OpenCTI With ANY.RUN: OSINT Platform to SOC & MDR Teams for Malware Analysis
OpenCTI With ANY.RUN: OSINT Platform to SOC & MDR Groups for Malware Analysis
ANY.RUN integrates with OpenCTI to streamline threat diagnosis, which permits enriching OpenCTI observations with recordsdata without delay from ANY.RUN diagnosis.
OpenCTI is a central hub that collects threat recordsdata from a range of sources, cherish ANY.RUN, via connectors, stores this recordsdata as “observations,” at the side of indicators cherish file hashes and IP addresses.
ANY.RUN is a cloud-based completely mostly malware diagnosis sandbox that assists security teams in investigating suspicious recordsdata that makes use of YARA and Suricata principles for initial detection interior 40 seconds and offers real-time interplay with the virtual atmosphere.
It permits analysts to circumvent automatic malware systems and delve deeper into analyzing sophisticated threats and its cloud-based completely mostly nature additionally eliminates setup and repairs burdens for security teams.
“ANY.RUN released connectors for MITRE ATT&CK systems and ways, an ANY.RUN TI Feeds connector that imports recordsdata into OpenCTI as soon as every 24 hours, and an ANY.RUN sandbox connector that which that you can maybe maybe presumably spend to counterpoint observations with recordsdata from sandbox diagnosis tasks, cherish malware household labels and maliciousness rankings.”
The novel integration offers two well-known functionalities:
- Computerized recordsdata import: ANY.RUN Possibility Intelligence Feeds connector automatically imports recordsdata into OpenCTI on daily basis.
- Interactive diagnosis and enrichment: Its sandbox connector permits enriching observations with recordsdata from malware execution in a sandbox atmosphere that involves malware labels, malicious rankings, and indicators cherish ways, systems, and procedures (TTPs) mature by the malware.
This integration combines and analyzes recordsdata from varied sources to present SOCs and MDR teams with a centralized platform for faster and extra comprehensive threat diagnosis.
Mix ANY.RUN in Your Company for Efficient Malware Analysis
Are you from SOC, Possibility Study, or DFIR departments? If that is the case, which that you can maybe maybe presumably be a part of an on-line neighborhood of 400,000 just security researchers:
- Accurate-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Crew contributors
- Secure detailed reviews with most recordsdata
- Negate Up Digital Machine in Linux & all Home windows OS Variations
- Work alongside with Malware Safely
Can delight in to that that you must take a look at all these facets now with free of fee get entry to to the sandbox:
ANY.RUN enrichment connector in OpenCTI
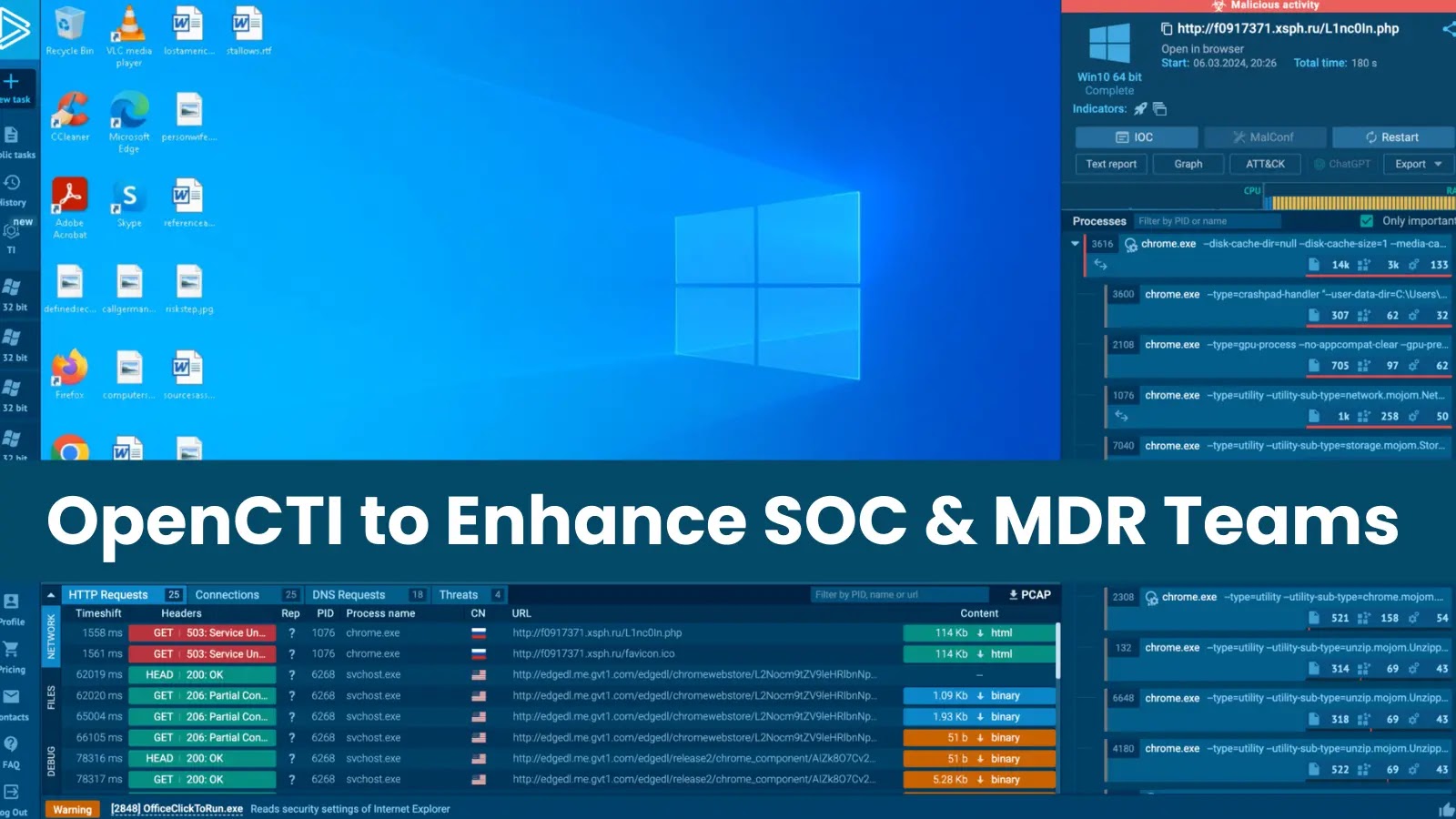
An OpenCTI observation could maybe additionally additionally be transformed exact into a fats-fledged indicator by leveraging the ANY.RUN sandbox connector. This entails submitting the observation to ANY.RUN and increasing a virtual machine to analyze the artifact’s behavior.
