Phemedrone Stealer Exploits Windows SmartScreen Flaw to Steal Sensitive Data

The cybersecurity neighborhood has no longer too lengthy in the past identified a brand contemporary threat is believed as Phemedrone Stealer, a stylish malware that exploits a vulnerability in Microsoft Home windows Defender SmartScreen, CVE-2023-36025.
This malware has been designed to rob tranquil data, including credentials from extra than one platforms and cryptocurrency wallet data.

Subtle Data Theft Tactics
Phemedrone Stealer is a . NET-compiled Trojan Stealer that employs evolved techniques to evade detection and harvest data from infected programs.
It uses a mutex checker to forestall extra than one circumstances. It applies preserve away from diagnosis by terminating processes if it detects a digital machine atmosphere or explicit languages linked with the Commonwealth of Just States (CIS).
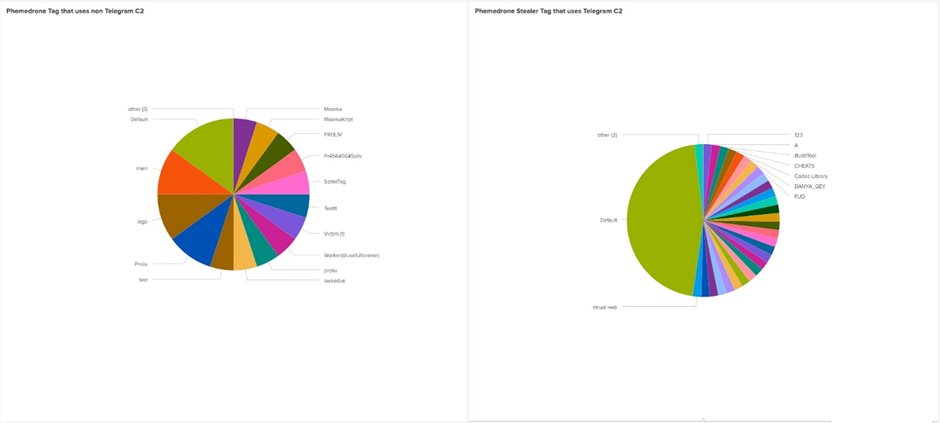
Focusing on Cryptocurrency Wallets
One in every of basically the most alarming capabilities of Phemedrone Stealer is its specialise in cryptocurrency wallets.
It targets wallets corresponding to Armory, Atomic, Bytecoin, Coinomi, Jaxx, Electrum, Exodus, and Guarda, making an try to extract tranquil data from explicit directories that retailer transaction records, story data, and cryptographic keys.
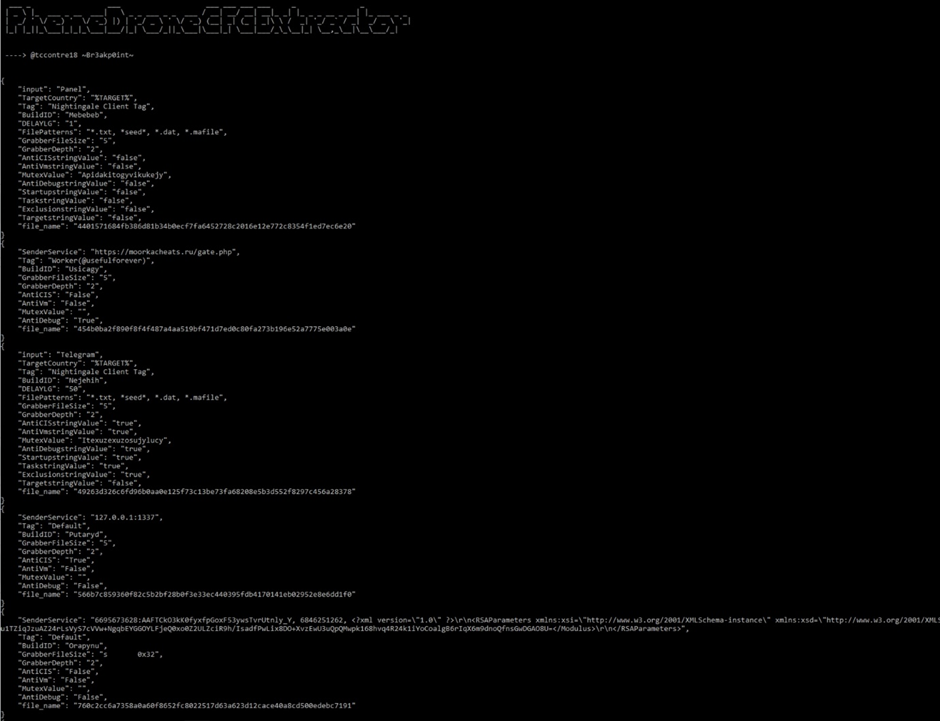
The Splunk Threat Research Team has dissected the Phemedrone Stealer, offering insights into its configuration settings and operational patterns.
