OrBit – Undetected Linux Malware Uses Unseen Hijack Method to Attack Linux Systems

Servers and cloud computing infrastructures are assuredly powered by Linux, a preferred working gadget. And these days a brand fresh and fully undetected Linux threat assuredly called OrBit has been discovered by cyber security researchers at Intezer.
It is a long way feasible to install it either as a chronic implant or as a unstable implant, reckoning on its desires. By hooking key good points on the computer, the malware employs developed evasion systems. Among the aspects offered to threat actors are:-
- A long way-off pick up entry to capabilities over SSH
- Harvests credentials
- Logs TTY commands
Right here’s the point at which any running processes on the machine, including fresh processes which possess been began, will be contaminated by the malware as soon as it has been installed.
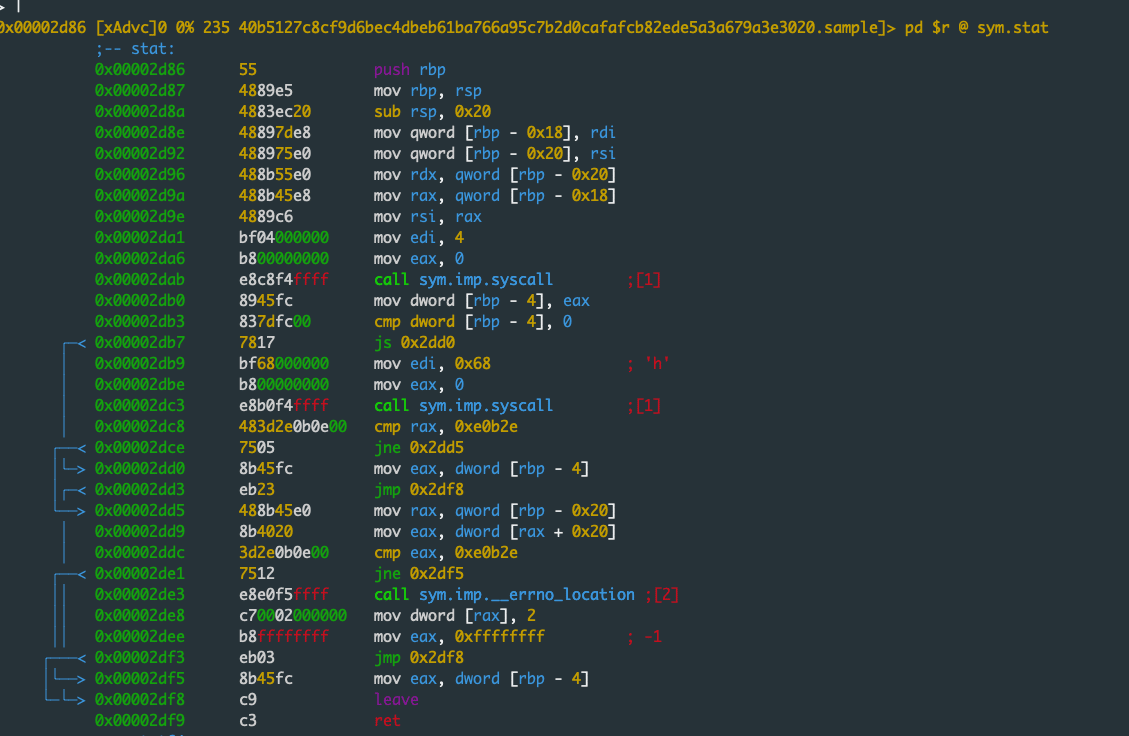
Technical Analysis
There are two ways all over which this malware hundreds the malicious library, in distinction to other threats that hijack shared libraries by editing the LD_PRELOAD environment variable.
Whereas here below now we possess talked about these two ways:-
- As a first step, the shared object may possibly maybe additionally additionally be added to the configuration file.
- Secondly, to load the malicious shared object we can patch the binary of the loader.
Upon set up, the dropper creates the environment for the malware to trot in and installs the payload into the environment. In response to the arguments offered on the divulge line, it extracts the payload to the most correctly appreciated location consistent with the positioning referred to above.
In response to the represent, It is a long way feasible to swap the set up route during the divulge line arguments, apart from to to replace or uninstall the payload fully using the divulge line arguments.
Stealthy Malware
After BPFDoor, Symbiote, and Syslogk, OrBit is now identified to be the fourth Linux malware to emerge in the end of the last three months in a short timeframe.
Like Symbiote, the malware targets all processes that are running on the compromised machine in repeat to unfold. An ELF dropper file is broken-down to start up the assault chain in repeat to extract the payload file (“libdl.so”) from the server.
It is a long way mostly significant to swear that OrBit makes exhaust of several stealthy systems making sure that it’s going to characteristic without being noticed at all. As a outcome these systems, it’s in a position to making sure persistence and making the casting off of the virus from contaminated computer systems reasonably involving.
There may possibly be one thing severely attention-grabbing about this malware in that it hooks to libraries almost hermetically on the machine it’s attacking.
As a outcome, the malware can pick up chronic, evade detection, and take hang of recordsdata apart from to position up a backdoor for the SSH protocol in the formula.
Safety instruments are failing to raise up with evolving threats that are focusing on Linux, whereas concurrently staying below the radar of threats focusing on Linux.
There are many examples of a brand fresh malware that would additionally additionally be extremely evasive and chronic of their systems, and OrBit is one such instance.
IoCs
| Hash | File |
| f1612924814ac73339f777b48b0de28b716d606e142d4d3f4308ec648e3f56c8 | Dropper |
| 40b5127c8cf9d6bec4dbeb61ba766a95c7b2d0cafafcb82ede5a3a679a3e3020 | Payload |
Source credit : cybersecuritynews.com