For the interval of this diagnosis, ANY.RUN extracts Indicators of Compromise (IOCs) from network traffic, memory dumps, and seen activity, then hyperlinks support to the true observation interior OpenCTI, enriching it with precious threat recordsdata.
The observation, now a hallmark encumbered with particulars, could maybe additionally additionally be forwarded to the SIEM or SOAR intention, which triggers the introduction of an incident label, prompting extra investigation by security responders.
The person targets to counterpoint an observable (indicator) interior the OpenCTI platform, navigates to the list of observables, and selects one by observing the empty malware diagnosis particulars and references they establish to leverage an enrichment connector.
Performance could maybe additionally additionally be accessed via a button on the head honest corner, permits fetching extra recordsdata from external sources, potentially at the side of malware diagnosis reviews and linked references.
The ANY.RUN enrichment connector automatically retrieves details a few supplied observable (e.g., URL, IP tackle) and enhances its recordsdata with extra particulars.
Clicking the refresh button triggers the connector to work within the background and can place connections between the observable and recognized ways, systems, and procedures (TTPs) mature by adversaries.
Exterior references cherish sandbox tasks will most definitely be identified, taking beneath consideration extra investigation by clicking the corresponding link and this job is launched in ANY.RUN.
What’s ANY.RUN?
ANY.RUN is a cloud-based completely mostly malware lab that does quite heaps of the work for security teams. 400,000 mavens spend ANY.RUN platform each day to peep into events and jog up threat analysis on Linux and Home windows cloud VMs.
Advantages of ANY.RUN
- Accurate-time Detection: ANY.RUN can obtain malware and without delay name many malware households the spend of YARA and Suricata principles interior about 40 seconds of posting a file.
- Interactive Malware Analysis: ANY.RUN differs from many automatic alternatives on fable of it lets you connect with the virtual machine from your browser. This are living fair helps cease zero-day vulnerabilities and developed malware that can get previous signature-based completely mostly safety.
- Price for money: ANY.RUN’s cloud-based completely mostly nature makes it a imprint-efficient option for companies since your DevOps crew doesn’t must enact any setup or make stronger work.
- Easiest for onboarding novel security crew contributors: ANY. RUN’s easy-to-spend interface permits even novel SOC researchers to instant be taught to look for malware and name signs of compromise (IOCs).
Are you from SOC and DFIR Groups? â Analyse Malware Incidents & get are living Secure admission to with ANY.RUN -> Open Now for Free
Source credit : cybersecuritynews.com