Instruct and Alter Operations
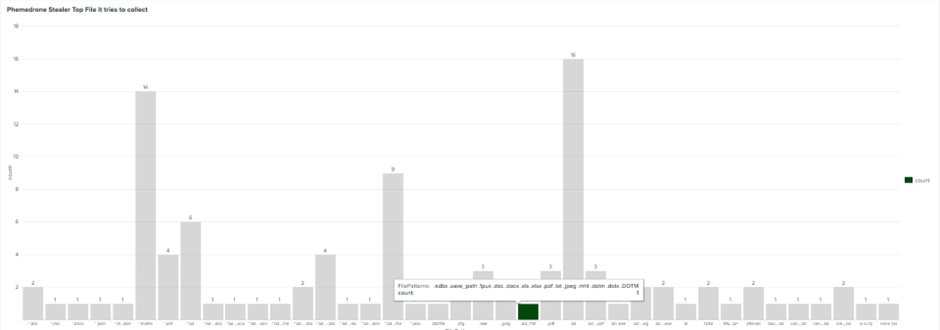
After amassing data, Phemedrone Stealer organizes it into a zipper file named in a explicit structure that contains the victim’s IP address and tantalizing user title, making it more uncomplicated for attackers to form thru the stolen data.
The C2 server then receives this organized data, including screenshots, machine data, and tranquil recordsdata from the compromised host.
Evasion and System Data Discovery
Phemedrone Stealer’s evasion techniques are particularly touching on. It assessments for digital machine identifiers and terminates if any are stumbled on.
| System Data | Technique |
| Receive AV Product Put in Data | “root\SecurityCenter2”, “SELECT * FROM AntivirusProduct” |
| Receive CPU Data | “SELECT * FROM Win32_Processor” |
| Receive Geo Data | hxxp[://]ip-api[.]com/json/?fields=11827 |
| Receive GPU | “SELECT * FROM Win32_VideoController” |
| Receive Hardware Data | “SELECT * FROM Win32_Processor” “SELECT * FROM Win32_DiskDrive” |
| Receive Total RAM | “SELECT * FROM Win32_ComputerSystem” |
| Home windows | “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Home windows NT\CurrentVersion” , “ProductName” |
Additionally, it collects detailed machine data from the infected host, including installed antivirus merchandise, CPU, GPU, and hardware data, as successfully as total RAM and Home windows product names, the utilization of WMI commands and registry parsing.
Data Sequence from Discord, Steam, and Browsers
The malware additionally targets data from applications fancy Discord and Steam, extracting story data and activities by querying explicit registry keys and file names.
It has a genuinely skilled class for extracting data from web browsers, critically Chrome, where it locates serious recordsdata to decrypt and extract saved passwords and other tranquil data.
Chrome Extensions in the Crosshairs
Phemedrone Stealer targets explicit Chrome extensions linked to second-mutter authentication, cryptocurrency management, and password management.
It collects data from these extensions and sends it lend a hand to its C2 server, doubtlessly compromising tranquil user data.
Indicators and Detection Alternatives
The Splunk Threat Research Team has dissected the Phemedrone Stealer, offering insights into its configuration settings and operational patterns.
They obtain additionally developed a Python script, phemdrone_extractor_s.py, to extract configuration data from the malware and obtain identified over 150 configuration settings linked to its campaign.
Phemedrone Stealer is a necessary threat resulting from its means to use a Home windows SmartScreen flaw and complicated data theft techniques.
Its evasion techniques, centered data collection, and organized exfiltration techniques originate it a ambitious field for cybersecurity defenses.
The cybersecurity neighborhood is actively working to impress and mitigate this threat, but customers and organizations must live vigilant and guarantee their programs are adequately right towards such refined assaults.
You might well maybe block malware, including Trojans, ransomware, spy ware, rootkits, worms, and zero-day exploits, with Perimeter81 malware safety. All are extremely defective, can wreak havoc, and harm your community.
Defend up to this point on Cybersecurity news, Whitepapers, and Infographics. Be conscious us on LinkedIn & Twitter.
Source credit : cybersecuritynews.com


