relentless application code contaminated while dynamically merging code modifications. It permits for rapid construction and attempting out of code modifications.
The (DevSecOps) mannequin, which contains security and automation all the intention in which by intention of the come lifecycle, entails CI/CD as a essential component.
As a result of cloud’s importance to IT modernization initiatives, CI/CD pipelines are steadily deployed in commercial cloud settings.
Suggestions To Stable CI/CD Environments
- Exercise NSA-Instructed Cryptography
When designing cloud apps and services, the NSA and CISA expose the utilization of powerful cryptographic algorithms and configuration.
The protection of files, alternate secrets and tactics, application programming interfaces (APIs), and keys created across the CI/CD pipeline is enhanced by the merely implementation and setup of these tactics.
- Minimize the utilization of prolonged-duration of time credentials
When it’s practicable, employ sturdy credentials that resist being stolen, phished, guessed, and replayed. Exercise identification federation and phishing-resistant security tokens to salvage non everlasting SSH and other keys at any time when human authentication is required.
- Add signature to CI/CD configuration and test it
Stable code signing is knowledgeable by the NSA and CISA to assemble digital self belief interior the CI/CD pipeline.
No matter the extent of pattern, assemble that code is constantly and accurately signed, and the signature is checked.
If the signature can no longer be validated, behold into what’s going to be causing it. It would per chance per chance per chance also merely be a straightforward environment downside or a designate of a bigger breach.
- Make primarily the most of two-person guidelines (2PR) for all code updates
A single developer shouldn’t study in code with out first being reviewed and popular by every other developer.
This notice improves code quality in identical old and makes it considerably less possible that malicious code will possible be efficiently checked in if a single developer’s credentials are compromised.
- Put in force least-privilege policies for CI/CD salvage entry to
Everybody in the firm win no longer want salvage entry to to the CI/CD pipeline.
Workers have to most productive be granted restricted salvage entry to with certain credentials upon quiz fairly than being given salvage entry to to all pipelines automatically.
Simplest the pipelines and elements they are altering desires to be accessible to developers. Also, enforce multi-component authentication (MFA) to sever the hazards linked to passwords.
- Stable person accounts
Audit administrative person accounts again and again and sets up salvage entry to limits the utilization of the least privilege and separation of responsibilities concepts. audit records to verify the legitimacy of novel accounts.
- Stable secrets and tactics
In a CI/CD pipeline, it is essential to take care of secrets and tactics, tokens, and other credentials securely.
Certainly no longer send confidential files across a pipeline in plaintext.
Make sure that confidential files is beneath no circumstances left in application that would per chance per chance also merely be reverse-engineered, such as passwords and non-public keys.
- Put in force network segmentation and traffic filtering
To pause the spread of malware and restrict salvage entry to from other parts of the network that elevate out no longer require salvage entry to, enforce and enforce efficient network segmentation across networks and services.
It is urged to place a demilitarized zone to pause unchecked network connectivity.
Filter network traffic to pause communications from known malicious IP addresses coming into or leaving the network.
Closing Thoughts
“The organizations have to enforce the proposed mitigations to harden their CI/CD environments and bolster organizational DevSecOps”, recommends NSA and CISA.
By imposing the proposed mitigations, organizations can sever the selection of exploitation vectors of their CI/CD environments and assemble a provocative ambiance for the adversary to penetrate”.
Which potential that truth, to protect and harden the CI/CD assault ground, protect malicious actors out by applying the next concepts.
Here’s essential to retain a powerful cybersecurity posture for the Department of Defence (DoD), the Defence Industrial Atrocious (DIB), the federal, convey, native, tribal, and territorial (SLTT) administrations, besides to homeowners of non-public sector files methods.
Source credit : cybersecuritynews.com


