PayPal Bug Let Attacker to Steal PayPal Balance with One Click

A security researcher declared the discovery of an unpatched flaw in PayPal that will furthermore permit attackers to steal money from users with one click on.
Earlier, the expert reported the worm to the PayPal worm bounty program, demonstrating that attackers can steal users’ money by exploiting Clickjacking.
Clickjacking Assault
Clickjacking is furthermore acknowledged as a “UI redress attack”. When an attacker uses more than one transparent or opaque layers to trick a person into clicking on a button or hyperlink on one other website when they were desiring to click on on the tip-stage website.
In step with the expert, “The attacker is “hijacking” clicks intended for their website and routing them to 1 other website, in all likelihood owned by one other application, domain, or each and each”.
“I chanced on that an attacker can steal money from Paypal accounts, Clickjacking on https://www.paypal.com/agreements/approve”, consistent with the post revealed by the researcher.
This endpoint is intended for “Billing Agreements” and it might probably well presumably presumably restful glean only billingAgreementToken. But after the testing, it changed into chanced on that it will pass one other tokens kind, and thus results in stealing money from the sufferer’s PayPal myth.
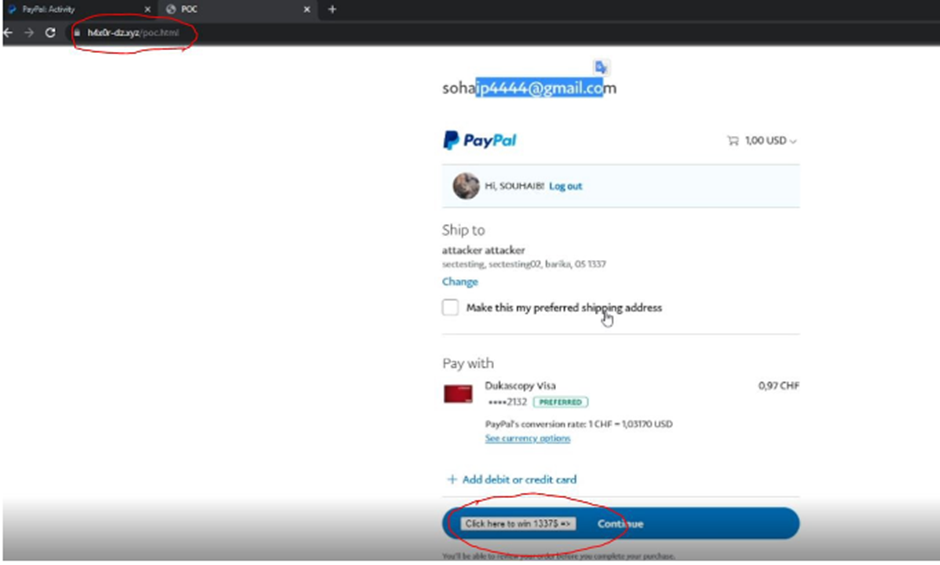
As you click on, you will send money to the attacker’s PayPal. Additionally, the attacker tackle shall be injected as the default billing.

Attacker injected billing tackle shall be the default one on the sufferer’s PayPal myth. The experts revealed a PoC exploit for this venture, which consistent with the expert has yet to be patched. “There are online companies and products that permit you in an effort to add steadiness using Paypal to your myth let’s pronounce steam! I will employ the same exploit and force the person in an effort to add money to my myth!” reads the post revealed by the researchers. “Or I will exploit this worm and let the sufferer plan/pay Netflix myth for me!”.
Source credit : cybersecuritynews.com


